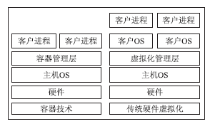
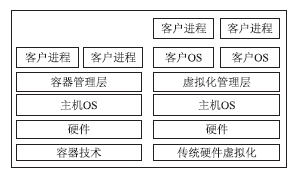
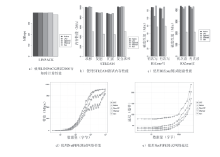
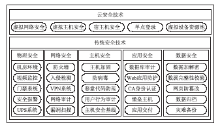
| [1] |
KAMP P H, WATSON R N M. Jails: Confining the omnipotent root[C]//Proceedings of t-he 2nd International SANE Conference, 2000: 116.
|
| [2] |
PRICE D, TUCKER A.Solaris Zones: Operating System Support for Consolidating Commercial Workloads[C]//LISA, 2004: 241-254.
|
| [3] |
SOLTESZ S, PÖTZL H, FIUCZYNSKI M E, et al. Container-based Operating System Virtu-alization: A Scalable, High-performance Alternative to Hypervisors[J]. Proceedings of Eurosys, 2007, 41(3): 275-288.
|
| [4] |
HELSLEY M. LXC: Linux container tools[EB/OL]. .
|
| [5] |
XAVIER M G, NEVES M V, ROSSI F D, et al.Performance Evaluation of Container-Based Virtualization for High Performance Computing Environments[C]//16th Euromicro Conference on Parallel, Distributed and Network-Based Processing (PDP 2008), IEEE, 2013: 233-240.
|
| [6] |
沈长达,尤俊生,钱镜洁. TrueCrypt加密容器快速检测技术[J]. 信息网络安全,2014,(9):220-222.
|
| [7] |
MERKEL D. Docker: lightweight linux containers for consistent development and dep-loyment[EB/OL]. .
|
| [8] |
陈驰,于晶. 云计算安全体系[M]. 北京:科学出版社,2014.
|
| [9] |
秦志光,包文意,赵洋,等. 云存储中一种模糊关键字搜索加密方案[J]. 信息网络安全,2015,(6):7-12.
|
| [10] |
冯登国,张敏,张妍,等. 云计算安全研究[J]. 软件学报,2011,22(1):71-83.
|
| [11] |
张云勇,陈清金,潘松柏,等. 云计算安全关键技术分析[J]. 电信科学,2010,26(9):64-69.
|
| [12] |
周国安,李强,陈新,等. 云环境下海量小文件存储技术研究综述[J]. 信息网络安全,2014,(6):11-17.
|
| [13] |
董宁. 云计算环境下的信息安全防护策略探析[J]. 电子测试,2014,(5):141-142.
|
| [14] |
王静. 基于飞腾平台的容器虚拟化技术研究[D]. 长沙:国防科学技术大学,2013.
|
| [15] |
薄明霞,陈军,王渭清. 云计算安全体系架构研究[J]. 信息网络安全,2011,(8):79-81.
|
| [16] |
Shocker. Docker PoC VMM-container breakout[EB/OL]. .
|
| [17] |
GUMMARAJU J, DESIKAN T, TURNER Y. Over 30% of Official Images in Docker Hub C-ontain High Priority Security Vulnerabilities[EB/OL]. .
|
| [18] |
秦志光,吴世坤,熊虎. 云存储服务中数据完整性审计方案综述[J]. 信息网络安全,2014,(7):1-6.
|
| [19] |
岑义涛. 从Docker容器漏洞谈Docker安全[EB/OL]. .
|