Netinfo Security ›› 2019, Vol. 19 ›› Issue (7): 50-58.doi: 10.3969/j.issn.1671-1122.2019.07.006
• Orginal Article • Previous Articles Next Articles
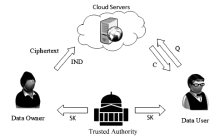
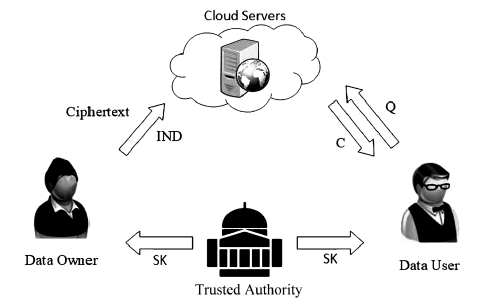
Secure Attribute Based Encryption Enabled Cloud Storage System with Ciphertext Search
Jianhua LIU1, Xiaokun ZHENG2( ), Dong ZHENG3, Zhangheng AO3
), Dong ZHENG3, Zhangheng AO3
- 1. Department of Information Center, Xi’an University of Posts and Telecommunications, Xi’an Shannxi 710121, China;
2. School of Computer Science and Technology, Xi’an University of Posts and Telecommunications,Xi’an Shannxi 710121, China;
3. National Engineering Laboratory for Wireless Security,Xi’an University of Posts and Telecommunications, Xi’an Shannxi 710121, China;
-
Received:2018-12-10Online:2019-07-19Published:2020-05-11
CLC Number:
Cite this article
Jianhua LIU, Xiaokun ZHENG, Dong ZHENG, Zhangheng AO. Secure Attribute Based Encryption Enabled Cloud Storage System with Ciphertext Search[J]. Netinfo Security, 2019, 19(7): 50-58.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.07.006
| [1] | ZHANG Y H, DENG R H, LIU X M, et al.Blockchain Based Efficient and Robust Fair Payment for Outsourcing Services in Cloud Computing[J]. Information Sciences, 2018, 46(2): 262-277. |
| [2] | ZHANG Yinghui, WU Axin, ZHENG Dong.Efficent and Privacy-aware Attribute-based Data Sharing in Mobile Cloud Computing[J]. Journal of Ambient Intelligence and Humanized Computing, 2018, 9(4): 1039-1048. |
| [3] | LV Congdong, HAN Zhen.A Security Model of Cloud Computing Based on IP Model[J]. Netinfo Security, 2018, 18(11): 27-32 . |
| 吕从东,韩臻. 基于IP模型的云计算安全模型[J].信息网络安全,2018,18(11):27-32. | |
| [4] | SONG Wei, WANG Bing, WANG Qian, et al.A Privacy-preserved Full-text Retrieval Algorithm over Encrypted Data for Cloud Storage Applications[J]. Journal of Parelled and Distributed Computing, 2017, 99(4): 14-27. |
| [5] | STANEK J, SORNIOTTI A, ANDROULAKI E, et al.A Secure Data Deduplication Scheme for Cloud Storage[C]//Springer. International Conference on Financial Cryptography and Data Security, March 3-7, 2014, Christ Church Barbados. Berlin, Heidelberg: Springer, 2014: 99-118. |
| [6] | KAMARA S, LAUTER K.Cryptographic Cloud Storage[M]. Berlin Heidelberg: Springer, 2010. |
| [7] | WU Jiyi, PING Lingdi, GE Xiaoping, et al.Cloud Storage as the Infrastructure of Cloud Computing[C]//IEEE. Intelligent Computing and Cognitive Informatics (ICICCI), June 22-23, 2010, Kuala Lumpur, Malaysia. New York: IEEE, 2010: 380-383. |
| [8] | SANAEI Z, ABOLFAZLI S, GANI A, et al.Heterogeneity in Mobile Cloud Computing: Taxonomy and Open Challenges[J]. Communications Surveys & Tutorials, IEEE, 2014, 16(1): 369-392. |
| [9] | WEI Lifei, ZHU Haojin, CAO Zhenfu, et al.Security and Privacy for Storage and Computation in Cloud Computing[J]. Information Sciences, 2014, 25(8): 371-386. |
| [10] | HEI Yiming, LIU Jianwei, ZHANG Zongyang, et al.Blockchain-based Distributed Cloud Storage System with Public Verification[J]. Netinfo Security, 2019, 19(3): 52-60. |
| 黑一鸣,刘建伟,张宗洋,等. 基于区块链的可公开验证分布式云存储系统[J].信息网络安全,2019,19(3):52-60. | |
| [11] | ZHU Jie.Information Adaptive Management and Scheduling Model for Active Fault-tolerant Cloud Storage System[J]. Intelligent Computer and Applications, 2019, 9(2):224-227. |
| 朱洁. 主动容错云存储系统的信息自适应管理调度模型[J].智能计算机与应用,2019,9(2):224-227. | |
| [12] | LIU Yantao, LIU Heng.Cloud Storage System Based on Network Coding[J]. Computer Science, 2018, 45(12):293-298, 312. |
| 刘宴涛,刘珩. 一种基于网格编码的云存储系统[J]. 计算机科学,2018, 45(12):293-298, 312. | |
| [13] | LI Jing,LIU Dongshi.Reliability Evaluation Model for Cloud Storage Systems With Proactive Fault Tolerance[J]. Journal of Computer Applications, 2018, 38(9): 2631-2636, 2649. |
| 李静,刘冬实. 主动容错云存储系统的可靠性评价模型[J]. 计算机应用, 2018,38(9):2631-2636,2649. | |
| [14] | WANG Shuai, LV Jianghua, WANG Ronghe, et al.A Multimedia File Cloud Storage System to Support Data Deduplication and Logical Expansion[J]. Journal of Computer Research and Development, 2018, 55(5): 1034-1048. |
| 汪帅,吕江花,汪溁鹤,等.一种支持数据去冗和扩容的多媒体文件云存储系统实现[J]. 计算机研究与发展,2018,55(5):1034-1048. | |
| [15] | HUANG Ke.Research on Data Auditing Protocol With Dedupli-cation[D]. Chengdu: University of Electronic Science and Technology of China, 2015. |
| 黄可. 重复数据可删除的云数据审计协议的研究[D]. 成都:电子科技大学,2015. | |
| [16] | ZHENG Dong, ZHAO Qinglan, ZHANG Yinghui.Cryptography Review[J]. Journal of Xi’an University of Posts and Telecommunications, 2013, 18(6): 1-10. |
| 郑东,赵庆兰,张应辉.密码学综述[J].西安邮电大学,2013,18(6):1-10. | |
| [17] | LIU Mingjie, WANG An.Fully Homomorphic Encryption and Its Applications[J]. Journal of Computer Research and Development, 2014, 51(12): 2593-2603. |
| [18] | WANG Rongbing, LI Yanan, XU Hongyan, et al.Full Homomorphic Encryption Scheme over Real Number Suitable for Cloud Service Environment[J]. Netinfo Security, 2017(11): 49-56. |
| 王嵘冰,李雅囡,徐红艳,等. 适合云服务环境的实数全同态加密方案[J].信息网络安全,2017,17(11):49-56. | |
| [19] | LI Mengtian, HU bin. RLWE-based Fully Homomorphic Encryption Schenme with Batch Technique[J]. Computer Science. 2019, 46(3): 209-216. |
| 李孟天,胡斌. 基于批处理技术的RLWE全同态加密方案[J]. 计算机科学,2019,46(3):209-216. | |
| [20] | LI Zengpeng, MA Chunguang, ZHAO Minghao.Leveled Fully Homomorphic Encryption Against Adaptive Key Recovery Attacks[J]. Journal of Computer Research and Development, 2019, 56(3): 496-507. |
| 李增鹏,马春光,赵明昊. 抵抗自适应密钥恢复攻击的层级全同态加密[J].计算机研究与发展,2019,56(3):496-507. | |
| [21] | ZHANG Yinghui, ZHENG Dong, DENG Robert H.Security and Privacy in Smart Health: Efficient Policy-Hiding Attrubute-Based Access Control[J]. IEEE Internet of Things Journal , 2018, 5(3): 2130-2145. |
| [22] | ZHAO Zhiyuan, WANG Jianhua, XU Kaiyong, et al.Fully Outsourced Attribute-Based Encryption with Verifiability for Cloud Storage[J]. Journal of Computer Research and Development, 2019, 56(2): 443-352. |
| 赵志远,王建华,徐开勇,等.面向云存储的支持完全外包属性基加密方案[J]. 计算机研究与发展,2019,56(2):443-352. | |
| [23] | ZHANG Xinglan, CUI Yao.Attribute-based Encryption Schema with Group Signatures[J]. Chinese Journal of Network and Information Security, 2019, 5(1): 15-20. |
| 张兴兰,崔遥. 基于群签名的属性加密方案[J]. 网络与信息安全学报,2019,5(1):15-20. | |
| [24] | GUAN Wei, ZHANG Lei.MAH-ABPRE Based Privacy Protection Algorithm for Big Data[J]. Computer Engineering and Design, 2018, 39(11): 3356-3424. |
| 关巍,张磊. 属性基代理重加密的大数据隐私保护方法[J].计算机工程与设计,2018,39(11):3356-3424. | |
| [25] | LIANG Kaitai, FANG Liming, WONG Duncan S, et al.A Ciphertext-policy Attribute-based Proxy Re-encryption Scheme for Data Sharing in Public Clouds[J]. Concurrency and Computation Practice and Experience, 2015, 27(8): 2004-2027. |
| [26] | XU Jieru, CHEN Kefei, SHEN Zhonghua, et al.Improved Certificate-based Conditional Proxy Re-encryption Scheme[J]. Journal of Cryptologic Reserch, 2018, 5(4): 344-358. |
| 徐洁如,陈克非,沈忠华,等. 改进的基于证书条件代理重加密方案[J]. 密码学报,2018,5(4):344-358. | |
| [27] | HU Junpeng, SHEN Jinan, LIANG Fang.Improved Identity-based Broadcast Proxy Re-encryption Storage Scheme in Cloud[J]. Application Research of Computers, 2017, 34(5): 1520-1524. |
| 胡俊鹏,沈济南,梁芳. 一种改进的基于身份广播代理重加密云存储方案[J]. 计算机应用研究,2017,34(5):1520-1524. | |
| [28] | BETHENCOURT J, SAHAI A, WATERS B.Ciphertext-policy Attribute-based Encryption[C]//IEEE. IEEE Symposium on Security and Privacy (SP '07). May 20-23, 2007. Berkeley, CA . New York: IEEE, 2007: 321-334. |
| [29] | LIN Peng, JIANG Jie, CHEN Tieming.Application of Keyword Searchable Encryption in Cloud[J]. Journal on Communications, 2015,36(Z1);259-265. |
| 林鹏,江颉,陈铁明. 云环境下关键词搜索加密算法研究[J]. 通信学报,2015,36(Z1):259-265. | |
| [30] | QIU Shuo, LIU Jiqiang, SHI Yanfeng, et al.Hidden Policy Ciphertext-policy Attribute-based Encryption with Keyword Search Against Keyword Guessing Attack[J]. Science China Information Sciences, 2017, 60(5): 5-21. |
| [1] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| [2] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [3] | Shengwei XU, Feijie WANG. Attribute-based Encryption Scheme Traced Under Multi-authority [J]. Netinfo Security, 2020, 20(1): 33-39. |
| [4] | Xiaoran LI, Rong HAO, Jia YU. Certificateless Provable Data Possession with Data Uploading Control [J]. Netinfo Security, 2020, 20(1): 83-88. |
| [5] | WANG Jinmiao, WANG Guowei, WANG Mei, ZHU Ruijin. Achieving Privacy Preserving and Flexible Access Control in Fog Computing [J]. Netinfo Security, 2019, 19(9): 41-45. |
| [6] | WANG Shengyu, WANG Jinmiao, DONG Qingfeng, ZHU Ruijin. A Survey of Attribute-based Encryption Technology [J]. Netinfo Security, 2019, 19(9): 76-80. |
| [7] | HOU Lin, LI Mingjie, XU Jian, ZHOU Fucai. Distributed Dynamic Provable Data Possession Model Based on Flexible Length-based Authenticated Skip List [J]. Netinfo Security, 2019, 19(7): 67-74. |
| [8] | Zhongyuan QIN, Yin HAN, Qunfang ZHANG, Xuejin ZHU. An Improved Scheme of Multi-PKG Cloud Storage Access Control [J]. Netinfo Security, 2019, 19(6): 11-18. |
| [9] | Bilin SHAO, Xiaojun LI, Genqing BIAN, Yu ZHAO. A Survey on Data Integrity Auditing Technology in Cloud Storage [J]. Netinfo Security, 2019, 19(6): 28-36. |
| [10] | Xixi YAN, Qichao ZHANG, Yongli TANG, Qinlong HUANG. Ciphertext Policy Attribute-based Encryption Scheme Supporting Traitor Tracing [J]. Netinfo Security, 2019, 19(5): 47-53. |
| [11] | Yiming HEI, Jianwei LIU, Zongyang ZHANG, Hui YU. Blockchain-based Distributed Cloud Storage System with Public Verification [J]. Netinfo Security, 2019, 19(3): 52-60. |
| [12] | Shuai LI, Xiaojie LIU, Bing XU. Research on a Disk Data Synchronization Method Based on Directory Hash Tree [J]. Netinfo Security, 2019, 19(2): 53-59. |
| [13] | Xing ZHAO, Xiaodong WANG, Chuanrong ZHANG. A Dynamic Cloud Security Storage System Based on Data Drifting [J]. Netinfo Security, 2019, 19(10): 65-73. |
| [14] | Zhongyuan QIN, Yin HAN, Xuejin ZHU. Research on Ciphertext Full-text Retrieval of Cloud Storage Based on Improved DGHV Algorithm [J]. Netinfo Security, 2019, 19(1): 8-8. |
| [15] | HU Ronglei, HE Yanqiong, ZENG Ping, FAN Xiaohong. Design and Implementation of Medical Privacy Protection Scheme in Big Data Environment [J]. 信息网络安全, 2018, 18(9): 48-54. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||