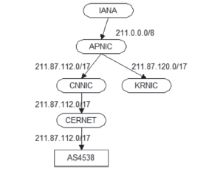
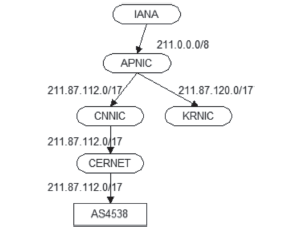
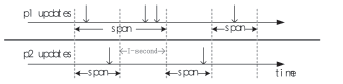
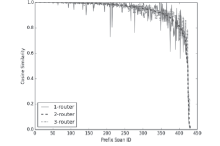
| [1] |
Huston G.Analyzing the Internet BGP routing table[J]. Internet Protocol Journal, 2001,4(1):2-15.
|
| [2] |
Hiran R, Carlsson N, Gill P.Characterizing Large-Scale Routing Anomalies: A Case Study of the China Telecom Incident[J]. Lecture Notes in Computer Science, 2013:229-238.
|
| [3] |
尹宝,姜丽莹,王潮. 量子蚁群算法的大规模无线传感网可信安全路由设计[J]. 信息网络安全,2015,(3):14-18.
|
| [4] |
Khare V, Ju Q, Zhang B.Concurrent Prefix Hijacks: Occurrence and Impacts 65[C]// Proceedings of the 2012 ACM conference on Internet measurement conference. ACM, 2012:29-36.
|
| [5] |
刘东亮,马春光. 基于NS-3的机会网络路由协议仿真[J]. 信息网络安全,2014,(5):52-58.
|
| [6] |
刘志辉,孙斌,谷利泽,等. 一种防范BGP地址前缀劫持的源认证方案[J]. 软件学报,2012,23(7):1908-1923.
|
| [7] |
|
| [8] |
|
| [9] |
赵玉东,徐恪,朱亮. 一种路由设备服务可信属性定义方法与可信路由协议设计[J]. 信息网络安全,2015,(1):24-31.
|
| [10] |
Lad M, Massey D, Pei D, et al.PHAS: A Prefix Hijack Alert System[J]. Security, 2006, 15:108-119.
|
| [11] |
Chi Y J, Oliveira R, Zhang L.Cyclops: the AS-Level connectivity observatory.[J]. Sigcomm Comput.commun.rev, 2009, 38(5):5-16.
|
| [12] |
Yan H, Oliveira R, Burnett K, et al.BGPmon: A Real-Time, Scalable, Extensible Monitoring System[C]//Cybersecurity Applications & Technologies Conference for Homeland Security, 2009:212-223.
|
| [13] |
齐峰,马春光,周永进,等. 一种基于网络编码的机会社会网络路由算法[J]. 信息网络安全,2015,(2):51-56.
|
| [14] |
Cheng P C, Zhang B, Massey D, et al.Identifying BGP routing table transfers[J]. Computer Networks, 2011, 55(3):636-649.
|
| [15] |
Kalogiros C, Bagnulo M, Kostopoulos A.Understanding incentives for prefix aggregation in BGP[J]. ReArch'09, Proceedings of the 2009 workshop on Re-architecting the internet,(49-54), 1 December 2009, Rome, Italy, 2009:49-54.
|
| [16] |
齐峰,马春光,周永进,等. 一种基于网络编码的机会社会网络路由算法[J]. 信息网络安全,2015,(2):51-56.
|
| [17] |
Archipelago (Ark) Measurement Infrastructure Project Homepage[EB/OL]. .
|
 ), Zhen LI, Gang XIONG
), Zhen LI, Gang XIONG