Netinfo Security ›› 2016, Vol. 16 ›› Issue (6): 15-21.doi: 10.3969/j.issn.1671-1122.2016.06.003
• Orginal Article • Previous Articles Next Articles
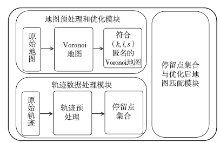
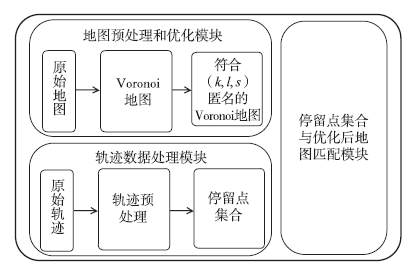
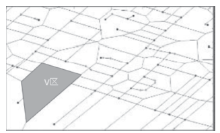
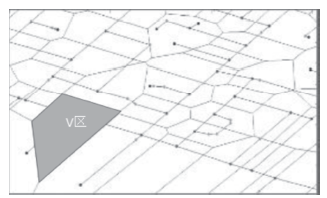
Research on Trajectory Privacy Preserving over Road Network Based on Voronoi Diagram
Jianchuan XIAO1,2, Li XU1,2( ), A-yong YE1,2, Limei LIN1,2
), A-yong YE1,2, Limei LIN1,2
- 1. School of Mathematics and Computer Science, Fujian Normal University, Fuzhou Fujian 350007, China
2.Fujian Provincial Key Laboratory of Network Security and Cryptology, Fuzhou Fujian 350007, China
-
Received:2016-05-04Online:2016-06-20Published:2020-05-13
CLC Number:
Cite this article
Jianchuan XIAO, Li XU, A-yong YE, Limei LIN. Research on Trajectory Privacy Preserving over Road Network Based on Voronoi Diagram[J]. Netinfo Security, 2016, 16(6): 15-21.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2016.06.003
| [1] | SWEENEY L.k-anonymity:A Model for Protecting Privacy[J].International Journal on Uncertainty,Fuzziness and Knowledge-based Systems,2002,10(5):557-570 |
| [2] | GRUTESER M, GRUNWALD D.Anonymous Usage of Location-based Services through Spatial and Temporal Cloaking[C]//ACM. International Conference on Mobile Systems, Applications, and Services, May 5-8, 2003.San Francisco, CA, USA. N Y: ACM,2003:31-42. |
| [3] | ABUL O, BONCHI F, NANNI M .Never Walk Alone: Uncertainty for Anonymity in Moving Objects Databases[C]//IEEE.Proceedings of the 24th IEEE International Conference on Data Engineering,April 7-12 ,2008.Cancun,Mexico.NJ:IEEE,2008:376-385. |
| [4] | MACHANAVAJJHALA A, GEHRKE J, KIFER D, et al.L-diversity: Privacy beyond k-anonymity[C]// IEEE.International Conference on Data Engineering, April 3-7,2006.Atlanta, GA, USA.NJ:IEEE, 2006:24. |
| [5] | HUO Zheng, MENG Xiaofeng, HU Haibo, et al. You Can Walk Alone: Trajectory Privacy-preserving through Significant Stays Protection[J]. Lecture Notes in Computer Science, 2012(7238):351-366. |
| [6] | SUI Peipei, WO Tianyu, WEN Zhangle, et al.Privacy-Preserving Trajectory Publication against Parking Point Attacks[C]//IEEE Computer Society.2013 IEEE 10th International Conference on Ubiquitous Intelligence & Computing and 2013 IEEE 10th International Conference on Autonomic & Trusted Computing(UIC/ATC),December 18-21,2013.Vietri sul Mere,SA, Italia.NJ:IEEE,2013:569-574. |
| [7] | 齐凌艳, 陈荣国, 温馨. 基于语义轨迹停留点的位置服务匹配与应用研究[J]. 地球信息科学学报, 2014(5):720-726. |
| [8] | 赵平, 马春光, 高训兵,等. 路网环境下基于Voronoi图的位置隐私保护方法[J]. 计算机科学, 2013(7):116-120. |
| [9] | 马春光, 周长利, 杨松涛,等. 基于Voronoi图预划分的LBS位置隐私保护方法[J]. 通信学报, 2015, 36(5):1-12. |
| [10] | BRINKHOFF T.Generating Traffic Data[J]. Bulletin of the Technical Committee on Data Engineering IEEE Computer Society, 2003(26):2003. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||