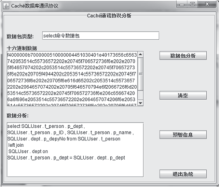
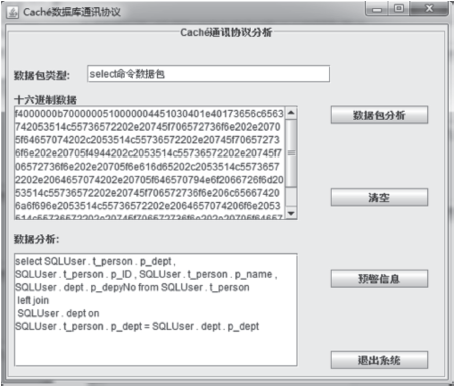
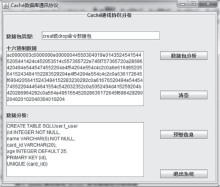
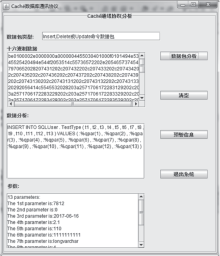
| [1] |
SMIRNOV A, LAM L, CHIUEH T. Portable Intrusion-Resilient Database Management Server[EB/OL]., 2006-3-20.
|
| [2] |
GUO L, WU H. Design and Implementation of TDS Protocol Analyzer[EB/OL]., 2009-8-11.
|
| [3] |
JIN S, LI M, WANG Z. Research and Design of Preprocessor Plugin Based on PCRE under Snort Platform[EB/OL]., 2011-7-1.
|
| [4] |
WU K, HUA L, WANG X, et al. The Design and Implementation of Database Audit System Framework[EB/OL]., 2014-10-23.
|
| [5] |
OTTE L, DANEL R, ŘEPKA M, et al. Comparison of Database Mirror Technologies for Use in Fault-Tolerant Information System Solutions[EB/OL]., 2015-7-2.
|
| [6] |
DANEL R, KOZEL R, JOHANIDES D, et al.Database Mirroring in Fault-Tolerant Continuous Technological Process Control[J]. Metalurgija, 2016, 55(1): 83-86.
|
| [7] |
PRABAKAR M A, KARTHIKEYAN M, MARIMUTHU K. An Efficient Technique for Preventing SQL Injection Attack Using Pattern Matching Algorithm[EB/OL]., 2013-6-13.
|
| [8] |
QING Sihan.Security Protection of Critical Infrastructure[J]. Netinfo Security,2015(2):1-6.
|
|
卿斯汉. 关键基础设施安全防护[J]. 信息网络安全,2015(2):1-6.
|
| [9] |
SHAO Z, LI Y, ZHANG K, et al. An Audit Method Based on Mathematical Statistics Detection in Database Audit System[EB/OL]., 2015-11-23.
|
| [10] |
ZHANG Jianbiao, ZHAO Zixiao, HU Jun, et al.The Design Framework of Reconfigurable Virtual Root of Trust in Cloud Environment[J]. Netinfo Security, 2018(1): 1-8.
|
|
张建标, 赵子枭, 胡俊, 等. 云环境下可重构虚拟可信根的设计框架[J]. 信息网络安全, 2018(1): 1-8.
|
| [11] |
SHI J, YAO J, LIU M. Research on Database Audit Scheme Design of Life Insurance Industry Based on OLAP Technology[EB/OL]., 2017-2-16.
|
| [12] |
WEN Weiping, GUO Ronghua, MENG Zheng, et al.Research and Implementation on Information Security Risk Assessment Key Technology[J]. Netinfo Security, 2015 (2): 7-14.
|
|
文伟平,郭荣华,孟正,等. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全,2015(2):7-14.
|
 ), Xiaolin CHANG, Zhen HAN
), Xiaolin CHANG, Zhen HAN