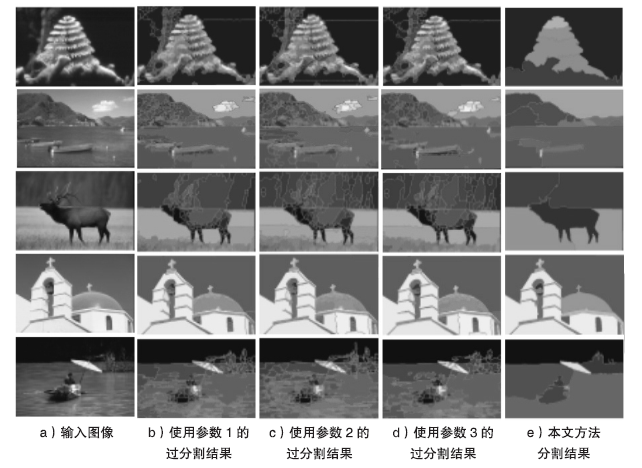
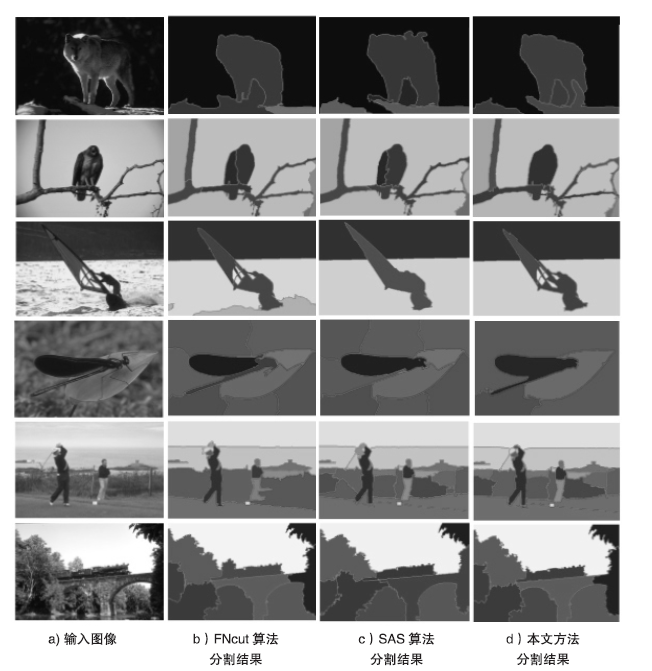
Netinfo Security ›› 2018, Vol. 18 ›› Issue (12): 8-14.doi: 10.3969/j.issn.1671-1122.2018.12.002
Previous Articles Next Articles
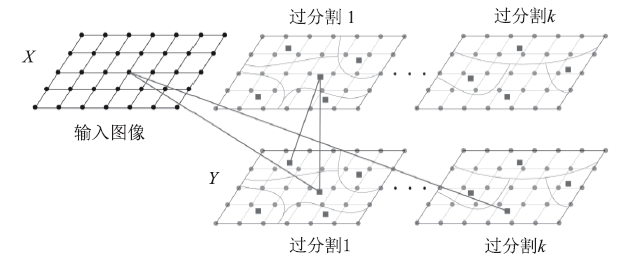
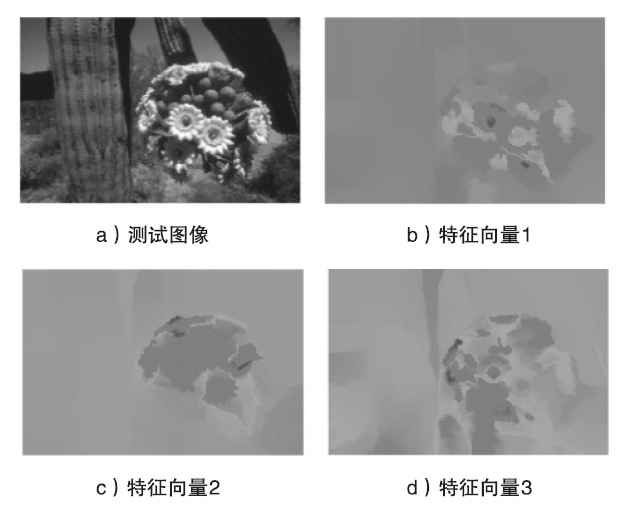
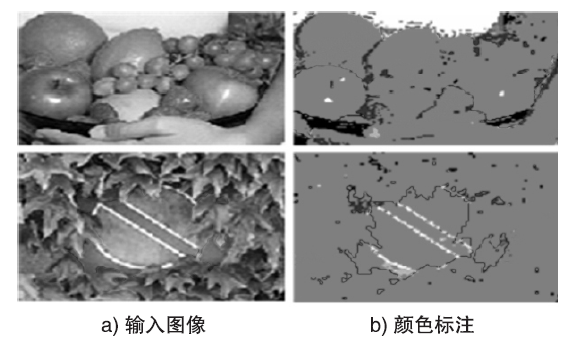
Spectral Clustering Bipartite Graph Segmentation Method Based on Color Invariant Features
Wei ZHAO1,2,3, Na ZHAO1( ), Yixing ZHANG4
), Yixing ZHANG4
- 1. College of Computer, National University of Defense Technology, Changsha Hunan 410073, China
2.Department of Information Technology, Hunan Police Academy, Changsha Hunan 410073, China
3.Key Laboratory of Network Crime Investigation, Colleges of Human Province, Changsha Hunan 410073,China
4.Xiangzhou Brigade, Network Police Detachment of Zhuhai Public Security Bureau, Zhuhai Guangdong 519000,China
-
Received:2018-09-25Online:2018-12-20Published:2020-05-11
CLC Number:
Cite this article
Wei ZHAO, Na ZHAO, Yixing ZHANG. Spectral Clustering Bipartite Graph Segmentation Method Based on Color Invariant Features[J]. Netinfo Security, 2018, 18(12): 8-14.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2018.12.002
| [1] | COMANICIU D, MEER P.Mean shift: A Robust Approach toward Feature Space Analysis[J]. Pattern Analysis and Machine Intelligent, 2002,5(7): 603-619. |
| [2] | ZHAO Feng, FAN Jiulun, ZHI Xiaobin, et al.Spatial and Gray Feature-based Spectral Clustering for Image Segmentation[J].Journal of Xi’an Institute of Posts and Telecommunications, 2012, 17(1):53-57. |
| 赵凤,范九伦,支晓斌,等.基于灰度和空间特性的谱聚类图像分割[J]. 西安邮电学院学报, 2012, 17(1):53-57. | |
| [3] | LI Zhengguo, WU Xiaoming, CHANG S F.Segmentation Using Superpixels: A Bipartite Graph Partitioning Approach[C]// IEEE.2012 IEEE Conference on Computer Vision and Pattern Recognition, June 16-21, 2012, Providence, RI, USA.NJ:IEEE, 2012: 789-796. |
| [4] | KIM T H, LEE M, LEE S U.Learning Full Pairwise Affinities for Spectral Segmentation[J]. Pattern Analysis and Machine Intelligent, 2013, 35(7):1690-1730. |
| [5] | YIN Fang, CHEN Deyun, WU Rui.Improved Method of Image Segmentation Using Spectral Clustering[J]. Computer Engineering and Applications,2011,47(21):185-187. |
| 尹芳,陈德云,吴锐.改进的谱聚类图像分割方法[J].计算机工程与应用,2011,47(21):185-187. | |
| [6] | GAO Shangbing, ZHOU Jingbo, YAN Yunyang.A New Superpixel-based Spectral Clustering for Image Segmentation[J].Journal of Nanjing University: Natural Sciences,2013,49(2):169-175. |
| 高尚兵,周静波,严云洋.一种新的基于超像素的谱聚类图像分割算法[J].南京大学学报:自然科学版,2013,49(2):169-175. | |
| [7] | BOYKOVY,FUUKA-LEA G. Graph Cuts and Efficient N-D Image Segmentation[J].Journal of Computer Vision, 2006, 70(2): 109-131. |
| [8] | GAO Hongtao, LU Wei, YANG Yuwang.An Adaptive Adjusting Kernel Function-Based Extraction Method for Image Salient Area[J].Netinfo Security,2018,18(2):54-60. |
| 高洪涛,陆伟,杨余旺.基于自适应调节核函数的图像显著区域提取方法[J].信息网络安全,2018,18(2):54-60. | |
| [9] | SERRA M, PENACCHIO O, BENAVENTE R, et al.Names and Shades of Color for Intrinsic Image Estimation[C]// IEEE.2012 IEEE Conference on Computer Vision and Pattern Recognition, June 16-21, 2012, Providence, RI, USA.NJ:IEEE, 2012: 278-285. |
| [10] | KIM T H, Lee K M, LEE S U.Learning Full Pairwise Affinities for Spectral Segmentation[C]// IEEE. 2010 IEEE Computer Society Conference on Computer Vision and Pattern Recognition, June 13-18, 2010, SanFrancisco, CA, USA.NJ:IEEE,2010: 789-796. |
| [11] | VAZQUEZ E, Baldrich R, WEIJER J V D,et al. Describing Reflectances for Colour Segmentation Robust to Shadows, Highlights and Textures[J]. Pattern Analysis and Machine Intelligent, 2007, 6(1):1-15. |
| [12] | NG A Y, JORDAN M I, WEISS Y.On Spectral Clustering: Analysis and an Algorithm[C]//NIPS. The 14th International Conference on Neural Information Processing Systems: Natural and Synthetic, December 3 - 8, 2001, Vancouver, British Columbia, Canada. Cambridge: MIT Press , 2001:849-856. |
| [13] | YAO Xiaoyu, MA Hui, LIAN Zhe.A Method of Anti-Antivirus Based on Feature Decomposition[J]. Netinfo Security, 2012,12(4):43-46. |
| 姚晓宇,马辉,廉喆.基于特征分解的免杀方法研究[J].信息网络安全, 2012,12(4):43-46. | |
| [14] | BERLIN B, KAY P.Basic Color Term: Their University and Evolution [M]. Berkeley: University of California Press, 1969. |
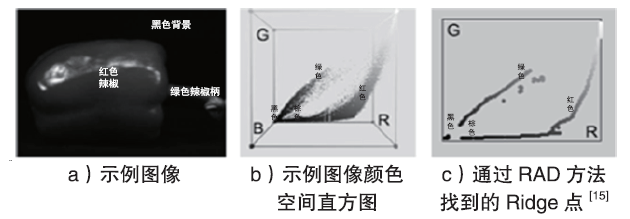
| [15] | UNNIKRISHNAN R, PANTOFARU C, Hebert M.Toward Objective Evaluation of Image Segmentation Algorithms[J]. Pattern Analysis and Machine Intelligent, 2007, 29(6):929-944. |
| [16] | MARTIN D, FOWLKES C, TAL D, et al.A Database of Human Segmented Natural Images and Its Application to Evaluating Segmentation Algorithms and Measuring Ecological Statistics[C]// IEEE. The 8th IEEE International Conference on Computer Vision, July 7-14, 2001,Vancouver, BC, Canada.NJ:IEEE,2001: 416-423. |
| [17] | COUR T, BENEZIT F, SHI Jianbo.Spectral Segmentation with Multiscale Graph Decomposition[C]// IEEE. 2005 IEEE Computer Society Conference on Computer Vision and Pattern Recognition, June 20-25, 2005, San Diego, CA, USA.NJ:IEEE,2005:24-32. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||