Netinfo Security ›› 2020, Vol. 20 ›› Issue (5): 47-56.doi: 10.3969/j.issn.1671-1122.2020.05.006
Previous Articles Next Articles
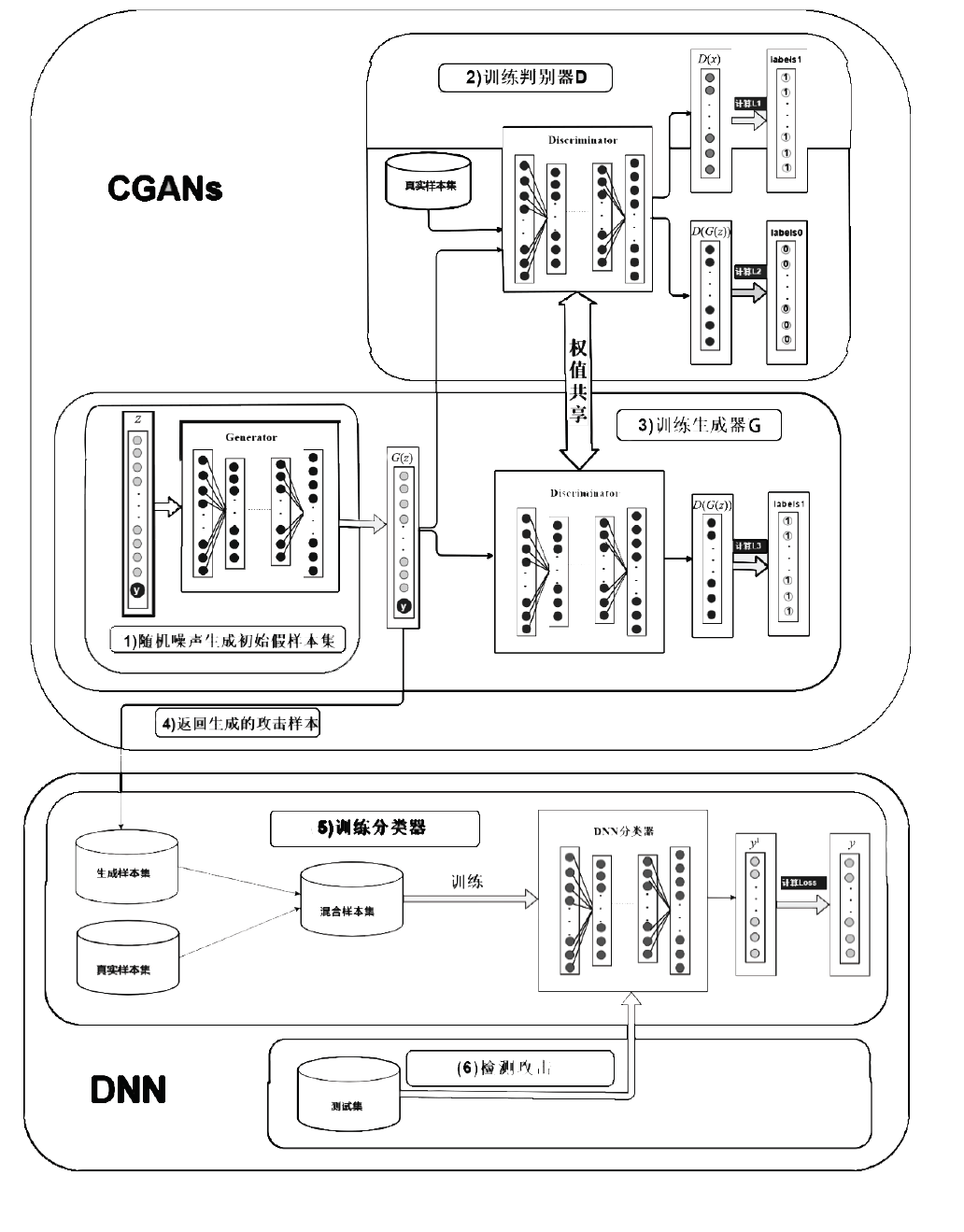
Research on Intrusion Detection Method Based on Modified CGANs
PENG Zhonglian1,2, WAN Wei1,*( ), JING Tao3, WEI Jinxia1
), JING Tao3, WEI Jinxia1
- 1. Computer Network Information Center of the Chinese Academy of Sciences, Beijing 100190, China
2. University of Chinese Academy of Sciences, Beijing 100049, China
3. Office of General Affairs, Chinese Academy of Sciences, Beijing 100084, China
-
Received:2020-02-20Online:2020-05-10Published:2020-06-05 -
Contact:Wei WAN E-mail:anquanip@cnic.cn
CLC Number:
Cite this article
PENG Zhonglian, WAN Wei, JING Tao, WEI Jinxia. Research on Intrusion Detection Method Based on Modified CGANs[J]. Netinfo Security, 2020, 20(5): 47-56.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.05.006
| 攻击类型 | 分类 | 总计 |
|---|---|---|
| DoS | back, land, neptune, pod, smurf, teardrop, mailbomb, processtable, udpstorm,apache2, worm | 11 |
| Probe | Satan, ipsweep, nmap, portsweep, mscan, saint | 6 |
| R2L | guess_passwd, ftp_write, imap, phf, multihop, warezmaster, xlock, xsnoop, snmpguess, snmpgetattack, httptunnel, sendmail, named, warezclient, spy | 15 |
| U2R | buffer_overflow, loadmodule, rootkit, perl, slotbacks, xterm, ps | 7 |
| 总计 | 39 |
| 类别 | KDDTrain+_20Percent | KDDTest+ | KDDTest-21 | |||
|---|---|---|---|---|---|---|
| 攻击类型 | 数量 | 攻击类型 | 数量 | 攻击类型 | 数量 | |
| Normal | normal | 13449 | normal | 9711 | normal | 2152 |
| 合计 | 13449 | 9711 | 2152 | |||
| Probe | ipsweep satan portsweep nmap | 710 691 587 301 | ipsweep satan portsweep nmap saint mscan | 141 735 157 73 319 996 | ipsweep satan portsweep nmap saint mscan | 141 727 156 73 309 996 |
| 合计 | 2289 | 2421 | 2402 | |||
| DoS | neptune smurf back teardrop pod land | 8282 529 196 188 38 1 | neptune smurf back teardrop pod land apache2 mailbomb processtable udpstorm | 4657 665 359 12 41 7 737 293 685 2 | neptune smurf back teardrop pod land apache2 mailbomb processtable udpstorm | 1579 627 359 12 41 7 737 293 685 2 |
| 合计 | 9234 | 7458 | 4342 | |||
| U2R | buffer_over?ow rootkit loadmodule | 6 4 1 | buffer_over?ow rootkit loadmodule perl httptunnel ps sqlattack xterm | 20 13 2 2 133 15 2 13 | buffer_over?ow rootkit loadmodule perl httptunnel ps sqlattack xterm | 20 13 2 2 133 15 2 13 |
| 合计 | 11 | 200 | 200 | |||
| R2L | guess_passwd warezmaster imap multihop phf ftp_write spy warezclient | 10 7 5 2 2 1 1 181 | guess_passwd warezmaster imap multihop phf ftp_write named sendmail xlock xsnoop worm snmpgetattack snmpguess | 1231 944 1 18 2 3 17 14 9 4 2 178 331 | guess_passwd warezmaster imap multihop phf ftp_write named sendmail xlock xsnoop worm snmpgetattack snmpguess | 1231 944 1 18 2 3 17 14 9 4 2 178 331 |
| 合计 | 209 | 2754 | 2754 | |||
| 总计 | 25192 | 22544 | 11850 | |||
| 模型 | Normal | Probe | DoS | U2R | R2L | Accuracy | Recall | Precision | F1- measure | FPR |
|---|---|---|---|---|---|---|---|---|---|---|
| ROS-DNN | 92.61 | 56.26 | 80.32 | 6.00 | 12.75 | 78.26 | 67.41 | 92.34 | 77.93 | 7.39 |
| SMOTE-DNN | 96.59 | 56.75 | 82.19 | 11.00 | 10.93 | 81.16 | 69.48 | 96.42 | 80.76 | 3.41 |
| ADASYN-DNN | 96.43 | 59.81 | 83.28 | 8.00 | 9.84 | 80.10 | 67.74 | 96.16 | 79.49 | 3.57 |
| CGANs-DNN | 96.76 | 78.88 | 88.67 | 11.00 | 46.71 | 87.98 | 79.46 | 96.98 | 88.27 | 2.33 |
| 模型 | Normal | Probe | DoS | U2R | R2L | Accuracy | Recall | Precision | F1- measure | FPR |
|---|---|---|---|---|---|---|---|---|---|---|
| ROS-DNN | 85.83 | 65.36 | 74.14 | 5.50 | 10.02 | 63.43 | 58.46 | 94.89 | 72.35 | 14.17 |
| SMOTE-DNN | 86.76 | 60.99 | 66.86 | 12.00 | 14.45 | 65.34 | 60.59 | 95.37 | 74.10 | 13.24 |
| ADASYN-DNN | 67.98 | 54.29 | 67.94 | 8.00 | 11.58 | 57.76 | 55.50 | 88.65 | 68.26 | 32.02 |
| CGANs-DNN | 89.04 | 80.19 | 78.27 | 11.33 | 25.17 | 78.43 | 75.84 | 96.63 | 84.12 | 11.22 |
| 模型 | Normal | Probe | DoS | U2R | R2L | Accuracy | Recall | Precision | F1- measure | FPR |
|---|---|---|---|---|---|---|---|---|---|---|
| KNN | 91.68 | 60.4 | 81.25 | 3.52 | 3.71 | 75.11 | 65.29 | 93.36 | 74.18 | 7.13 |
| SVM | 92.12 | 60.71 | 74.15 | 0.00 | 0.00 | 72.68 | 57.13 | 90.36 | 70.97 | 7.21 |
| RF | 97.37 | 58.53 | 80.64 | 0.54 | 7.25 | 75.61 | 60.19 | 96.14 | 72.32 | 2.54 |
| DNN | 96.12 | 67.30 | 84.40 | 2.61 | 14.26 | 80.44 | 68.47 | 95.65 | 76.10 | 3.79 |
| CGANs-DNN | 97.16 | 76.97 | 87.25 | 11.00 | 46.42 | 86.98 | 78.43 | 97.79 | 88.27 | 2.68 |
| 模型 | Normal | Probe | DoS | U2R | R2L | Accuracy | Recall | Precision | F1- measure | FPR |
|---|---|---|---|---|---|---|---|---|---|---|
| KNN | 67.49 | 60.08 | 69.31 | 3.51 | 3.16 | 56.01 | 52.69 | 88.41 | 65.13 | 30.91 |
| SVM | 68.36 | 60.44 | 57.89 | 0.00 | 0.00 | 46.88 | 41.64 | 84.15 | 58.17 | 32.14 |
| RF | 88.44 | 60.48 | 65.88 | 0.54 | 10.82 | 56.94 | 50.84 | 94.98 | 64.89 | 11.44 |
| DNN | 85.99 | 67.26 | 64.17 | 4.60 | 14.02 | 61.16 | 54.24 | 94.19 | 70.88 | 13.79 |
| CGANs-DNN | 88.14 | 80.89 | 78.82 | 12.50 | 26.17 | 73.43 | 76.86 | 97.20 | 84.92 | 12.66 |
| [1] | ZHANG Huanguo, MU Yi . Cyberspace Security[J]. China Communications, 2016,11(2):68-69. |
| [2] | ALI MH, MOHAMMED B A D A, ISMAIL M A B , et al. A New Intrusion Detection System Based on Fast Learning Network and Particle Swarm Optimization[J]. IEEE Access, 2018,18(6):20255-20261. |
| [3] | TIAN Yingjie, MIRZABAGHERI M, BAMAKAN S M H , et al. Ramp Loss One-Class Support Vector Machine; A Robust and Effective Approach to Anomaly Detection Problems[J]. Neurocomputing, 2018,310(3):223-235. |
| [4] | GANESHAN R, PAUL R S . I-AHSDT: Intrusion Detection Using Adaptive Dynamic Directive Operative Fractional Lion Clustering and Hyperbolic Secant-Based Decision Tree Classifier[J]. Journal of Experimental & Theoretical Artificial Intelligence, 2018,6(30):887-910. |
| [5] | SERPEN G , AGHAEIE. Host-Based Misuse Intrusion Detection Using PCA Feature Extraction and KNN Classification Algorithms[J]. Intelligent Data Analysis, 2018,22(5):1101-1114. |
| [6] | LI Deng, DONG Yu . Deep Learning: Methods and Applications[J]. Foundations and Trends in Signal Processing, 2014,7(3-4):197-387. |
| [7] | WONGSUPHASAWAT K, SMILKOV D, WEXLER J , et al. Visualizing Dataflow Graphs of Deep Learning Models in Tensor Flow[J]. IEEE Transactions on Visualization and Computer Graphics, 2018,24(1):1-24. |
| [8] | MALAIYA R K, KWON D, KIM J , et al. An Empirical Evaluation of Deep Learning for Network Anomaly Detection[J]. IEEE Access, 2018,18(7):140806-140817. |
| [9] | LI Chaopeng, WANG Jinlin, YE Xiaozhou . Using a Recurrent Neural Network and Restricted Boltzmann Machines for Malicious Traffic Detection[J]. Neuro Quantology, 2018,16(5):823-831. |
| [10] | ZHENG Wang . Deep Learning Based Intrusion Detection with Adversaries[J]. IEEE Access, 2018,18(6):38367-38384. |
| [11] | XIN Yang, KONG Lingshuang, LIU Zhi , et al. Machine Learning and Deep Learning Methods for Cybersecurity[J]. IEEE Access, 2018,18(6):35365-35381. |
| [12] | SEO E, SONG H M, KIM H K . GIDS: GAN based Intrusion Detection System for In-Vehicle Network [C]//IEEE. 16th Annual Conference on Privacy, Security and Trust (PST), August 28-30, 2018, Belfast, UK. New York: IEEE, 2018: 1-6. |
| [13] | GOODFELLOW I, POUGET-ABADIE J, MIRZA M et al. Generative Adversarial Nets[EB/OL]. http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.747.1316&rep=rep1&type=pdf, 2014-10-15. |
| [14] | GULRAJANI I, AHMED F, ARJOVSKY M , et al. Improved Training of Wasserstein GANs[EB/OL]. https://arxiv.org/pdf/1704.00028.pdf, 2017-10-15. |
| [15] | DHANABAL L, SHAN THARAJAH . A Study on NSL-KDD Dataset for Intrusion Detection System Based on Classification Algorithms[EB/OL]. https://ijarcce.com/upload/2015/june-15/IJARCCE%2096.pdf, 2015-10-15. |
| [16] | WANG Xiaosen, HE Kun, SONG Chuanbiao , et al. AT-GAN: A Generative Attack Model for Adversarial Transferring on Generative Adversarial Nets[EB/OL]. https://arxiv.org/pdf/1904.07793.pdf, 2020-1-15. |
| [17] | HU Weiwei, TAN Ying . Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN[EB/OL]. https://arxiv.org/pdf/1702.05983.pdf, 2017-10-15. |
| [18] | MUHAMMAD U, MUHAMMAD A, SIDDIQUE L , et al. Generative Adversarial Networks For Launching and Thwarting Adversarial Attacks on Network Intrusion Detection Systems [C]//IEEE. 15th International Wireless Communications & Mobile Computing Conference (IWCMC), June 24-28, 2019, Tangier, Morocco. New York: IEEE, 2019: 78-83. |
| [19] | MA Tao, WANG Fen, CHENG Jianjun , et al. A Hybrid Spectral Clustering and Deep Neural Network Ensemble Algorithm for Intrusion Detection in Sensor Networks[J]. Sensors, 2016,16(10):1701-1723. |
| [20] | TANG T A, MHAMDI L, MCLERNON D , et al. Deep Recurrent Neural Network for Intrusion Detection in SDN-based Networks [C]//IEEE. 4th IEEE Conference on Network Softwarization and Workshops (NetSoft), June 25-29, 2018, Montreal, QC, Canada. New York: IEEE, 2018: 202-206. |
| [21] | MUNA A H, MOUSTAFA N, SITNIKOVA E , et al. Identification of Malicious Activities in Industrial Internet of Thingsbased on Deep Learning Models[J]. Journal of Information Security and Applications, 2018,41:1-11. |
| [22] | GUILLAUME L, FERNANDO N, CHRISTOS A . Imbalanced-Learn: A Python Toolbox to Tackle the Curse of Imbalanced Datasets in Machine learning[EB/OL]. https://hal.inria.fr/hal-01516244/document, 2017-10-15. |
| [23] | CHAWLA N V, BOWYER K W, HALL L O , et al. SMOTE: Synthetic Minority Over-Sampling Technique[J]. Journal of Artificial Intelligence Research, 2002,16(1):321-357. |
| [24] | HE Haibo, BAI Yang, GARCIA E A , et al. ADASYN: Adaptive Synthetic Sampling Approach for Imbalanced Learning [C]//IEEE. 2008 IEEE International Joint Conference on Neural Networks (IEEE World Congress on Computational Intelligence), June 1-8, 2008, Hong Kong, China. New York: IEEE, 2018: 1322-1328. |
| [1] | LI Qiao, LONG Chun, WEI Jinxia, ZHAO Jing. A Hybrid Model of Intrusion Detection Based on LMDR and CNN [J]. Netinfo Security, 2020, 20(9): 117-121. |
| [2] | JIANG Nan, CUI Yaohui, WANG Jian, WU Jinchao. Context-based Attack Scenario Reconstruction Model for IDS Alarms [J]. Netinfo Security, 2020, 20(7): 1-10. |
| [3] | ZHANG Xiaoyu, WANG Huazhong. Intrusion Detection of ICS Based on Improved Border-SMOTE for Unbalance Data [J]. Netinfo Security, 2020, 20(7): 70-76. |
| [4] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [5] | Wenhua LUO, Caidian XU. Network Intrusion Detection Based on Improved MajorClust Clustering [J]. Netinfo Security, 2020, 20(2): 14-21. |
| [6] | Jian KANG, Jie WANG, Zhengxu LI, Guangda ZHANG. A Model for Anomaly Intrusion Detection with Different Feature Extraction Strategies in IoT [J]. Netinfo Security, 2019, 19(9): 21-25. |
| [7] | Wenying FENG, Xiaobo GUO, Yuanye HE, Cong XUE. Intrusion Detection Model Based on Feedforward Neural Network [J]. Netinfo Security, 2019, 19(9): 101-105. |
| [8] | Xuli RAO, Pengna XU, Zhide CHEN, Li XU. Network Intrusion Detection with Incomplete Information Based on Deep Learning [J]. Netinfo Security, 2019, 19(6): 53-60. |
| [9] | Chunguang MA, Yaoyao GUO, Peng WU, Haibo LIU. Review of Image Enhancement Based on Generative Adversarial Networks [J]. Netinfo Security, 2019, 19(5): 10-12. |
| [10] | Jinghao LIU, Siping MAO, Xiaomei FU. Intrusion Detection Model Based on ICA Algorithm and Deep Neural Network [J]. Netinfo Security, 2019, 19(3): 1-10. |
| [11] | Hong CHEN, Yue XIAO, Chenglong XIAO, Jianhu CHEN. The Intrusion Detection Method of SMOTE Algorithm with Maximum Dissimilarity Coefficient Density [J]. Netinfo Security, 2019, 19(3): 61-71. |
| [12] | Zheng TIAN, Shu LI, Yizhen SUN, Xi LI. Industrial Control System Intrusion Detection Model Based on S7 Protocol [J]. Netinfo Security, 2019, 19(11): 8-13. |
| [13] | Yang ZHANG, Yuangang YAO. Research on Network Intrusion Detection Based on Xgboost [J]. Netinfo Security, 2018, 18(9): 102-105. |
| [14] | Gelin ZHANG, Yong LI. Non-negative Matrix Factorization Optimization and Its Application in Network Intrusion Detection [J]. Netinfo Security, 2018, 18(8): 73-78. |
| [15] | Shuning WEI, Xingru CHEN, Yong JIAO, Jin WANG. Research on the Application of AR-OSELM Algorithm in Network Intrusion Detection [J]. Netinfo Security, 2018, 18(6): 1-6. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||