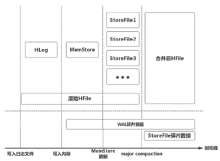
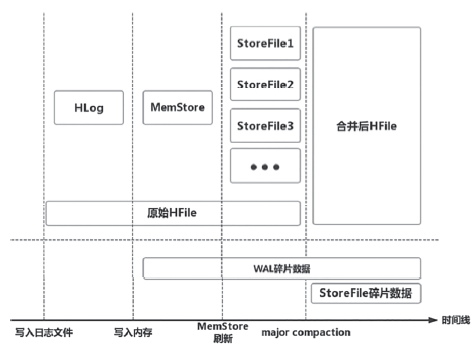
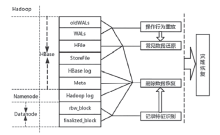
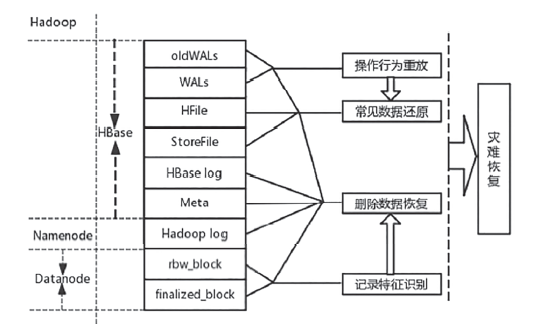
| [1] |
ALHAZMI O H,MALAIYA Y K.Evaluating Disaster Recovery Plans Using the Cloud[C]//IEEE. Reliability and Maintainability Symposium(RAMS), January 28-31,2013 , Orlando, Florida, USA.New York:IEEE,2013:37-42.
|
| [2] |
YANG Yixian, YAO Wenbin, CHEN Wei.A Comprehensive Review of Information System Disaster Recovery Technology[J]. Journal of Beijing University of Posts and Telecommunications,2010,33(2):1-6.
|
|
杨义先,姚文斌,陈钊.信息系统灾备技术综论[J].北京邮电大学学报,2010,33(2):1-6.
|
| [3] |
KHANUJA H K, ADANE D S.A Framework for Database Forensic Analysis[J]. Computer Science & Engineering: An International Journal (CSEIJ), 2012, 2(3): 27-44.
|
| [4] |
ALDHAQM A,RAZAK S A,OTHMAN S H,et al.Ngadi, Conceptual Investigation Process Model for ManagingDatabase Forensic Investigation Knowledge[J]. Sciences, Engineering and Technology, 2016, 12(4): 386-394.
|
| [5] |
CHOI J H,JEONG D W,LEE S J.The Method of Recovery for Deleted Record in Oracle Database[J]. Journal of The Korea Institute of Information Security & Cryptology(JKIISC), 2013, 23(5): 947-955.
|
| [6] |
ADEDAYO O M,OLIVIER M S.Ideal Log Setting for Database Forensics Reconstruction[J]. Digital Investigation, 2015(12): 27-40.
|
| [7] |
ZHOU Jingzhe, CHEN Changsong.Analysis of Network Information Security Countermeasures for Cloud Computing Architecture[J]. Netinfo Security, 2017, 17(11): 74-79.
|
|
周靖哲,陈长松. 云计算架构的网络信息安全对策分析[J]. 信息网络安全,2017,17(11):74-79.
|
| [8] |
YOON J S,JUNG D W,KANG C H,et al.Digital Forensic Investigation of MongoDB[J]. Journal of the Korea Institute of Information Security and Cryptology, 2014, 24(1):123-134.
|
| [9] |
CHOI J M,JUNG D W,YOON J S,et al.Digital Forensics Investigation of Redis Database[J]. KIPS Transactions on Computer and Communication Systems, 2016, 5(5):117-126.
|
| [10] |
DEAN F C,GHEMAWAT J S,HSIEH W C,et al.Gruber, Bigtable: A Distributed Storage System for Structured Data[J]. Transactions on Computer Systems, 2008, 26(2):205-218.
|
| [11] |
GAO X M,JUDY Q.Scalable Inverted Indexing on NoSQL Table Storage[D]. Indiana:School of Informatics and Computing, 2013.
|
| [12] |
CHEN Xilin,MA Ding.HBase Storage Structure Design for Weibo Information Analysis[J].Netinfo Security, 2016,16(9): 267-271.
|
|
陈希林,马丁. 针对微博信息分析的HBase存储结构设计[J]. 信息网络安全,2016,16(9):267-271.
|
| [13] |
MENG Yongwei, HUANG Jianqiang, CAO Tengfei, et al.Design and Implementation of Hadoop Cluster Deployment Experiment[J].Experimental Technology and Management,2015(1):145-149.
|
|
孟永伟,黄建强,曹腾飞,等.Hadoop集群部署实验的设计与实现[J]. 实验技术与管理,2015(1):145-149.
|
| [14] |
LUO Wenhua,WANG Jun,SUN Yuanyuan.Study on Multi-level Data Collaborative Analysis of Nodes Based on Cloud Server[J].Netinfo Security, 2018, 18(3):39-45.
|
|
罗文华,王俊,孙媛媛.基于云服务端的节点多层次数据协同分析研究[J].信息网络安全,2018,18(3):39-45.
|