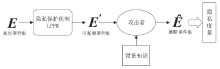
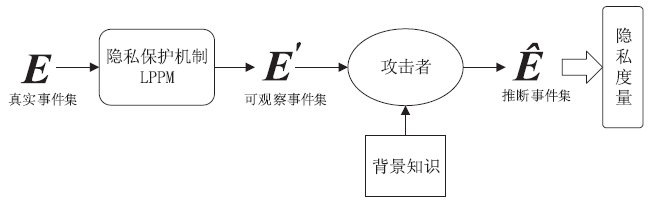
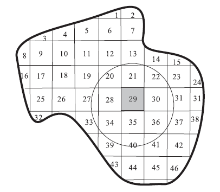
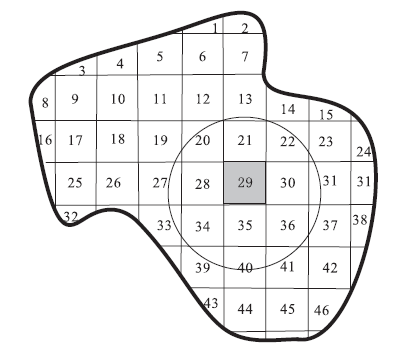
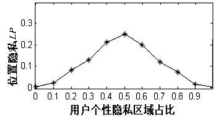
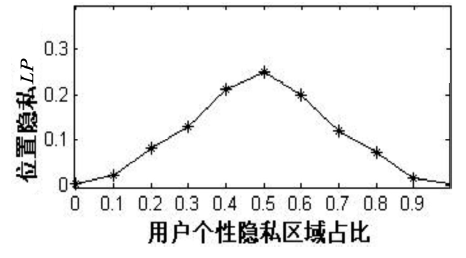
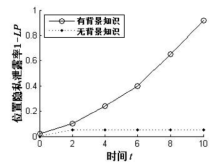
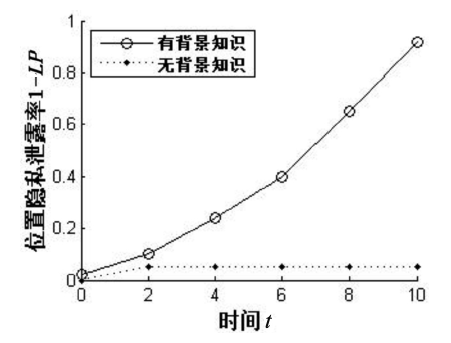
| [1] |
张学军, 桂小林, 伍忠东. 位置服务隐私保护研究综述[J]. 软件学报, 2015(9):2373-2395.
|
| [2] |
孟小峰, 潘晓. 基于位置服务的隐私保护[J]. 中国计算机学会通讯, 2010, 6(6): 16-23.
|
| [3] |
DÍAZ C, SEYS S, CLAESSENS J, et al. Towards Measuring Anonymity[C]//Springer. 2nd International Conference on Privacy Enhancing Technologies (PET2002), April 14-15, 2002,San Francisco, CA, USA. Berlin Heidelberg: Springer-Verlag, 2003:54-68.
|
| [4] |
SHOKRI R, FREUDIGER J, JADLIWALA M, et al.A Distortion-Based Metric for Location Privacy[C]//ACM. 8th ACM workshop on Privacy in the electronic society, November 9, 2009, Chicago, IL, USA. New York, USA: ACM ,2009: 21-30.
|
| [5] |
SHOKRI R, TRONCOSO C, DIAZ C, et al.Unraveling an Old Cloak: k-anonymity for Location Privacy[C]// ACM. 9th ACM workshop on Privacy in the Electronic Society, October 04-08, 2010, Chicago, IL, USA. New York, USA: ACM, 2010:115-118.
|
| [6] |
林欣,李善平,杨朝晖. LBS 中连续查询攻击算法及匿名性度量[J]. 软件学报,2009,20(4): 1058-1068.
|
| [7] |
CHEN X, PANG J.Measuring Query Privacy in Location-based Services[C]//ACM.2nd ACM Conference on Data and Application Security and Privacy, February 07-09, 2012, San Antonio, TX, USA. New York, USA: ACM, 2012: 49-60.
|
| [8] |
SERJANTOV A, DANEZIS G.Towards an Information Theoretic Metric for Anonymity[C]//Springer. 2nd International Conference on Privacy Enhancing Technologies (PET2002), April 14-15, 2002,San Francisco, CA, USA. Berlin Heidelberg: Springer-Verlag, 2003: 41-53.
|
| [9] |
MA Z, KAROL F, WEBER M.Measuring Location Privacy in V2X Communication Systems with Accumulated Information[C]// IEEE. 6th International Conference on Mobile Adhoc and Sensor Systems (MASS’09), October 12-15 2009, Macau, China. Piscataway, NJ, USA: IEEE, 2009: 322-331.
|
| [10] |
BOUALOUACHE A, MOUSSAOUI S.S2SI: A Practical Pseudonym Changing Strategy for Location Privacy in VANETs[C]// IEEE. 2014 International Conference on Advanced Networking Distributed Systems and Applications (INDS2014), June 17-19, 2014, Bejaia, Algeria. Piscataway, NJ, USA: IEEE, 2014: 70-75.
|
| [11] |
SHOKRI R, THEODORAKOPOULOS G, PAPADIMITRATOS P, et al.Hiding in the Mobile Crowd: Location Privacy through Collaboration[J]. IEEE Transactions on Dependable & Secure Computing Special Issue on “Security & Privacy in Mobile Platforms”, 2014, 11(3):266-279.
|
| [12] |
HOH B, GRUTESER M.Protecting Location Privacy through Path Confusion[C]// IEEE. 1st International Conference on Security and Privacy for Emerging Areas in Communications Networks(SecureComm2005), September 5-9, 2005, Athens, Greece. Piscataway, NJ, USA: IEEE, 2005: 194-205.
|
| [13] |
FISCHER L, KATZENBEISSER S, ECKERT C.Measuring Unlinkability Revisited[C]// ACM. 7th ACM Workshop on Privacy in the Electronic Society, October 27-31, 2008, Alexandria, VA, USA. New York, USA: ACM, 2008: 105-110.
|
| [14] |
HOH B, GRUTESER M, Herring R, et al.Virtual Trip Lines for Distributed Privacy-preserving Traffic Monitoring[C]//ACM. 6th International Conference on Mobile Systems, Applications, and Services, June 17-20,2008,Breckenridge,Colorado,USA. New York, USA: ACM, 2008: 15-28.
|
| [15] |
SHOKRI R, THEODORAKOPOULOS G, BOUDEC J Y L, et al. Quantifying Location Privacy[J]. IEEE Symposium on Security & Privacy, 2011, 42(12):247-262.
|
| [16] |
张学军,桂小林,冯志超,等. 位置服务中的查询隐私度量框架研究[J]. 西安交通大学学报,2014,48(2): 8-13.
|
| [17] |
BRINKHOFF T.A Framework for Generating Network-based Moving Objects[J]. GeoInformatica, 2002, 6(2): 153-180.
|
 ), Jiashuai LI1,2, Haifeng MA1,2
), Jiashuai LI1,2, Haifeng MA1,2