Netinfo Security ›› 2016, Vol. 16 ›› Issue (7): 53-60.doi: 10.3969/j.issn.1671-1122.2016.07.009
• Orginal Article • Previous Articles Next Articles
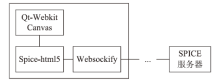
A Performance Testing Framework of Virtual Desktop Based on User Motion Controlling Language
Jingxuan ZHANG1,2,3, Jinda CHANG1,2,3, Dong GUO1,2,3, Wei WANG1,2,3
- 1. Department of Computer Science and Engineering, Tongji University, Shanghai 200092, China
2. Tongji Branch National Engineering & Technology Center of High Performance, Shanghai 200092, China
3. The Key Laboratory of Embedded System and Service Computing, Ministry of Education, Tongji University, Shanghai 200092, China
-
Received:2016-06-02Online:2016-07-20Published:2020-05-13
CLC Number:
Cite this article
Jingxuan ZHANG, Jinda CHANG, Dong GUO, Wei WANG. A Performance Testing Framework of Virtual Desktop Based on User Motion Controlling Language[J]. Netinfo Security, 2016, 16(7): 53-60.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2016.07.009
| [1] | WANG J, LIANG L. Survey of Virtual Desktop Infrastructure System[EB/OL]. https://tools.ietf.org/html/draft-ma-appsawg-vdi-survey-00, 2011-11-14. |
| [2] | SCHMIDT B K, LAM M S, NORTHCUTT J D.The Interactive Performance of SLIM[J]. ACM SIGOPS Operating Systems Review, 1999, 33(5): 32-47. |
| [3] | NIEH J, YANG S J, NOVIK N.A Comparison of Thin-client Computing Architectures[R]. Columbia: Columbia University, Technical Report CUCS-022-00, 2000. |
| [4] | YANG S J, NIEH J, SELSKY M, et al.The Performance of Remote Display Mechanisms for Thin-client Computing[C]//USENIX. General Track of the annual conference on USENIX Annual Technical Conference, June 10-15, 2002, Monterey, California, USA. New York: ACM, 2002: 131-146. |
| [5] | NIEH J, YANG S J, NOVIK N.Measuring Thin-client Performance Using Slow-motion Benchmarking[J]. ACM Transactions on Computer Systems (TOCS), 2003, 21(1): 87-115. |
| [6] | 武越,刘向东. 涉密环境桌面虚拟化多级安全系统设计与实现[J]. 信息网络安全,2014(9):101-104. |
| [7] | BARATTO R A, KIM L N, NIEH J.THINC: A Virtual Display Architecture for Thin-client Computing[J]. ACM SIGOPS Operating Systems Review, 2005, 39(5): 277-290. |
| [8] | TAN K J, GONG J W, WU B T, et al.A Remote Thin Client System for Real Time Multimedia Streaming over VNC[C]//IEEE. 2010 IEEE International Conference on Multimedia and Expo (ICME), July 19-23, 2010, Suntec City, Singapore. New Jersey: IEEE, 2010: 992-997. |
| [9] | SIMOENS P, PRAET P, VANKEIRSBILCK B, et al.Design and Implementation of A Hybrid Remote Display Protocol to Optimize Multimedia Experience on Thin Client Devices[C]//IEEE. Telecommunication Networks and Applications Conference, 2008, December 7-10, 2008, Adelaide, Australia. New Jersey: IEEE, 2008: 391-396. |
| [10] | 郑志蓉,刘毅. 虚拟计算平台远程可信认证技术研究[J]. 信息网络安全,2014(10):77-80. |
| [11] | TALWAR V, NAHRSTEDT K, MILOJICIC D.Modeling Remote Desktop Systems in Utility Environment with Application to QoS Management[C]//IEEE. IEEE International Symposium on Integrated Network Management, June 1-5, 2009, Long Island, NY, USA. New Jersey: IEEE, 2009: 746-760. |
| [12] | LAI A M, NIEH J.On the Performance of Wide-area Thin-client Computing[J]. ACM Transactions on Computer Systems (TOCS), 2006, 24(2): 175-209. |
| [13] | 黄儒,罗守山,李忠献. 面向云桌面平台的攻防反馈防御图研究设计[J]. 信息网络安全,2014(11):1-7. |
| [14] | BARATTO R A, POTTER S, SU G, et al.Mobidesk: Mobile Virtual Desktop Computing[C]//ACM. 10th Annual International Conference on Mobile Computing and Networking, September 26-October 1, 2004, Philadelphia, PA, USA. New York: ACM, 2004: 1-15. |
| [15] | LUBONSKI M, GAY V, SIMMONDS A.A Conceptual Architecture for Adaptation in Remote Desktop Systems Driven by the User Perception of Multimedia[C]//IEEE. 2005 Asia-Pacific Conference on Communications, October 5, 2005, Perth, WA, Australia. New Jersey: IEEE, 2005: 891-895. |
| [16] | 杨永娇,严飞,于钊,等.一种基于VT-d技术的虚拟机安全隔离框架研究[J]. 信息网络安全,2015(11):7-14. |
| [17] | ZHOU Min, SMITH A J.Analysis of Personal Computer Workloads[C]//IEEE. 7th International Symposium on Modeling, Analysis and Simulation of Computer and Telecommunication Systems, October 24-28, 1999, College Park, MD, USA. New Jersey: IEEE, 1999: 208-217. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||