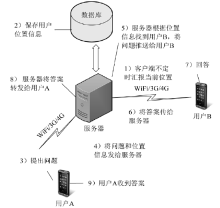
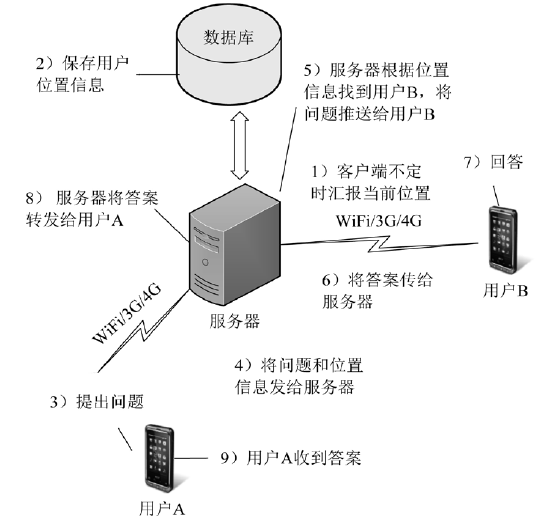
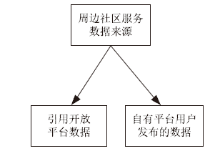
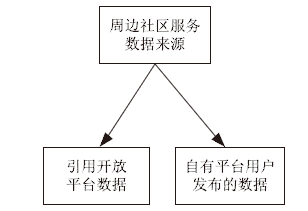
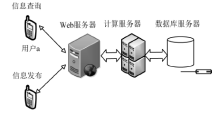
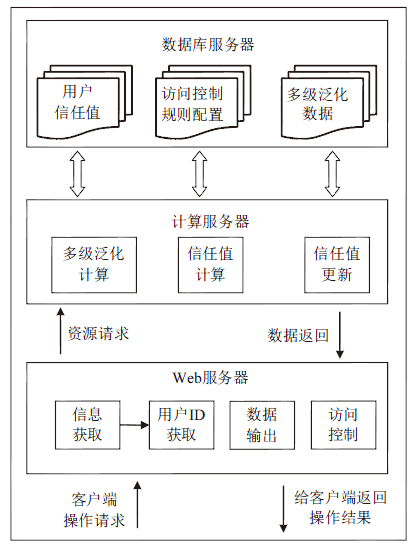
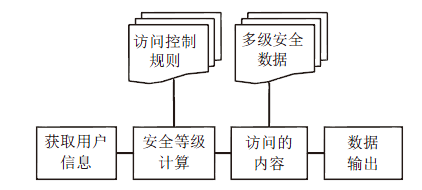
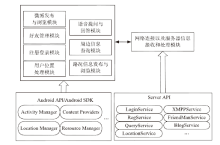
| [1] |
王沂,韩广国,李慧智.无线网络中可证安全的移动用户密钥交换协议[J]. 信息网络安全,2015(3):54-58.
|
| [2] |
李凤华,王巍,马建峰,等. 基于行为的访问控制模型及其行为管理[J]. 电子学报,2008,36(10):1881-1890.
|
| [3] |
王黎璐,王鸿宇.移动互联网安全分析[J]. 信息网络安全,2013(10):91-94.
|
| [4] |
凡菊,姜元春,张结魁. 网络隐私问题研究综述[J]. 情报理论与实践,2008,31(1):153-157.
|
| [5] |
GRAWAL R, SRIKANT R.Privacy-preserving Data Mining[J]. ACM Sigmod Record, 2000, 29(2): 439-450.
|
| [6] |
WARNER S L.Randomized Response: A Survey Technique for Eliminating Evasive Answer Bias[J]. Journal of the American Statistical Association, 1965, 60(309): 63-69.
|
| [7] |
YU Yu, LEIWO J, PREMKUMAR B.A Study on the Security of Privacy Homomorphism[C]//IEEE. Third International Conference on Information Technology: New Generations (ITNG'06), April 10-12, 2006, Las Vegas, Nevada, USA. New Jersey: IEEE, 2006: 470-475.
|
| [8] |
YANG Xiaochun, LIU Xiangyu, WANG Bin, et al.K-anonymization Approaches for Supporting Multiple Constraints[J]. Journal of Software, 2006, 17(5): 1222-1231.
|
| [9] |
FAN S, TRUONG S. Access Control for Networks: US, Patent 6,219,06[P].2001-4-17.
|
| [10] |
SANDHU R S, SAMARATI P.Access Control: Principle and Practice[J]. IEEE Communications Magazine, 1994, 32(9): 40-48.
|
| [11] |
SANDHU R S, COYNE E J, FEINSTEIN H L, et al.Role-based Access Control Models[J]. Computer, 1996, 29(2): 38-47.
|
| [12] |
Yang Y, Ding R, Min Y.Object-based Access Control Model[J]. Automation of Electric Power Systems, 2003, 27(7): 36-40.
|
| [13] |
郑周,张大军,李运发. 云计算中面向数据存储的安全访问控制机制[J]. 信息网络安全,2015(9):221-226.
|
| [14] |
任向民. 基于K-匿名的隐私保护方法研究[D]. 哈尔滨:哈尔滨工程大学,2012.
|
| [15] |
SWEENEY L. k-anonymity: A Model for Protecting Privacy[J]. IEEE Security and Privacy Magazine, 2002, 10(5): 1-14.
|
| [16] |
MACHANAVAJJHALA A, KIFER D, GEHRKE J, et al.l-diversity: Privacy beyond k-anonymity[J]. ACM Transactions on Knowledge Discovery from Data (TKDD), 2007, 1(1): 3.
|
| [17] |
唐春明,郑晓龙.云计算中一种对大群组用户的隐私保护公共审计方案[J]. 信息网络安全,2015(2):19-25.
|
 ), Fuzhen CHEN1,2, Jiujun CHENG1,2, Xiangrong CHEN1,2
), Fuzhen CHEN1,2, Jiujun CHENG1,2, Xiangrong CHEN1,2