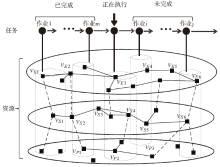
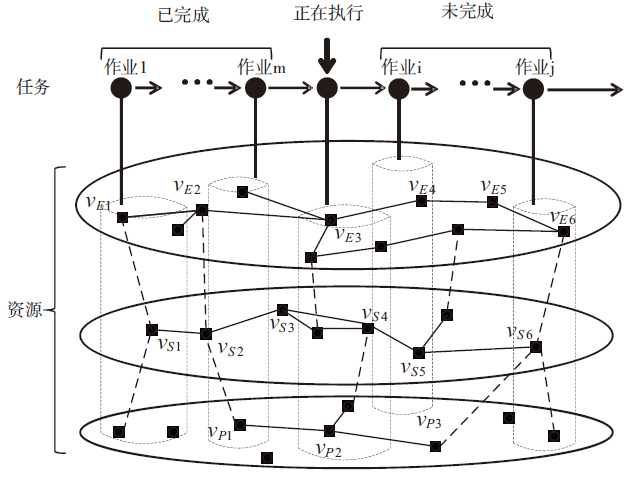
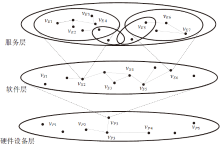
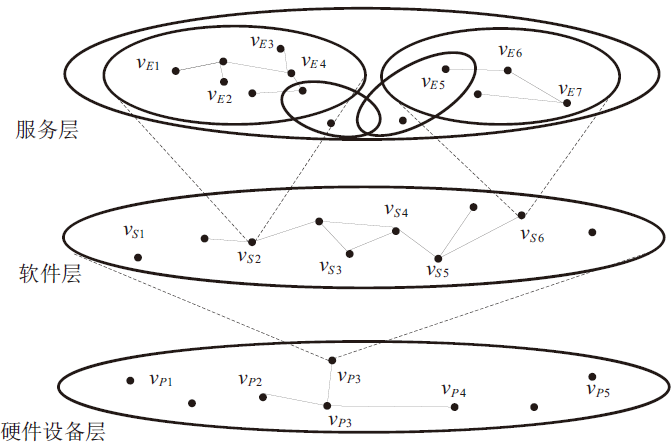
| [1] |
HAFNER K, MARKOFF J.Cyberpunk: Outlaws and Hackers on the Computer Frontier[M].NewYork:Simon & Schuster, 1991.
|
| [2] |
段彬,韩伟红,李爱平. 网络蠕虫危害性的量化评估模型研究[J].信息网络安全,2016(6):41-47.
|
| [3] |
COLIN C.Adversaries Outpace US In Cyber War; Acquisition Still Too Slow [EB/OL]., 2016-6-15.
|
| [4] |
郑江波,张建华. 智慧城市中信息安全架构研究与设计[J].信息网络安全,2016(1):88-93.
|
| [5] |
BUNKER R J.Fifth Dimensional Operations: Space-Time-Cyber Dimensionality in Conflict and War—A Terrorism Research Center Book[M]. Bloomington: iUniverse, 2014.
|
| [6] |
陈晓兵,陈凯,徐震,等. 面向工业控制网络的安全监管方案[J].信息网络安全,2016(7):61-70.
|
| [7] |
KAKADIA D, ,2015-10-13.
|
| [8] |
褚灵伟, 邹仕洪, 程时端,等. 概率和噪声环境下基于主动探针的Internet服务故障管理[J]. 中国科学, 2008, 38(10):1733-1746.
|
| [9] |
刘建辉, 王凤梅, 寇雪琴. 工程机械的层次模型协同诊断方法[J]. 计算机测量与控制, 2006, 14(8):1016-1017.
|
| [10] |
CLARK A, ALOMAIR B, BUSHNELL L, et al.Input Selection for Disturbance Rejection in Networked Cyber-physical Systems[C]//Decision and Control (CDC), 2015 IEEE 54th Annual Conference,December 15-18 ,2015, Osaka. New York:IEEE, 2015: 954-961.
|
| [11] |
SCALA A, LUCENTINI P G D S. The Equal Load-sharing Model of Cascade Failures in Power Grids[J]. Physica A: Statistical Mechanics and its Applications ,2016,462(11): 737-742.
|
| [12] |
安若铭, 杨峰, 孔翔,等. 导弹电源系统故障诊断实验[J]. 实验技术与管理, 2012, 29(7):92-95.
|
| [13] |
LIU W Y, TANG B P, HAN J G, et al.The Structure Healthy Condition Monitoring and Fault Diagnosis Methods in Wind Turbines: A review[J]. Renewable and Sustainable Energy Reviews, 2015, 44: 466-472.
|
| [14] |
KING D, FARREL A. A PCE-based Architecture for Application-based Network Operations[EB/OL]. ,2016-6-15.
|
| [15] |
BERGEerge C.Graphs and Hypergraphs[M]. Amsterdam: North-Holland publishing company, 1973.
|
| [16] |
Berge C.Hypergraphs: combinatorics of finite sets[M]. North Holland :Elsevier, 1984.
|
| [17] |
ZHANG J, YI K, WANG H, et al.Timeliness Optimization Model For Network C4ISR System Structure Based on Information Flow[C]// ASEI2015.3rd International conference on Applied Science and Engineering Innovation,December 24-26, 2015,Beijing. New York:icasei,2015.
|
| [18] |
周芳, 周正虎. C4ISR系统作战业务信息失真效应建模[J].中国电子科学研究院学报, 2015, 10(3):287-292.
|
| [19] |
陈开放,李汇云,刘松,等. 基于DDS舰载通信系统的信息安全分析研究[J].信息网络安全,2016(3):47-52.
|
 ), Hongqi ZHANG2,3, Jin WANG1, Ning WANG1
), Hongqi ZHANG2,3, Jin WANG1, Ning WANG1