Netinfo Security ›› 2017, Vol. 17 ›› Issue (1): 1-7.doi: 10.3969/j.issn.1671-1122.2017.01.001
• Orginal Article • Next Articles
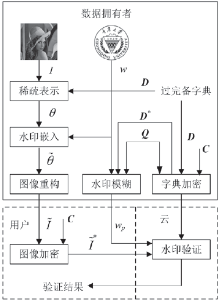
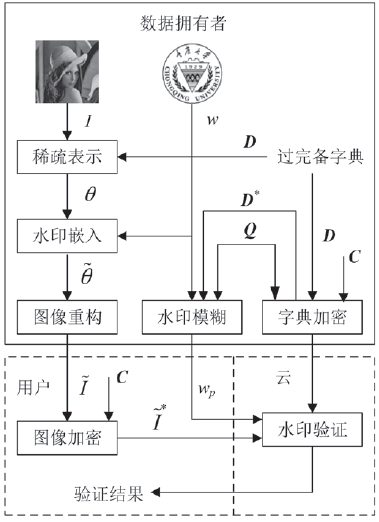
Cloud-assisted Secure Digital Watermarking Based on Sparse Representation
Di XIAO( ), Qingqing MA, Lan WANG, Yanping XIANG
), Qingqing MA, Lan WANG, Yanping XIANG
- College of Computer Science, Chongqing University, Chongqing 400044, China
-
Received:2016-10-28Online:2017-01-20Published:2020-05-12
CLC Number:
Cite this article
Di XIAO, Qingqing MA, Lan WANG, Yanping XIANG. Cloud-assisted Secure Digital Watermarking Based on Sparse Representation[J]. Netinfo Security, 2017, 17(1): 1-7.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2017.01.001
| [1] | WANG Yong, WONG K W, LIAO Xiaofeng, et al.A New Chaos-based Fast Image Encryption Algorithm[J]. Applied Soft Computing, 2011, 11(1): 514-522. |
| [2] | 肖迪,王莹,常燕廷,等. 基于加法同态与多层差值直方图平移的密文图像可逆信息隐藏算法[J]. 信息网络安全,2016(4):9-16. |
| [3] | HUANG C K, NIEN H H.Multi Chaotic Systems Based Pixel Shuffle for Image Encryption[J]. Optics Communications, 2009, 282(11): 2123-2127. |
| [4] | YE Guodong.Image Scrambling Encryption Algorithm of Pixel Bit Based on Chaos Map[J]. Pattern Recognition Letters, 2010, 31(5): 347-354. |
| [5] | XIAO Di, FU Qingqing, XIANG Tao, et al.Chaotic Image Encryption of Regions of Interest[J]. International Journal of Bifurcation and Chaos, 2016, 26(11): 1-15. |
| [6] | COX I J, MILLER M L, BLOOM J A.Digital Watermarking[M]. San Francisco: Morgan Kaufmann Publishers, 2002. |
| [7] | WU Haotian, DUGELAY J L, SHI Yunqing.Reversible Image Data Hiding with Contrast Enhancement[J]. IEEE Signal Processing Letters, 2014, 22(1): 81-85. |
| [8] | PARAH S A, SHEIKH J A, LOAN N A, et al. Robust and Blind Watermarking Technique in DCT Domain Using Inter-block Coefficient Differencing[EB/OL]. , 2016-10-10. |
| [9] | LI Hongyuan, LIU Guangjie, DAI Yuewei, et al.Copyright Protecting Using the Secure Visible Removable Watermarking in JPEG Compression[J]. International Journal of Digital Content Technology & Its Applications, 2010, 4(8): 34-42. |
| [10] | CANDS E J, ROMBERG J, TAO T.Robust Uncertainty Principles: Exact Signal Reconstruction from Highly Incomplete Frequency Information[J]. IEEE Transactions on Information Theory, 2006, 52(2): 489-509. |
| [11] | DONOHO D L.Compressed Sensing[J]. IEEE Transactions on Information Theory, 2006, 52(4): 1289-1306. |
| [12] | CANDS E J, WAKIN M B.An Introduction to Compressive Sampling[J]. IEEE Signal Processing Magazine, 2008, 25(2): 21-30. |
| [13] | 周佳奇. 基于压缩感知的云协助下的水印方法研究[D]. 重庆:重庆大学,2016. |
| [14] | HUA Guang, XIANG Yong, BI Guoan.When Compressive Sensing Meets Data Hiding[J]. IEEE Signal Processing Letter, 2016, 23(4): 473-477. |
| [15] | 肖迪,邓秘密,张玉书. 基于压缩感知的鲁棒可分离的密文域水印算法[J]. 电子与信息学报,2015,37(5):1248-1254. |
| [16] | Donoho L.For Most Large Underdetermined Systems of Linear Programs the Minimal 1 Norm Solution is also the Sparsest Solution[J]. Communications on Pure and Applied Mathematics, 2006, 59(6): 797-829. |
| [17] | 秦志光,包文意,赵洋,等. 云存储中一种模糊关键字搜索加密方案[J]. 信息网络安全,2015(6):7-12. |
| [18] | ZHANG Yushu, XIAO Di, WONG K W, et al.Perturbation Meets Key-based Interval Splitting Arithmetic Coding: Security Enhancement and Chaos Generalization[J]. Security & Communication Networks, 2016, 9(1): 43-53. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||