Netinfo Security ›› 2019, Vol. 19 ›› Issue (7): 31-41.doi: 10.3969/j.issn.1671-1122.2019.07.004
• Orginal Article • Previous Articles Next Articles
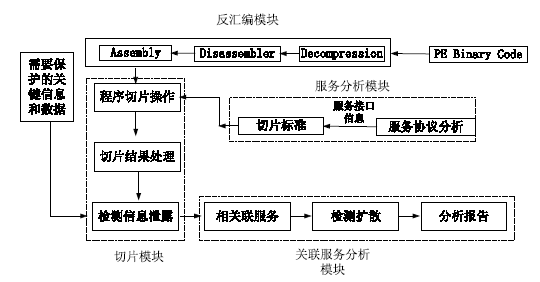
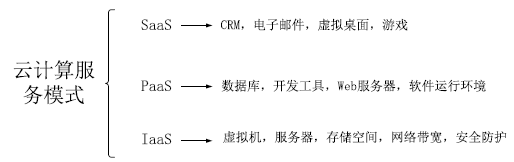
Research on Software Security Model of Cloud Computing Based on Program Slicing Technology
Yanpeng CUI, Luming FENG( ), Zheng YAN, Huaqing LIN
), Zheng YAN, Huaqing LIN
- Xidian University, Xi’an Shaanxi 710071, China
-
Received:2018-10-15Online:2019-07-19Published:2020-05-11
CLC Number:
Cite this article
Yanpeng CUI, Luming FENG, Zheng YAN, Huaqing LIN. Research on Software Security Model of Cloud Computing Based on Program Slicing Technology[J]. Netinfo Security, 2019, 19(7): 31-41.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.07.004
| [1] | KRSUL I V.Software Vulnerability Analysis[M]. West Lafayette: Purdue University, 1998. |
| [2] | ABLON L, BOGART A. Zero Days, Thousands of Nights: The Life and Times of Zero-Day Vulnerabilities and Their Exploits[M]. California: Rand Corporation, 2017. |
| [3] | MCGRAW G.Software Security[J]. Security & Privacy IEEE, 2012, 36(9): 662-665. |
| [4] | WEISER M.Program Slices: Formal,Psychological,Practical Investigations of An Automatic Program Abstraction Method[EB/OL]. , 2018-9-15. |
| [5] | WEISER M.Program Slicing[C]//IEEE. Proceedings of the 5th International Conference on Software Engineering, March 9-12, 1981, San Diego, California, USA. New Jersey: IEEE, 1981: 439-449. |
| [6] | WEISER M.Programmers Use Slices When Debugging[J]. Communications of the ACM, 1982, 25(7): 446-452. |
| [7] | GALLAGHER K B, LYLE J R.Using Program Slicing in Software Maintenance[J]. IEEE Transactions on Software Engineering, 1991, 17(8): 751-761. |
| [8] | LUCIA A.Program Slicing: Methods and Applications[C]//IEEE. Proceedings First IEEE International Workshop on Source Code Analysis and Manipulation, November 10-December 10, 2001, Florence, Italy. Washington: IEEE, 2001: 142-149. |
| [9] | GALLAGHER K B, LYLE J R.Software Safety and Program Slicing[C]//IEEE. COMPASS’93: Proceedings of the Eighth Annual Conference on Computer, June 14-17, 1993, Gaithersburg, MD, USA. Maryland: IEEE, 1993: 71-80. |
| [10] | OTTENSTEIN K J, OTTENSTEIN L M.The Program Dependence Graph in a Software Development Environment[J]. ACM Sigplan Notices, 1993, 19(5): 177-184. |
| [11] | KUCK D J, KUHN R H, PADUA D A, et al.Dependence Graphs and Compiler Optimizations[C]//ACM. Proceedings of the 8th ACM SIGPLAN-SIGACT symposium on Principles of Programming Languages, January 26-28, 1981, Williamsburg, Virginia. New York: ACM, 1981: 207-218. |
| [12] | FERRANTE J, OTTENSTEIN K J, WARREN J D.The Program Dependence Graph and Its Use in Optimization[J]. ACM Transactions on Programming Languages and Systems (TOPLAS), 1987, 9(3): 319-349. |
| [13] | KOREL B, LASKI J.Dynamic Slicing of Computer Programs[J]. Journal of Systems and Software, 1990, 13(3): 187-195. |
| [14] | KRSU L.Software Vulnerability Analysis[M]. West Lafayette: Purdue University, 1998. |
| [15] | LIU B, SHI L, CAI Z, et al.Software Vulnerability Discovery Techniques: A Survey[C]//IEEE. 2012 Fourth International Conference on Multimedia Information Networking and Security, November 2-4, 2012, Washington, DC, USA. Washington: IEEE Computer Society, 2012: 152-156. |
| [16] | STAVROULAKIS P, Stamp M.Handbook of Information and Communication Security[M]. Berlin: Springer Science & Business Media, 2010. |
| [17] | MCGRAW G, MORRISETT G.Attacking Malicious Code: A Report to the Infosec Research Council[J]. IEEE software, 2000 (5): 33-41. |
| [18] | COLLBERG C S, THOMBORSON C.Watermarking, Tamper-proofing, and Obfuscation-tools for Software Protection[J]. IEEE Transactions on Software Engineering, 2002, 28(8): 735-746. |
| [19] | LIU M, JIA C, LIU L, et al.Extracting Sent Message Formats from Executables Using Backward Slicing[C]//IEEE. 2013 Fourth International Conference on Emerging Intelligent Data and Web Technologies, September 9-11, 2013, Washington, DC, USA. Washington: IEEE Computer Society, 2013: 377-384. |
| [20] | ROZINOV K.Efficient Static Analysis of Executables for Detecting Malicious Behaviors[EB/OL]. , 2018-9-15. |
| [21] | JOHNSON N M, CABALLERO J, CHEN K Z, et al.Differential Slicing: Identifying Causal Execution Differences for Security Applications[C]//IEEE. 2011 IEEE Symposium on Security and Privacy, May 22-25, 2011, Berkeley, California, USA. California: Security and Privacy (SP), 2011: 347-362. |
| [22] | ZHU E, LIU F, FANG X, et al.DYBS: A Lightweight Dynamic Slicing Framework for Diagnosing Attacks on x86 Binary Programs[J]. Journal of Software, 2014, 9(3): 560-568. |
| [23] | HUANG S, ZHENG Y, ZHANG R.Attack Diagnosis on Binary Executables Using Dynamic Program Slicing[J]. . |
| [24] | LU Y, YI S, LEI Z, et al.Binary Software Vulnerability Analysis Based on Bidirectional-slicing[C]//IEEE. 2012 Second International Conference on Instrumentation, Measurement, Computer, Communication and Control, December 8-10, 2012, Washington, DC, USA. Washington: IEEE Computer Society, 2012: 842-845. |
| [25] | LESTRINGANT P,GUIHÉRY F,FOUQUE P A. Assisted Identification of Mode of Operation in Binary Code with Dynamic Data Flow Slicing[C]//Springer. International Conference on Applied Cryptography and Network Security, June 19-22, 2016, London (Guildford), United Kingdom. Berlin: Springer, Cham, 2016: 561-579. |
| [26] | DENG X, XU G, SUN G, et al.Software Watermarking Based on Dynamic Program Slicing[C]//IEEE. 2008 International Conference on Intelligent Information Hiding and Multimedia Signal Processing, August 15-17, 2008, Harbin, China. Washington: IEEE, 2008: 461-464. |
| [27] | LI X, CAO Y, FENG Z, et al.Web Service Security Analysis Model Based on Program Slicing[C]//IEEE. 2010 10th International Conference on Quality Software, July 14-15, 2010, Zhangjiajie, China. Washington: IEEE, 2010: 422-428. |
| [28] | FU W, ZHANG Y, ZHU X, et al.WSSecTool: A Web Service Security Analysis Tool Based on Program Slicing[C]//IEEE. 2012 IEEE Eighth World Congress on Services, June 24-29, 2012, Washington, DC, USA. Washington: IEEE Computer Society, 2012: 179-183. |
| [29] | TONG F, YAN Z.A Hybrid Approach of Mobile Malware Detection in Android[J]. Journal of Parallel and Distributed Computing, 2017, 103(5): 22-31. |
| [30] | YAN P, YAN Z.A Survey on Dynamic Mobile Malware Detection[J]. Software Quality Journal, 2018, 26(3): 891-919. |
| [1] | Yuan LIU, Wei QIAO. Research and Optimization of Container Network Based on Kubernetes Cluster System in Cloud Environment [J]. Netinfo Security, 2020, 20(3): 36-44. |
| [2] | Jiameng BAI, Yingshuai KOU, Zeyi LIU, Daren ZHA. Docker-based RBAC Task Management System [J]. Netinfo Security, 2020, 20(1): 75-82. |
| [3] | REN Liangqin, WANG Wei, WANG Qiongxiao, LU Linli. A New Cloud Cryptographic Computing Platform Architecture and Implementation [J]. Netinfo Security, 2019, 19(9): 91-95. |
| [4] | YU Yi, LV Liangshuang, LI Xiaojian, WANG Tianbo. Dynamic Network Topology Description Language for Mobile Cloud Computing Scenario [J]. Netinfo Security, 2019, 19(9): 120-124. |
| [5] | WANG Zixuan, LV Liangshuang, LI Xiaojian, WANG Tianbo. A Shared Storage-based Virtual Machine Application Distribution Strategy for OpenStack [J]. Netinfo Security, 2019, 19(9): 125-129. |
| [6] | LIU Yuling, TANG Yunshan, ZHANG Qi, LI Feng. Power Dispatch Software Security Situation Assessment Method [J]. Netinfo Security, 2019, 19(8): 15-21. |
| [7] | GE Xinrui, CUI Wei, HAO Rong, YU Jia. Verifiable Keywords Ranked Search Scheme over Encrypted Cloud Data [J]. Netinfo Security, 2019, 19(7): 82-89. |
| [8] | Chunqi TIAN, Jing LI, Wei WANG, Liqing ZHANG. A Method for Improving the Performance of Spark on Container Cluster Based on Machine Learning [J]. Netinfo Security, 2019, 19(4): 11-19. |
| [9] | Pu ZHAO, Wei CUI, Rong HAO, Jia YU. A Secure Outsourcing Computation Scheme for El-Gamal Signature Generation [J]. Netinfo Security, 2019, 19(3): 81-86. |
| [10] | Zhenfeng ZHANG, Zhiwen ZHANG, Ruichao WANG. Model of Cloud Computing Security and Compliance Capability for Classified Protection of Cybersecurity 2.0 [J]. Netinfo Security, 2019, 19(11): 1-7. |
| [11] | FENG Xinyang, SHEN Jianjing. A Yarn and NMF Based Big Data Clustering Algorithm [J]. 信息网络安全, 2018, 18(8): 43-49. |
| [12] | TAO Yuan, HUANG Tao, ZHANG Mohan, LI Shuilin. Research and Development Trend Analysis of Key Technologies for Cyberspace Security Situation Awareness [J]. 信息网络安全, 2018, 18(8): 79-85. |
| [13] | ZHANG Qi, LIN Xijun, QU Haipeng. Identity-based Encryption Scheme Support Authorization Equality Test in Cloud Environment [J]. 信息网络安全, 2018, 18(6): 52-60. |
| [14] | ZHANG Jianbiao, YANG Shisong, TU Shanshan, WANG Xiao. Research on vTPCM Trust Management Technology for Cloud Computing Environment [J]. 信息网络安全, 2018, 18(4): 9-14. |
| [15] | CHEN Yan, GE Jianyong, LAI Jing, LU Zhen. Security System of the Information System in the Cloud [J]. 信息网络安全, 2018, 18(4): 79-86. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||