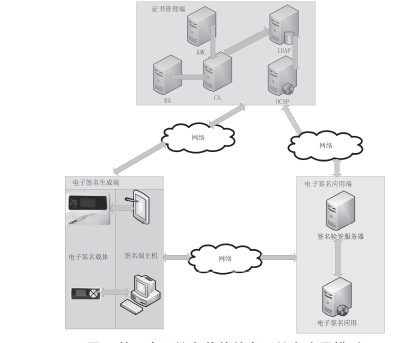
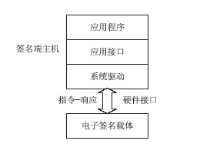
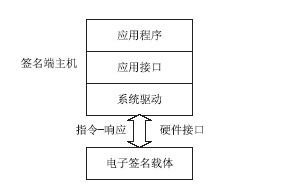
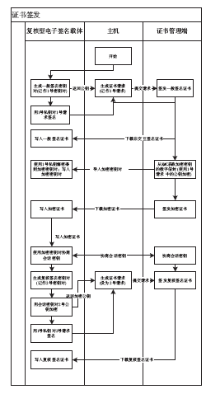
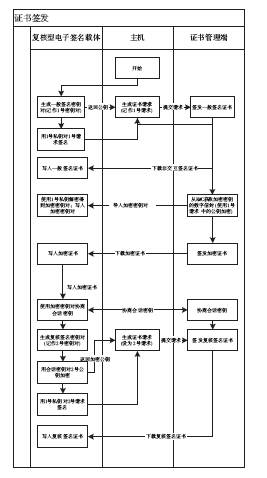
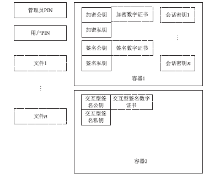
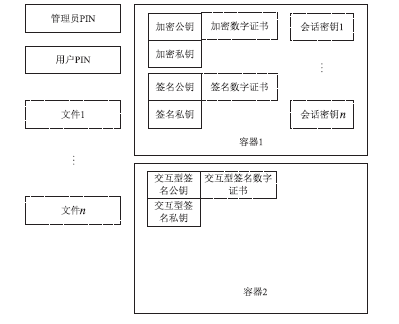
Netinfo Security ›› 2015, Vol. 15 ›› Issue (9): 93-96.doi: 10.3969/j.issn.1671-1122.2015.09.022
• Orginal Article • Previous Articles Next Articles
Review-attached Electronic Signing Scheme Following Autonomous Cryptographic Standards
Peng-fei ZHU1,2( ), Wei LI2, Li-qin ZHANG2, Hai-yan LIU3
), Wei LI2, Li-qin ZHANG2, Hai-yan LIU3
- 1. Beijing Engineering Laboratory of Smart Network Authentication, Beijing 100085, China
2. Feitian Technologies Co., Ltd., Beijing 100085, China
3. BaoTou Railway Vocational & Technical College, Baotou Neimenggu 014060, China
-
Received:2015-07-15Online:2015-09-01Published:2015-11-13
CLC Number:
Cite this article
Peng-fei ZHU, Wei LI, Li-qin ZHANG, Hai-yan LIU. Review-attached Electronic Signing Scheme Following Autonomous Cryptographic Standards[J]. Netinfo Security, 2015, 15(9): 93-96.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2015.09.022
| [1] | JR/T 0068-2012.网上银行系统信息安全通用规范R/T 0068-2012.网上银行系统信息安全通用规范[S],2012. |
| [2] | 李伟,于华章,朱鹏飞.一种交互型USB Key方案[C]//第18届全国信息安全保密学术会议论文集,2008:378-383 |
| [3] | 飞天诚信科技有限公司. 复核型USB Key与普通USB Key的混合应用探讨[J]. 保密科学技术,2011,(3):13-15 |
| [4] | 张云峰,王璐,方先锋,等.基于国密算法的安全金融ATM系统实现及产业化[J].信息系统工程,2014,(7):66-69. |
| [5] | GM/T 0034-2014.基于SM2密码算法的证书认证系统密码及其相关安全技术规范M/T 0034-2014.基于SM2密码算法的证书认证系统密码及其相关安全技术规范[S],2014. |
| [6] | GM/T 0017-2012.智能密码钥匙密码应用接口数据格式规范M/T 0017-2012.智能密码钥匙密码应用接口数据格式规范[S],2012. |
| [7] | 王标,陈持协,孙谋,等. 环Zn上广义圆锥曲线多重数字签名方案的分析与改进[J]. 信息网络安全,2014,(4):60-63. |
| [8] | GM/T 0016-2012.智能密码钥匙密码应用接口规范M/T 0016-2012.智能密码钥匙密码应用接口规范[S],2012. |
| [9] | GM/T 0010-2012.SM2密码算法加密签名消息语法规范M/T 0010-2012.SM2密码算法加密签名消息语法规范[S],2012. |
| [10] | GM/T 0009-2012.SM2密码算法使用规范M/T 0009-2012.SM2密码算法使用规范[S],2012. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||