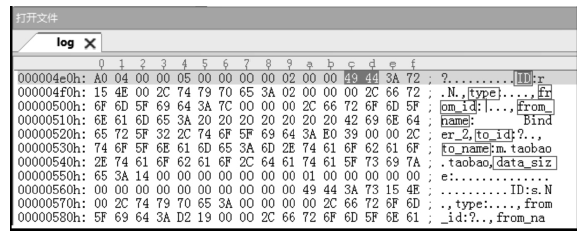
| [1] |
贾同彬,蔡阳,王跃武,等. 一种面向普通用户的Android APP安全性动态分析方法研究[J]. 信息网络安全,2015(9):1-5.
|
| [2] |
杨欢,张玉清,胡予濮,等.基于多类特征的Android应用恶意行为检测系统[J].计算机学报,2014,37(1):1-13.
|
| [3] |
ZHOU Yajin, JIANG Xuxian.Dissecting Android Malware: Characterization and Evolution[C]//IEEE.Proceedings of the 33rd IEEE Symposium on Security and Privacy,May 20-23,2012, Oakland,USA.Piscataway, NJ, USA: IEEE,2012:221-239.
|
| [4] |
ALAZAB M,MOONSAMY V,BATTEN L, et al.Analysis of Malicious and Benign Android Application[C]// IEEE.Proceedings of the 32nd International Conference on Distributed Computing Systems Workshops, June 18-21,2012,Macau,China. Piscataway, NJ, USA: IEEE, 2012:608-616.
|
| [5] |
MOONSAMY V,ALAZAB M,BATTEN L.Towards an Understanding of the Impact of Advertising on Data Leaks[J]. International Journal of Security and Networks, 2012, 7(3):181-193.
|
| [6] |
吴剑华,莫兰芳,李湘.Android用户隐私保护系统[J].信息网络安全,2012 (9):50-53.
|
| [7] |
李子锋,程绍银,蒋凡.一种Android应用程序恶意行为的静态检测方法[J].计算机系统应用,2013,22(7):148-151.
|
| [8] |
BERESFORD A R, RICE A, SKEHIN N, et al.MockDroid: Trading Privacy for Application Functionality on Smartphones[C]//ACM.Proceedings of the 12th Workshop on Mobile Computing Systems and Applications. March 1-2, 2011,Phoenix,USA. New York, USA: ACM , 2011:49-54.
|
| [9] |
出众网络.安卓软件应用安全漏洞挖掘国内外研究现状[EB/OL].,2014-08-28.
|
| [10] |
ENCK W, GILBERT P, CHUM B, et al.TaintDroid: An Information-flow Tracking System for Realtime Privacy Monitoring on Smartphones[J].Acm Transactions on Computer Systems, 2010, 57(3):393-407.
|
| [11] |
GILBERT P, CHUN B G, COX L P, et al.Vision: Automated Security Validation of Mobile Apps at App Markets[C]// ACM . MCS '11 Proceedings of theSecond international Workshop on Mobile Cloud Computing and Services, June 28 - July 1,2011,Bethesda, MD, USA. New York:ACM,2011:21-26.
|
| [12] |
邓平凡. 深入理解Android[M].北京:机械工业出版社,2011.
|
| [13] |
YANG Zhemin, YANG Min, ZHANG Yuan .et al.AppIntent: Analyzing Sensitive Data Transmission in Android for Privacy Leakage Detection[C]// ACM .Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, November 4-8, 2013, Germany. New York:ACM,2013: 1043-1054.
|
| [14] |
王汝言,蒋子泉,刘乔寿,等.Android下Binder进程间通信机制的分析与研究[J].计算机技术与发展,2012,22(9):107-110.
|
| [15] |
DAVI L, DMITRIENKO A, SADEGHI A R, et al.Privilege Escalation Attacks on Android[C]// ISC.Proceedings of the 13th Information Security Conference, November 13-15, 2010,Florida,USA. Heidelberg Berlin:Springer, 2010: 346-360.
|
| [16] |
FELT A P, WANG H J, MOSHCHUK A, et al.Permission Re-Delegation: Attacks and Defenses[C]// USENIX.Proceedings of the 20th USENIX Security Symposium, August 8-12, 2011,San Francisco,USA. Berkeley,USA :USENIX,2011: 22.
|
| [17] |
张耀民. SSH 框架在Web 项目开发中的构建和应用实践[J].微型机与应用,2013,32(15):1-4.
|
| [18] |
蒋卫祥,陈荣保.基于SSH框架的构件组装技术研究与应用[J].常州信息职业技术学院学报,2013,12(4):1-4.
|
 ), Zhen HAN1, Qihui ZHOU2, Yazhe WANG2
), Zhen HAN1, Qihui ZHOU2, Yazhe WANG2