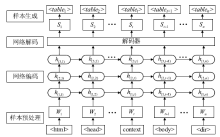
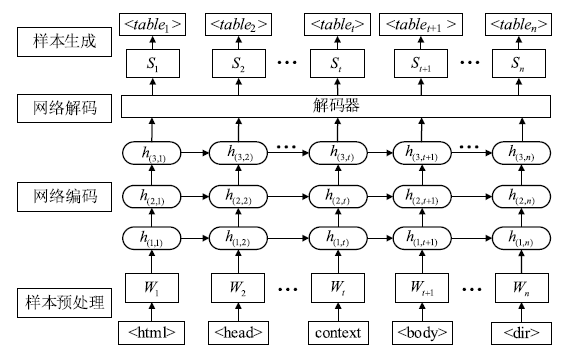
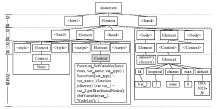
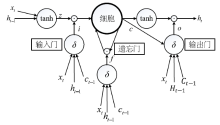
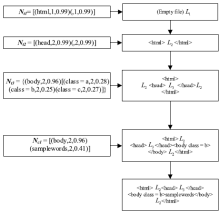
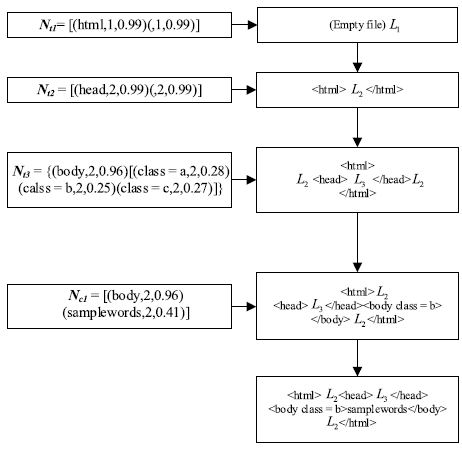
| [1] |
WANG xiajing,HU changzhen,MA rui. A Survey of Key techniques of Binary Program Vulnerability Discovery[J]. Netinfo Security, 2017, 17(8): 1-13.
|
|
王夏菁,胡昌振,马锐,等.二进制程序漏洞挖掘关键技术研究综述[J].信息网络安全,2017,17(8):1-13.
|
| [2] |
PANG Y, XUE X, NAMIN A S.Early Identification of Vulnerable Software Components via Ensemble Learning[C]// IEEE. 15th IEEE International Conference on Machine Learning and Applications(ICMLA), December 18-20, 2016, Los Angeles, California, USA. New York: IEEE, 2017: 476-481.
|
| [3] |
PANG Y, XUE X, NAMIN A S.Predicting Vulnerable Software Components through N-Gram Analysis and Statistical Feature Selection[C]// IEEE. 14th International Conference on Machine Learning and Applications (ICMLA), December 4 -7, 2013, Miami, Florida, USA. New York: IEEE, 2015:543-548.
|
| [4] |
WEN weiping, WU bozhi, JIAO yingnan, et al. Design and Implementation on Malicious Document Detection Tool Based on Machine Learning[J]. Netinfo Security, 2018, 18(8): 1-7.
|
|
文伟平,吴勃志,焦英楠,等.基于机器学习的恶意文档识别工具设计与实现[J].信息网络安全,2018,18(8):1-7.
|
| [5] |
GODEFROID P, PELEG H, SINGH R.Learn&Fuzz: Machine Learning for Input Fuzzing[C]// IEEE. 32nd IEEE/ACM International Conference on Automated Software Engineering, October 30-November 3, 2017, Urbana-Champaign, IL, USA, New York: IEEE, 2017: 50-59.
|
| [6] |
WANG J, CHEN B, WEI L, et al.Skyfire: Data-Driven Seed Generation for Fuzzing[C]//IEEE. 38th IEEE Symposium on Security and Privacy, May 22-24, 2017, San Jose, California, USA. New York: IEEE, 2017: 579-594.
|
| [7] |
WU Fang, A Study of Binary Vulnerability Analysis and Detection Based on Deep Leraning[D]. Beijing: Beijing Jiaotong University, 2018.
|
|
吴芳. 基于深度学习的二进制程序漏洞分析与检测方法研究[D].北京:北京交通大学,2018.
|
| [8] |
SUNDERMEYER M,SCHLÜTER R,NEY H. LSTM Neural Networks for Language Modeling[C]//INTERSPEECH. 13th Annual Conference of the International Speech Communication Association, September 9-13, 2012, Portland, Oregon, USA. New York: 2012: 601-608.
|
| [9] |
KALCHBRENNER N, GREFENSTETTE E,BLUNSOM P. A Convolutional Neural Network for Modelling Sentences[EB/OL]. .
|
| [10] |
PALANGI H, DENG L, SHEN Y, et al.Deep Sentence Embedding Using Long Short-Term Memory Networks: Analysis and Application to Information Retrieval[J]. ACM Transactions on Audio Speech & Language Processing, 2016, 24(4): 694-707.
|
| [11] |
BENGIO Y, SIMARD P, FRASCONI P.Learning Long-term Dependencies with Gradient Descent is Difficult[J]. IEEE Transactions on Neural Networks, 2002, 5(2):157-166.
|
| [12] |
BELTRAMELLI T.Pix2code: Generating Code from a Graphical User Interface Screenshot[C]//EICS. ACM SIGCHI Symposium on Engineering Interactive Computing Systems, June 26-29, 2017, Lisbon, Portugal. New York: ACM, 2018: 3.
|
| [13] |
NIEPERT M, AHMED M, KUTZKOV K.Learning Convolutional Neural Networks for Graphs[C]//ICML. 33rd International conference on machine learning, June 19 - 24, 2016, New York City, NY, USA. New York: ICML, 2016: 2014-2023.
|
| [14] |
GRAVES A. Generating Sequences With Recurrent Neural Networks[EB/OL]. , 2013-8-4.
|
| [15] |
SHE D, PEI K, EPSTEIN D, et al. NEUZZ: Efficient Fuzzing with Neural Program Learning[EB/OL]., 2018-7-15.
|
| [16] |
RAJPAL M, BLUM W, SINGH R. Not all Bytes are Equal: Neural Byte Sieve for Fuzzing[EB/OL]., 2017-11-10.
|
| [17] |
BÖTTINGER K, GODEFROID P, SINGH R. Deep Reinforcement Fuzzing[C]//IEEE. IEEE Security and Privacy Workshops (SPW), May 24, 2018, San Francisco, CA, USA. New York: IEEE, 2018: 116-122.
|
| [18] |
HUANG Yi.Research on Software Security Vulnerability Discovery Based on Fuzzing[D]. Hefei: University of Science and Technology of China, 2010.
|
|
黄奕. 基于模糊测试的软件安全漏洞发掘技术研究[D].合肥:中国科学技术大学,2010.
|
 ), Luping LIU2, Peng JIA2
), Luping LIU2, Peng JIA2