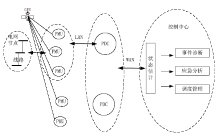
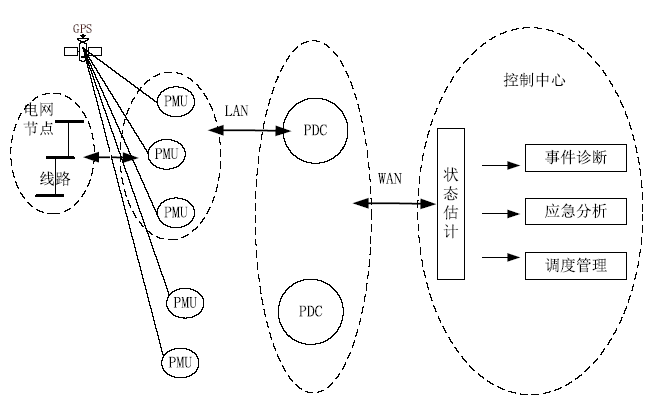
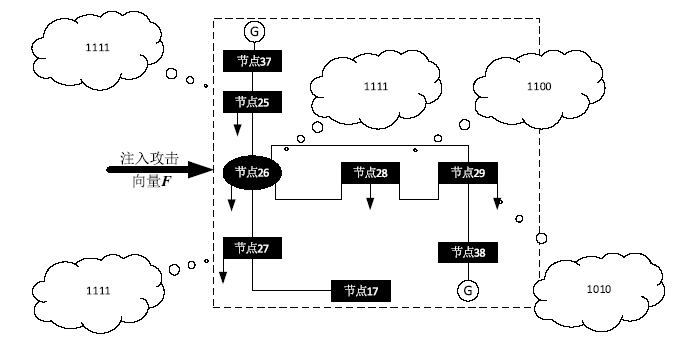
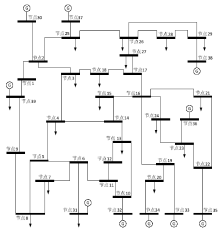
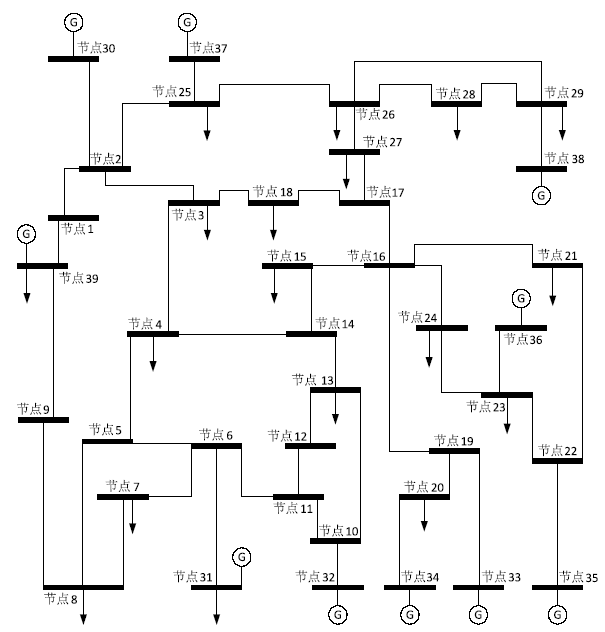
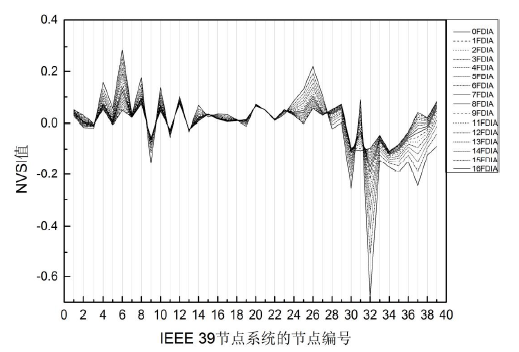
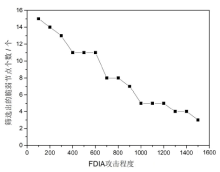
Netinfo Security ›› 2019, Vol. 19 ›› Issue (4): 29-36.doi: 10.3969/j.issn.1671-1122.2019.04.004
Previous Articles Next Articles
False Data Intrusion Detection Method Based on Physical Information in Power Network
Zhuoqun XIA1,2,3( ), Youyou ZENG2, Bo YIN1,2, Ming XU3
), Youyou ZENG2, Bo YIN1,2, Ming XU3
- 1. Hunan Provincial Key Laboratory of Intelligent Processing of Big Data on Transportation, Changsha University of Science and Technology, Changsha Hunan 410114, China
2. School of Computer and Communication Engineering, Changsha University of Science and Technology, Changsha Hunan 410114, China
3. School of Computer, National University of Defense Technology, Changsha Hunan 410073, China
-
Received:2018-10-15Online:2019-04-10Published:2020-05-11
CLC Number:
Cite this article
Zhuoqun XIA, Youyou ZENG, Bo YIN, Ming XU. False Data Intrusion Detection Method Based on Physical Information in Power Network[J]. Netinfo Security, 2019, 19(4): 29-36.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.04.004
| (1)断1条线路 | (2)断2条线路 | (3)断3条线路 | ||||||
|---|---|---|---|---|---|---|---|---|
| LOF | 节点编号 | NVSI | LOF | 节点编号 | NVSI | LOF | 节点编号 | NVSI |
| 40.713 | 14 | 1.183 | 44.852 | 14 | 1.377 | 41.843 | 14 | 1.380 |
| 30.447 | 4 | 0.894 | 28.676 | 16 | 0.896 | 34.340 | 25 | 1.141 |
| 1.921 | 39 | 0.082 | 25.017 | 4 | 0.788 | 27.344 | 16 | 0.918 |
| 1.607 | 12 | 0.074 | 20.199 | 17 | 0.645 | 23.213 | 4 | 0.787 |
| 1.552 | 29 | 0.072 | 1.876 | 39 | 0.079 | 19.913 | 26 | 0.679 |
| 1.529 | 8 | 0.071 | 1.790 | 8 | 0.077 | 18.215 | 17 | 0.625 |
| 1.284 | 20 | 0.065 | 1.748 | 12 | 0.075 | 1.609 | 39 | 0.079 |
| 1.27 | 5 | -0.007 | 1.652 | 29 | 0.072 | 1.556 | 3 | -0.006 |
| [1] | LIANG Gaoqi, ZHAO Junhua, LUO Fengji, et al.A Review of False Data Injection Attacks Against Modern Power Systems[J]. IEEE Transactions on Smart Grid, 2017, 8(4): 1630-1638. |
| [2] | CUI Shuguang, HAN Zhu, KAR S, et al.Coordinated Data-injection Attack and Detection in the Smart Grid: A Detailed Look at Enriching Detection Solutions[J]. IEEE Signal Processing Magazine, 2012, 29(5): 106-115. |
| [3] | WANG Yi, AMIN M M, FU Jian, et al.A Novel Data Analytical Approach for False Data Injection Cyber-Physical Attack Mitigation in Smart Grids[J]. IEEE Access, 2017(5): 26022-26033. |
| [4] | PAL S, SIKDAR B, CHOW J H.Classification and Detection of PMU Data Manipulation Attacks Using Transmission Line Parameters[J]. IEEE Transactions on Smart Grid, 2017, 9(5): 5057-5066. |
| [5] | LIU Yao, NING Peng, REITER M K.False Data Injection Attacks against State Estimation in ElectricPower Grids[J]. ACM Transactions on Information and System Security, 2011, 14(1): 21-32. |
| [6] | CHEN Poyu Y, YANG Shusen, MCCANN J A, et al.Detection of False Data Injection Attacks in Smart-grid Systems[J]. IEEE Communications Magazine, 2015, 53(2): 206-213. |
| [7] | XIA Zhuoqun, ZOU Fengfei, XU Ming, et al.Research on Defensive Strategy of Real-time Price Attack Based on Zero-determinant[J]. Netinfo Security, 2017, 17(11): 25-31. |
| 夏卓群,邹逢飞,徐明,等. 基于零行列式的实时电价攻击防御策略研究[J]. 信息网络安全,2017,17(11):25-31. | |
| [8] | ESMALIFALAK M, LIU Lanchao, NGUYEN N, et al.Detecting Stealthy False Data Injection Using Machine Learning in Smart Grid[J]. IEEE Systems Journal, 2017, 11(3): 1644-1652. |
| [9] | AHMED S, LEE Y D, HYUN S H, et al.Feature Selection-Based Detection of Covert Cyber Deception Assaults in Smart Grid Communications Networks using Machine Learning[J]. IEEE Access, 2018(6): 27518-27529. |
| [10] | HE Youbiao, MENDIS G J, WEI Jin.Real-time Detection of False Data Injection Attacks in Smart Grid: A Deep Learning-Based Intelligent Mechanism[J]. IEEE Transactions on Smart Grid, 2017, 8(5): 2505-2516. |
| [11] | ASHOK A, GOVINDARASU M, AJJARAPU V.Online Detection of Stealthy False Data Injection Attacks in Power System State Estimation[J]. IEEE Transactions on Smart Grid, 2018, 9(3): 1636-1646. |
| [12] | GUAN Zhitao, AN P, YANG Tingting.Matrix Partition-based Detection Scheme for False Data Injection in Smart Grid[J]. International Journal of Wireless and Mobile Computing, 2015, 9(3): 250-256. |
| [13] | XU Ruzhi, WANG Rui, GUAN Zhitao, et al.Achieving EfficientDetection against False Data Injection Attacks in Smart Grid[J]. IEEE Access, 2017(5): 13787-13798. |
| [14] | LI Beibei, LU Rongxing, WANG Wei, et al.Distributed Host-based Collaborative Detection for False Data Injection Attacks in Smart Grid Cyber-physical System[J]. Journal of Parallel & Distributed Computing, 2016, 103(C): 32-41. |
| [15] | REN Wei, ZHAO Junge.Security Architecture and Analysis of Smart Grid[J].Netinfo Security, 2012, 12(8): 178-181. |
| 任伟,赵俊阁. 智能电网安全架构与分析[J]. 信息网络安全,2012,12(8):178-181. | |
| [16] | HAZARIKA D.New Method for Monitoring Voltage Stability Condition of a Bus of an Interconnected Power System Using Measurements of the Bus Variables[J]. Iet Generation Transmission & Distribution, 2012, 6(10): 977-985. |
| [17] | ZIMMERMAN R D, MURILLO-SANCHEZ C E, THOMAS R J. MATPOWER: Steady-State Operations, Planning, and Analysis Tools for Power Systems Research and Education[J]. IEEE Transactions on Power Systems, 2011, 26(1): 12-19. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||