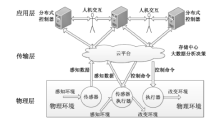
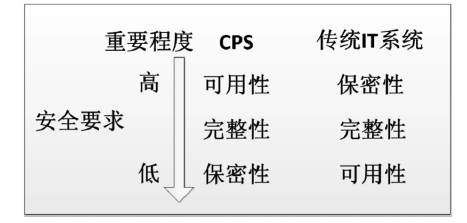
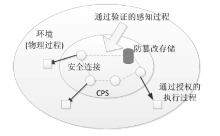
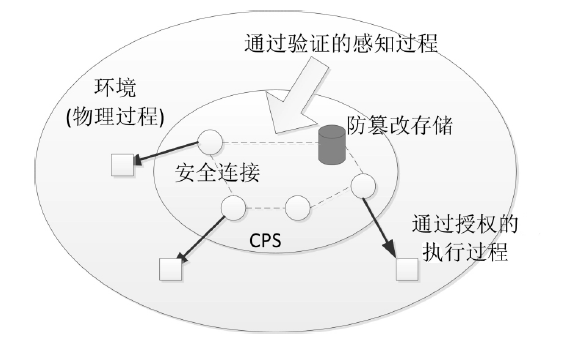
Netinfo Security ›› 2016, Vol. 16 ›› Issue (7): 20-28.doi: 10.3969/j.issn.1671-1122.2016.07.004
• Orginal Article • Previous Articles Next Articles
Research Survey on Security Issues in Cyber-Physical Systems
Kunlun PENG1, Wei PENG1, Dongxia WANG2, Qianqian XING1
- 1.School of Computer, National University of Defense and Technology, Changsha Hunan 410073, China
2.Beijing Institute of System Engineering, Beijing 100101,China
-
Received:2016-05-05Online:2016-07-20Published:2020-05-13
CLC Number:
Cite this article
Kunlun PENG, Wei PENG, Dongxia WANG, Qianqian XING. Research Survey on Security Issues in Cyber-Physical Systems[J]. Netinfo Security, 2016, 16(7): 20-28.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2016.07.004
| [1] | RAJKUMAR R, LEE I, SHA L, et al.Cyber-Physical Systems:The Next Computing Revolution[C]//IEEE. The Design Automation Conference,June 13-18,2010. Anaheim, CA,USA.NJ:IEEE,2010:731-736. |
| [2] | 黎作鹏,张天驰,张菁.信息物理融合系统(CPS)研究综述[J].计算机科学,2011,38(9):25-29. |
| [3] | QAISAR S.Cyber-Physical Systems Security: A Brief Survey[C]//IEEE.12th International Conference on Computational Science and Its Applications, June 18-21, 2012. Salvador, Brazil.NJ:IEEE, 2012 : 146-149. |
| [4] | 彭勇,江常青,谢丰,等.工业控制系统信息安全研究进展[J].清华大学学报(自然科学版),2012,52(10):1396-1408. |
| [5] | AYAN B, TRIDIB M. EnsuringSafety,Security and Sustainability of Mission-Critical Cyber-Physical Systems[J]. Proceedings of the IEEE, 2012, 100(1) : 283-299. |
| [6] | NIST SP800-82.Guide to Industrial Control System(ICS) Security[S].Gaithersburg,USA:National Institute of Standard and Technology (NIST), 2011. |
| [7] | DAVID A.Multiple Efforts to Secure Control Systems Are Under Way,but Challenges Remain,GAO-07-1036[R].Washington DC,USA:US Government Accountability Office(US GAO),2007. |
| [8] | AMEYV M.Security for Cyber-Physical Systems[J].International Journal of Computing and Technology, 2014,1(6):257-261. |
| [9] | 刘景力. 信息物理系统风险评估分析与设计[D].北京:北京邮电大学,2013. |
| [10] | 丁超,杨立君,吴蒙. IoT/CPS 的安全体系结构及关键技术[J].中兴通讯技术,2011,17(1):11-16. |
| [11] | 李钊,彭勇,谢丰,等.信息物理系统安全威胁与措施[J].清华大学学报(自然科学版),2012,52(10):1482-1487. |
| [12] | KONSTANTINOU C, MANIATAKOS M, SAQIB F,et al.Cyber-Physical Systems: A Security Perspective[C]//IEEE.20th IEEE European Test Symposium (ETS) ,May 25-29,2015. Cluj-Napoca, Romania.NJ:IEEE,2015:1-8. |
| [13] | CHAN Haowen, GLIGOR V D, PERRIG A, et al.On the Distribution and Revocation of Cryptographic Keys in Sensor Networks[J]. IEEE Transactions on Dependable and Secure Computing, 2005, 2(3): 233-247. |
| [14] | ALVARO A C, SAURABH A, SHANKAR S.Secure Control: Towards Survivable Cyber-Physical Systems[J]. International Conference on Distributed Computing Systems Workshops, 2008, 6(13) : 495-500. |
| [15] | OLESHCHUK V.Internet of Things and Privacy Preserving Technologies[C]//IEEE.1st International Conference on Wireless Communication, Vehicular Technology,Information Theory and Aerospace & Electronic Systems Technology,May 17-20, 2009. Aalborg, Denmark.NJ:IEEE,2009:336-340. |
| [16] | PARNO B, LUK M, GAUSTAD E, et al. Secure Sensor Network Routing: A Clean-Slate Approach[EB/OL].. |
| [17] | BYRES E,CHAUVIN B,KARSCH J,et al.The Special Needs of SCADA/PCN Firewalls:Architectures and Test Results[C]//IEEE. 10th IEEE Conference on Emerging Technologies and Factory Automations, September 19-22,2005. Catania, Italia.NJ:IEEE,2005:876-884. |
| [18] | JAY B,JAMES C F,JEFFREY P,et al.Snort 2.0 Intrusion Detection Syngress,Feb 2003[EB/OL].. |
| [19] | ROOSTA T,NILSSON D K,LINDQVIST U,et al.An Intrusion Detection System for Wireless Process Control Systems[C]//IEEE. 5th IEEE International Conference on Mobile Ad Hoc and Sensor Systems, September 29-October 2,2008. Atlanta, GA ,USA.NJ:IEEE,2008:866-872. |
| [20] | VALDES A, CHEUNG S.Communication Pattern Ano-Maly Detection in Progess Control Systems[C]//IEEE. International Conference on Technologies for Homeland Security, May 11-12,2009. Boston, MA,USA.NJ:IEEE,2009:1-8. |
| [21] | GAO Wei, MORRIS T,REAVES B,et al.On SCADA Control System Command and Response In-jection and Intrusion Detection[C]//IEEE. 2010 IEEE eCrime Researches Summit,October 18-20,2010. Dallas, TX ,USA.NJ:IEEE,2010:1-9. |
| [22] | ZHU B,JOSEPH A,SASTRY S.A Taxonomy of Cyber Attacks on SCADA Systems[C]//IEEE. 2011 International Conference on Internet of Things and the 4th International Conference on Cyber, Physical and Social Computing (ITHINGSCPSCOM’11),October 19-22,2011. Dalian,China.NJ:IEEE,2011:380-388. |
| [23] | SU Chuanjun, WU Chiaying.JADE Implemented Mobile Multi-Agent Based, Distributed Information Platform for Pervasive Health Care Monitoring[J]. Applied Soft Computing, 2011, 11(1): 315-325. |
| [24] | LUO Qi.Advancing Knowledge Discovery and Data Mining[C]//IEEE.Knowledge Discovery and Data Mining, 2008. WKDD 2008. First International Workshop on, January 23-24,2008. Adelaide, SA,Australia.NJ:IEEE, 2008: 3-5. |
| [25] | KRISHNA K V.Security Solutions for Cyber-physical Systems[D].ARIZONA:ARIZONA STATE UNIVERSITY,2009. |
| [26] | VENKATASUBRAMANIAN K K, NABAR S, GUPTA S K S, et al. Cyber Physical Security Solutions for Pervasive Health Monitoring Systems[J]. User-Driven Healthcare: Concepts, Methodologies, Tools, and Applications, 2013,5(7):276-285. |
| [27] | ROSTAMI M, JUELS A, KOUSHANFAR F, et al. Heart-to-heart (H2H): Authentication for Implanted Medical Devices[EB/OL].. |
| [28] | CHUANG Weihong, GARG R, WU Min. How Secure are Power Network Signature Based Time Stamps?[EB/OL].. |
| [29] | POH M Z, MCDUFF D J, PICARD R W.Non-contact, Automated Cardiac Pulse Measurements Using Video Imaging and Blind Source Separation[J].Optics Express ,2010,18(10):10762-10774. |
| [30] | SAILER R, JAEGER T, ZHANG Xiaolan, et al. Attestation-based Policy Enforcement for Remote Access[EB/OL].. |
| [31] | SCHELLEKENS D, WYSEUR B, PRENEEL B.Remote Attestation on Legacy Operating Systems with Trusted Platform Modules[J]. Science of Computer Programming, 2008, 74(1): 13-22. |
| [32] | SHEN Zhidong, LI Li, YAN Fei, et al.Cloud Computing System Based on Trusted Computing Platform[C]//IEEE.Intelligent Computation Technology and Automation (ICICTA), 2010 International Conference on, May 11-12,2010. Changsha,China.NJ:IEEE, 2010: 942-945. |
| [33] | MICHAEL K, ELISA B.Physically Restricted Authentication and Encryption for Cyber-Physical Systems[J]. STC’09 Proceedings of the 2009 ACM Workshop on Scalable Trusted Computing,2009, 8(12) : 55-60. |
| [34] | ATALLAH M J, BRYANT E D, KORB J T, et al.Binding Software to Specific Native Hardware in a VM Environment: The Puf Challenge and Opportunity[EB/OL]. . |
| [35] | GASSEND B, CLARKE D, DIJK M V,et al. Controlled Physical Random Functions[EB/OL].. |
| [36] | GUAJARDO J, KUMAR S S, SCHRIJEN G J, et al. FPGA intrinsic PUFs and Their Use for IP Protection[EB/OL].. |
| [37] | SUH G E, DEVADAS S.Physcal Unclonable Functions for Device Authentication and Secret Key Generation[C]//IEEE. 44th IEEE Design Automation Conference (DAC), June 4-8,2007. San Diego, CA ,USA.NJ:IEEE,2007:9-14. |
| [38] | CHAN A C F. ZHOU Jianying.Cyber-Physical Device Authentication for Smart Grid Electric Vehicle Ecosystem[J].IEEE Journal on Selected Areas in Communications,2014,32(7):1509-1517. |
| [39] | OLESHCHUK V.Internet of Things and Privacy Preserving Technologies[C]//IEEE.1st International Conference on Wireless Communication, Vehicular Technology, Information Theory and Aerospace&Electronic Systems Technology, 2009,May 17-20,2009. Aalborg, Denmark.NJ:IEEE,2009:336-340. |
| [40] | LUK M, MEZZOUR G, PERRIG A, et al.Minisec: A Secure Sensor Network Communication Architecture[C]//IEEE. 6th International Conference on Information Processing in Sensor Networks (IPSN 2007), April 25-27,2007. Cambridge, MA,USA.NJ:IEEE, 2007 : 479-488. |
| [41] | LI Hong, SUN Limin,ZHU Haojin, et al.Achieving Privacy Preservation in WiFi Fingerprint-based Localization[C]//IEEE. INFOCOM 2014, April 27-May 2,2014. Toronto, ON, Canada.NJ:IEEE,2014:2337-2345. |
| [42] | YANG Dejun, FANG Xi, XUE Guoliang.Truthful Incentive Mechanisms for k-anonymity Location Privacy[C]// IEEE. INFOCOM 2013, April 14-19, 2013. Turin, Italia.NJ:IEEE, 2013: 2994-3002. |
| [43] | GENTRY C. Fully Homomorphic Encryption Using Ideal Lattices[EB/OL].. |
| [44] | ATALLAH M J, LI J.Secure Outsourcing of Sequence Vomparisons[J].Int. J. Inf. Secur., 2005(4) :277-287. |
| [45] | YANG Weining,LI Ninghui,QI Yuan,et al.Minimizing Private Data Disclosures in the Smart grid[EB/OL].. |
| [46] | FAN Zhong, KALOGRIDIS G, EFTHYMIOU C,et al. The New Frontier of Communications Research: Smart Grid and Smart Metering[EB/OL].. |
| [47] | U.S. NIST.Guidelines for Smart Grid Cyber Security[R].U.S: NIST, 2010. |
| [48] | CAVOUKIAN A, POLONETSKY J, WOLF C. Smart Privacy for the Smart Grid: Embedding Privacy into the Design of Electricity Conservation[EB/OL].. |
| [49] | ATALLAH M J, DU Wenliang. Secure Multi-Party Computational Geometry[EB/OL].. |
| [50] | KØIEN G M, OLESHCHUK V A. Location Privacy for Cellular Systems:Analysis and Solution[EB/OL].. |
| [51] | 熊琦,彭勇,戴忠华.工控系统信息安全风险评估初探[J].中国信息安全,2012,27(3):57-59. |
| [52] | HAIMES Y Y,CHITTESTER C G.A Roadmap for Quantifying the Efficacy of Risk Management of Information Security and Interdependent SCADA Systems[J]. Journal of Homeland Security and Emergency Management, 2005, 2(2) : 1-21. |
| [53] | BRIAN K.Cyber Incident Blamed for Nuclear Power Plant Shutdown[EB/OL].. |
| [54] | TEN C W, LIU Chenching, GOVINDARASU M.Vulnerability Assessment of Cybersecurity for SCADA Systems Using Attack Trees[C]//IEEE. 2007 IEEE Conference on Power Engineering Sociery General Meeting,June 24-28, 2007. Tampa, FL, USA. NJ : IEEE , 2007: 1-8. |
| [55] | HIGUERO M V, UNZILLA J J, JACOB E, et al. Application of ‘Attack Trees’ Technique to Copyright Protection Protocols Using Watermarking and Definition of a New Transactions Protocol SecDP (Secure Distribution Protocol)[EB/OL].. |
| [56] | PATEL S C, GRAHAM J H,RALSTON P A S.Quantitatively Assessing the Vulnerability of Critical Information Systems:A New Method for Evaluating Security Enhancements[J].International Journal of Information Management, 2008, 28(6) : 483-491. |
| [57] | ZONOUS S A, KHURANA H, SANDERS W H, et al.RRE:A Game-Theoretic Intrusion Response and Recovery Engine[J]. IEEE Transactions on Parallel and Distributed Systems, 2009, 25(2) : 395-406. |
| [58] | WEI Mingkui, WANG Wenye.Greenbench: a Benchmark for Observing Power Grid Vulnerability under Data-Centric Threats[C]//IEEE. INFOCOM 2014, April 27-May 2,2014.Toronto, ON ,Canada.NJ:IEEE,2014:2625-2633. |
| [59] | TAN Rui, KRISHNA V B, YAU D K Y,et al.Impact of Integrity Attacks on Real-time Pricing in Smart Grids[EB/OL].. |
| [60] | CARDENAS A.A, AMIN S, LIN Z S, et al.Attacks against Process Control Systems:Risk Assessment, Detection, and Response[EB/OL].. |
| [61] | AMIN S, SCHWARTZ G A, HUSSAIN A.In Quest of Benchmarking Security Risks to Cyber-Physical Systems[J]. IEEE Netw. 2013,27(1):19-24. |
| [62] | ZHENG Yaowen, HONG Li, SHI Zhiqiang, et al. Security of Cyber Physical System[EB/OL].. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||