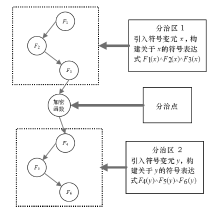
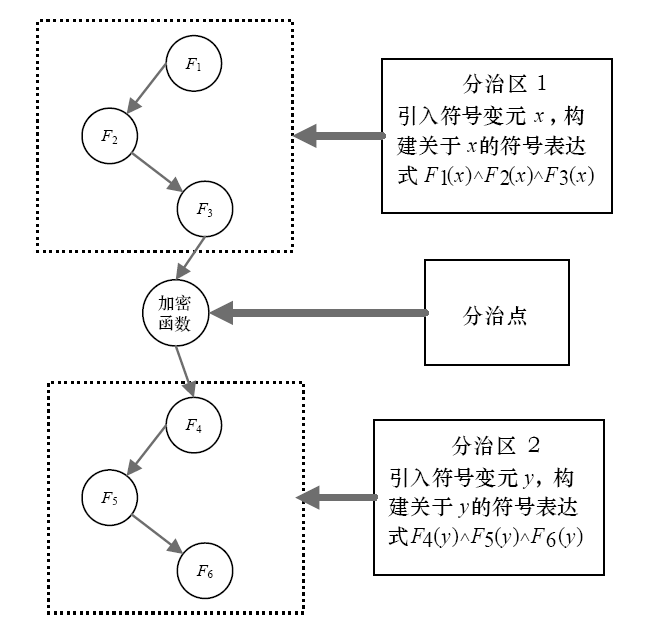
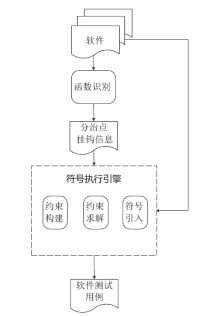
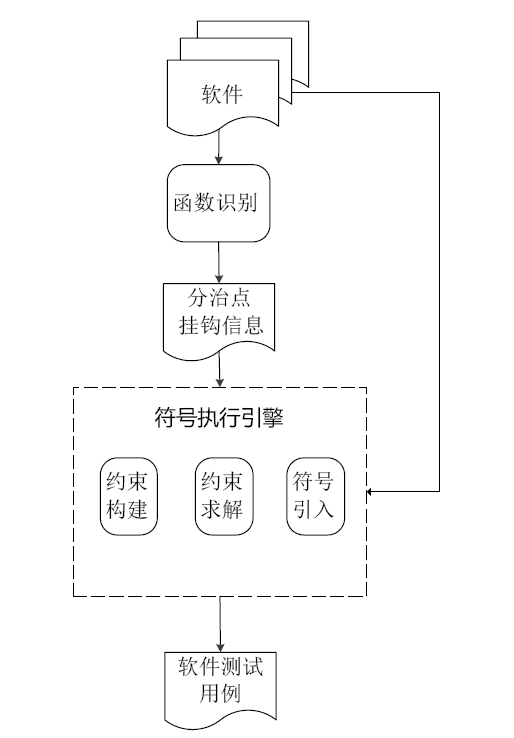
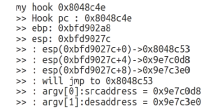
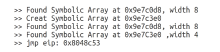
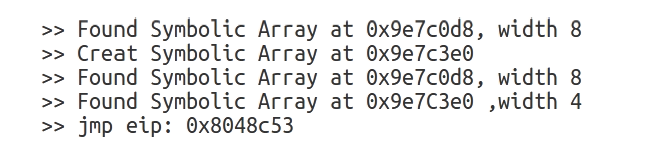
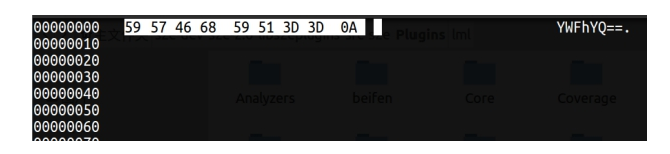
| [1] |
DONG Qixing . Research on Test Case Generation Technology Based on Dynamic Symbol Execution[D]. Hefei:University of Science and Technology of China, 2014.
|
|
董齐兴 . 基于动态符号执行的测试用例生成技术研究[D]. 合肥:中国科学技术大学, 2014.
|
| [2] |
RENFER G . Automatic Program Testing [EB/OL]. https://link.springer.com/book/10.1007/978-3-319-30348-2, 1962/2020, 2020-4-10.
|
| [3] |
MILLER B P, FREDRIKSEN L, SO B . An Empirical Study of the Reliability of UNIX Utilities[J]. Communications of the ACM, 1990,33(12):32-44.
|
| [4] |
CHEN Jianmin, SHU Hui, XIONG Xiaobing . Fuzzing Test Method Based on Symbolic Execution[J]. Computer Engineering, 2009,35(21):33-35.
|
|
陈建敏, 舒辉, 熊小兵 . 基于符号化执行的 Fuzzing 测试方法[J]. 计算机工程, 2009; 35(21):33-35.
|
| [5] |
CHA S K, AVGERINOS T, REBERT A , et al. Unleashing Mayhem on Binary Code [C]//IEEE. 2012 IEEE Symposium on Security and Privacy, May 20-23, 2012, San Francisco, CA, USA. NJ: IEEE, 2012: 380-394.
|
| [6] |
STEPHENS N, GROSEN J, SALLS C , et al. Driller: Augmenting Fuzzing Through Selective Symbolic Execution[EB/OL]. https://sefcom.asu.edu/publications/driller:augmenting-fuzzing-through-selective-symbolic-execution-ndss2016.pdf, 2020-4-10.
|
| [7] |
RAWAT S, JAIN V, KUMAR A , et al. VUzzer: Application-aware Evolutionary Fuzzing[EB/OL]. http://sharcs-project.eu/m/filer_public/48/8c/488c5fb7-9aad-4c87-ab9c-5ff251ebc73d/vuzzer_ndss17.pdf, 2020-4-10.
|
| [8] |
JOHANSSON W, SVENSSON M, LARSON U E , et al. T-Fuzz: Model-Based Fuzzing for Robustness Testing of Telecommunication Protocols [C]//IEEE. 2014 IEEE Seventh International Conference on Software Testing, Verification and Validation, March 31-April 4, 2014, Cleveland, OH, USA. NJ: IEEE, 2014: 323-332.
|
| [9] |
GANESH V, DILL D L . A Decision Procedure for Bit-vectors and Arrays[M] //Springer. Computer Aided Verification. Heidelberg: Springer, Berlin, Heidelberg, 2007: 519-531.
|
| [10] |
DE MOURA L, BJORNER N . Z3: An Efficient SMT Solver[M] //Springer. Tools and Algorithms for the Construction and Analysis of Systems. Heidelberg: Springer, Berlin, Heidelberg, 2008: 337-340.
|
| [11] |
CHIPOUNOV V, KUZNETSOV V, CANDEA G . S2E: A Platform for In-vivo Multi-path Analysis of Software Systems[EB/OL]. https://www.ndsl.kaist.edu/~kyoungsoo/ee807_2014/papers/s2e.pdf, 2020-4-10.
|
| [12] |
Shellphish . Angr[EB/OL]. https://github.com/angr/, 2020-4-7.
|
| [13] |
HUANG S K, HUANG M H, HUANG P Y , et al. CRAX: Software Crash Analysis for Automatic Exploit Generation by Modeling Attacks as Symbolic Continuations [C]//IEEE. 2012 IEEE Sixth International Conference on Software Security and Reliability, June 20-22, 2012, Gaithersburg, MD, USA. NJ: IEEE, 2012: 78-87.
|
| [14] |
WANG Yan, ZHANG Chao, XIANG Xiaobo , et al. Revery: from Proof-of-concept to Exploitable[EB/OL]. https://www.researchgate.net/publication/328321653_Revery_From_Proof-of-Concept_to_Exploitable, 2020-4-10.
|
| [15] |
GODEFROID P, LEVIN M Y, MOLNAR D . SAGE: Whitebox Fuzzing for Security Testing[J]. Communications of the ACM, 2012,55(3):40-44.
|
| [16] |
BALDONI R, COPPA E, D’ELIA D C , et al. A Survey of Symbolic Execution Techniques[EB/OL]. https://arxiv.org/abs/1610.00502, 2020-4-10.
|
| [17] |
HOU Gang, ZHOU Kuanjiu, YONG Jiawei , et al. A Review of Research on State Explosion in Model Detection[J]. Computer Science, 2013,40(S1):77-86, 111.
|
|
侯刚, 周宽久, 勇嘉伟 , 等. 模型检测中状态爆炸问题研究综述[J]. 计算机科学, 2013,40(S1):77-86,111.
|
| [18] |
BELLARD F. QEMU , A Fast and Portable Dynamic Translator[EB/OL]. https://www.mendeley.com/catalogue/e628a8cb-4d09-36c3-bf08-824b8a481808/, 2020-4-10.
|
| [19] |
CADAR C, DUNBAR D, ENGLER D . Unassisted and Automatic Generation of High-coverage Tests for Complex Systems Programs[EB/OL]. https://static.usenix.org/events/osdi08/tech/full_papers/cadar/cadar.pdf, 2009/2020, 2020-4-10.
|
| [20] |
LATTNER C, ADVE V . LLVM: A Compilation Framework for Lifelong Program Analysis & Transformation [C]//IEEE. InInternational Symposium on Code Generation and Optimization, March 20-24, 2004, San Jose, CA, USA. NJ: IEEE, 2004: 75-86.
|
 ), LU Yuliang
), LU Yuliang