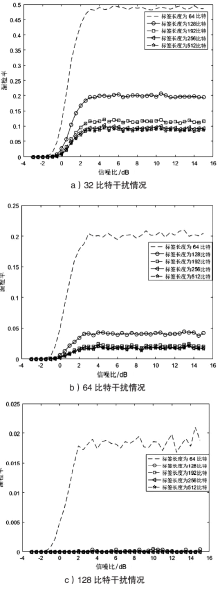
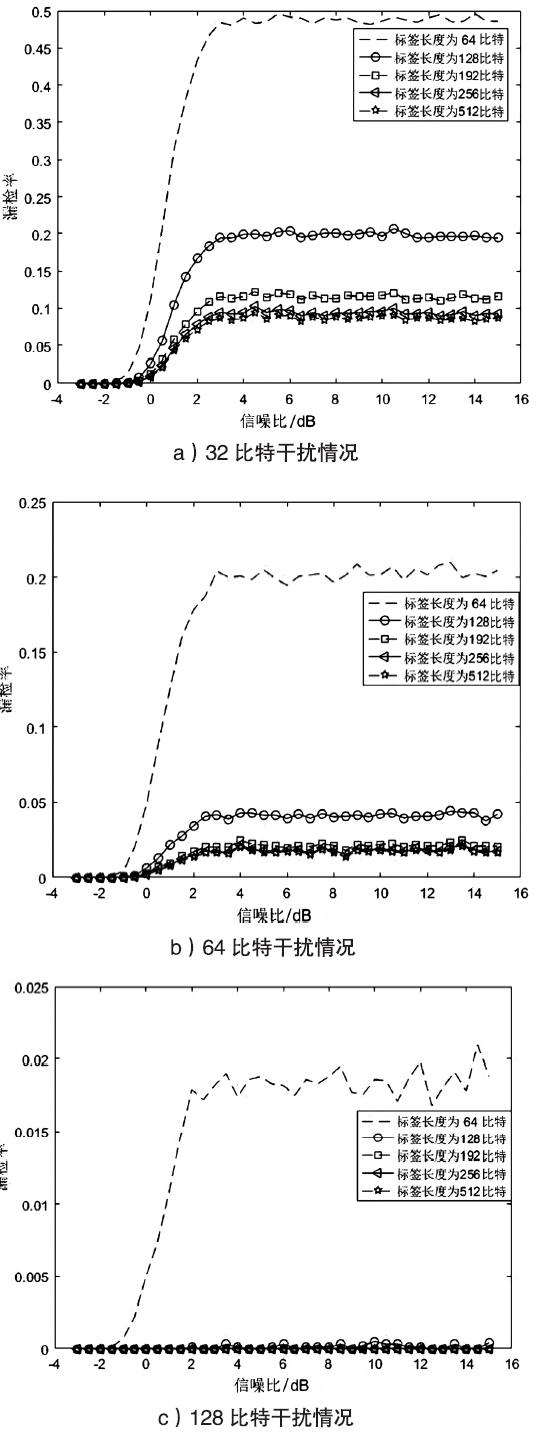
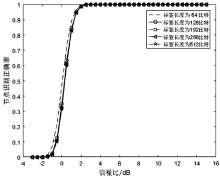
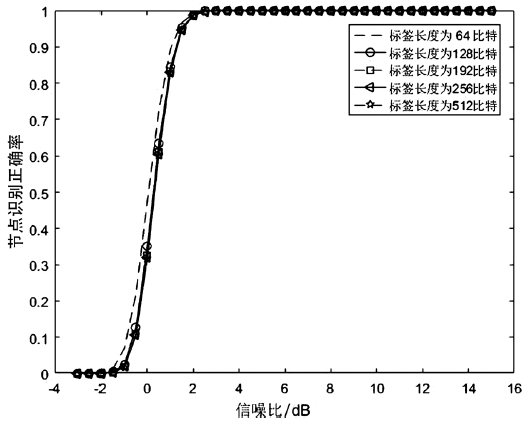
| [1] |
LAI Lifeng, GAMAL E, POOR H V.Authentication Over Noisy Channels[J]. IEEE Transactions on Information Theory, 2009, 55(2): 906-916.
|
| [2] |
WANG Xianbin, HAO Peng, LAJOS H.Physical-layer Authentication for Wireless Security Enhancement: Current Challenges and Future Developments[J]. IEEE Communications Magazine, 2016, 54(6): 152-158.
|
| [3] |
TUGNAIT J K.Wireless User Authentication via Comparison of Power Spectral Densities[J]. IEEE Journal on Selected Areas in Communications, 2013, 31(9): 1791-1802.
|
| [4] |
CHOI J.A Coding Approach with Key-channel Randomization for Physical-layer Authentication[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(1): 175-185.
|
| [5] |
YU P L, BARAS J S, SADLER B M.Physical-layer Authentication[J]. IEEE Transactions on Information Forensics and Security, 2008, 3(1): 38-51.
|
| [6] |
WANG Wenhao, SUN Zhi, PIAO Sixu, et al.Wireless Physical-layer Identification: Modeling and Validation[J]. IEEE Transactions on Information Forensics & Security, 2015, 11(9): 2091-2106.
|
| [7] |
BIHL T J, BAUER K W, TEMPLE M A.Feature Selection for RF Fingerprinting with Multiple Discriminant Analysis and Using ZigBee Device Emissions[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(8): 1862-1874.
|
| [8] |
REISING D R, TEMPLE M A, JACKSON J A.Authorized and Rogue Device Discrimination Using Dimensionally Reduced RF-DNA Fingerprints[J]. IEEE Transactions on Information Forensics & Security, 2015, 10(6): 1180-1192.
|
| [9] |
JORSWIECK E, TOMASIN S, SEZGIN A.Broadcasting into the Uncertainty: Authentication and Confidentiality by Physical-Layer Processing[J]. Proceedings of the IEEE, 2015, 103(10): 1702-1724.
|
| [10] |
ZHANG Shengjun, JIN Liang, LOU Yangming, et al.Secret Key Generation Based on Two-Way Randomness for TDD-SISO System[J]. China Communications, 2018, 15(7): 202-216.
|
| [11] |
ALTHUNIBAT S, SUCASAS V, MANTAS G, et al.Physical-layer Entity Authentication Scheme for Mobile MIMO Systems[J]. IET Communications, 2018, 12(6): 712-718.
|
| [12] |
SHAN Dan, ZENG Kai, XIANG Weidong, et al.PHY-CRAM: Physical Layer Challenge-response Authentication Mechanism for Wireless Networks[J]. IEEE Journal on Selected Areas in Communications, 2013, 31(9): 1817-1827.
|
| [13] |
WU Xiaofu, YANG Zhen.Physical-layer Authentication for Multi-carrier Transmission[J]. IEEE Communications Letters, 2015, 19(1): 74-77.
|
| [14] |
PENG Hao, WANG Xianbin, BEHNAD A.Relay Authentication by Exploiting I/Q Imbalance in Amplify-and-forward System[C]//IEEE. Global Communications Conference, December 8-12, 2014, Austin, Texas, USA. New Jersey: IEEE, 2015: 613-618.
|
| [15] |
ZHENG Yue, SOMNATH D S, CHANG C H.Securing IoT Monitoring Device using PUF and Physical Layer Authentication[C]//IEEE. IEEE International Symposium on Circuits and Systems, May 27-30, 2018, Florence, Italy. New Jersey: IEEE, 2018: 1-5.
|
| [16] |
CHEN An.Utilizing the Variability of Resistive Random Access Memory to Implement Reconfigurable Physical Unclonable Functions[J]. IEEE Electron Device Letters, 2015, 36(2): 138-140.
|
| [17] |
XIONG Jun, MA Dongtang, WONG K K, et al.Robust Masked Beam Forming for MISO Cognitive Radio Networks with Unknown Eavesdroppers[J]. IEEE Transactions on Vehicular Technology, 2016, 65(2): 744-755.
|
| [18] |
ZHANG Jiliang, QU Gang, LV Yongqiang, et al.A Survey on Silicon PUFs and Recent Advances in Ring Oscillator PUFs[J]. Journal of Computer Science and Technology, 2014, 29(4): 664-678.
|
| [19] |
HOLCOMB D E, BURLESON W P, FU K.Power-Up SRAM State as an Identifying Fingerprint and Source of True Random Numbers[J]. IEEE Transactions on Computers, 2008, 58(9): 1198-1210.
|
| [20] |
GUAJARDO J, KUMAR S S, SCHRIJEN G J, et al.FPGA Intrinsic PUFs and Their Use for IP Protection[M]//Springer. Cryptographic Hardware and Embedded Systems-CHES 2007. Heidelberg: Springer, 2007: 63-80.
|
 ), GONG Ming2, MA Zhao2
), GONG Ming2, MA Zhao2