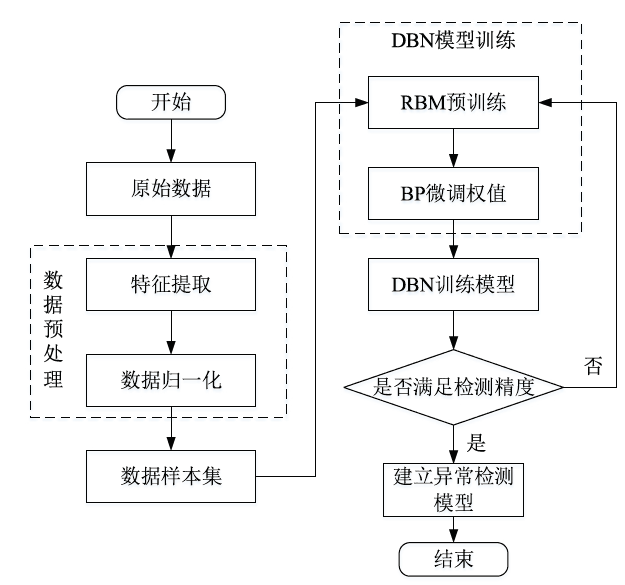
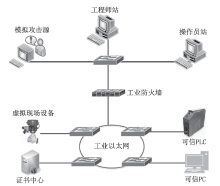
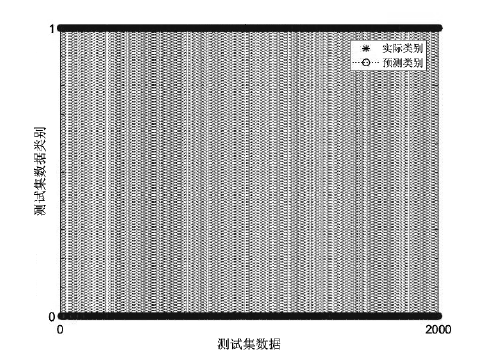
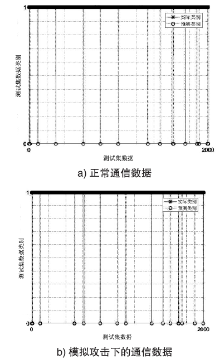
| [1] |
XIA Chunming, LIU Tao, WANG Huazhong, et al.Industrial Control System Security Analysis[J].Information Security and Technology, 2013, 4(2): 13-18.
|
|
夏春明,刘涛,王华忠,等. 工业控制系统信息安全现状及发展趋势[J]. 信息安全与技术,2013,4(2):13-18.
|
| [2] |
WANG Xiaoshan, YANG An, SHI Zhiqiang,et al.New Trend of Information Security in Industrial Control Systems[J]. Netinfo Security, 2015, 15(1): 6-11.
|
|
王小山,杨安,石志强,等. 工业控制系统信息安全新趋势[J]. 信息网络安全,2015,15(1):6-11.
|
| [3] |
SP800-82.Guide to Industrial Control System(ICS) SecuritySP800-82.Guide to Industrial Control System(ICS) Security[S]. Gaithersburg: National Institute of Standards and Technology, 2010.
|
|
SP800-82.工业控制系统安全指南SP800-82.工业控制系统安全指南[S]. 盖瑟斯堡:美国国家标准与技术研究院,2010.
|
| [4] |
WAN Ming, SHANG Wenli, ZHAO Jianming, et al.Trusted Security Defense Architecture for Industrial Embedded Device[J]. Instrument Standardization & Metrolog, 2015, 6: 18-21.
|
|
万明,尚文利,赵剑明,等. 面向工业嵌入式设备的可信安全防护体系[J]. 仪器仪表与标准化计量,2015,6:18-21.
|
| [5] |
SHAO Cheng, ZHONG Lianggao.An Information Security Solution Scheme of Industrial Control System Based on Trusted Computing[J]. Information and Control, 2015, 44(5): 628-633.
|
|
邵诚,钟梁高. 一种基于可信计算的工业控制系统信息安全解决方案[J]. 信息与控制,2015,44(5):628-633.
|
| [6] |
TSAI C F, HSU Y F, LIN C Y, et al.Intrusion Detection by Machine Learning: A Review[J]. Expert System with Applications, 2009, 36(10): 11994-12000.
|
| [7] |
ZHANG Shengshan, SHANG Wenli, WAN Ming.Security Defense Module of Modbus TCP Communication Based on Region/Enclave Rules[J]. Computer Engineering and Design, 2014, 35(11): 3701-3707.
|
|
张盛山,尚文利,万明,等. 基于区域/边界规则的Modbus TCP通讯安全防御模型[J]. 计算机工程与设计,2014,35(11):3701-3707.
|
| [8] |
SHEN Changxiang, ZHANG Huanguo, WANG Huaimin, et al.Research and Development of Trusted Computing[J]. SCIENTIA SINICA Informationis, 2010(2): 139-166.
|
|
沈昌祥,张焕国,王怀民,等. 可信计算的研究与发展[J]. 中国科学:信息科学, 2010(2):139-166.
|
| [9] |
QIAO Xinxiao, JIA Zhiping.Automation Monitoring and Control System Based on Modbus/TCP Protocol[J]. Computer Engineering, 2004(8): 181-182.
|
|
乔新晓,贾智平. 基于Modbus/TCP的自动化监控系统[J]. 计算机工程,2004(8):181-182.
|
| [10] |
PU Chunyan.Design and Research of Modbus/Modbus_TCP Gateway[J]. China CIO News, 2018(1): 158-159.
|
|
蒲春燕. Modbus/Modbus_TCP网关的设计与研究[J]. 信息系统工程,2018(1):158-159.
|
| [11] |
DRURY B. Control Techniques, Drives and Controls Handbook[EB/OL]. , 2018-12-25.
|
| [12] |
ZUO Wei, CHENG Yongxin.Principle and Security Analysis of Modbus Protocol[J]. Communications Technology, 2013, 46(12): 66-69.
|
|
左卫,程永新. Modbus协议原理及安全性分析[J]. 通信技术,2013,46(12):66-69.
|
| [13] |
ZHANG Chunxia, JI Nannan, WANG Guanwei.Restricted Boltzmann Machines[J]. Chinese Journal of Engineering Mathematics, 2015(2): 159-173.
|
|
张春霞,姬楠楠,王冠伟. 受限波尔兹曼机[J]. 工程数学学报,2015(2):159-173.
|
| [14] |
YIN Wenye, HE Weiji, GU Guohua, et al.A New Full Waveform Analysis Approach Using Simulated Tempering Markov Chain MonteCarlo Method[J]. Acta Physica Sinica, 2014, 63(16): 198-204.
|
|
尹文也,何伟基,顾国华,等. 模拟回火马尔可夫链蒙特卡罗全波形分析方法[J]. 物理学报,2014,63(16):198-204.
|
| [15] |
HINTON G E.Training Products of Experts by Minimizing Contrastive Divergence[J]. Neural Computation, 2002, 14(8): 1771-1800.
|
| [16] |
HINTON G E.A Practical Guide to Training Restricted Boltzmann Machines.[J]. Momentum, 2012, 9(1): 599-619.
|
| [17] |
HINTON G E, OSINDERO S, TEH Y W.A Fast Learning Algorithm for Deep Belief Nets[J]. Neural Computation, 2006, 18(7): 1527-1554.
|
| [18] |
MITCHELL R, Chen I R.A Survey of Intrusion Detection Techniques for Cyber-physical Systems[J]. ACM Computing Surveys (CSUR), 2014, 46(4): 55.
|
| [19] |
WANG Gongcong, WANG Jingzhong, WANG Baocheng.A New Detection Method of Abnormal Network Behavior based on the Packet Content[J]. Netinfo Security, 2013, 13(12): 58-61.
|
|
王功聪,王景中,王宝成.基于数据包内容的网络异常行为分析方法研究[J].信息网络安全,2013,13(12):58-61.
|
| [20] |
SHANG Wenli, ZHANG Shengshan, WAN Ming, et al.Modbus TCP Communication Anomaly Detection Algorithm Based on PSO-SVM[J]. Acta Electronica Sinica, 2014, 42(11): 2314-2320.
|
|
尚文利,张盛山,万明,等. 基于PSO-SVM 的Modbus TCP通讯的异常检测方法[J]. 电子学报,2014,42(11):2314-2320.
|
 ), Xiule ZHANG1,2,3,4, Xianda LIU1,3,4,5, Long YIN1,3,4,5
), Xiule ZHANG1,2,3,4, Xianda LIU1,3,4,5, Long YIN1,3,4,5