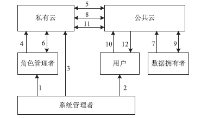
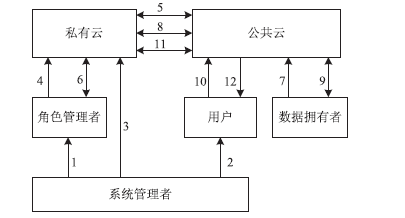
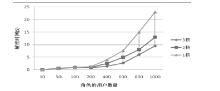
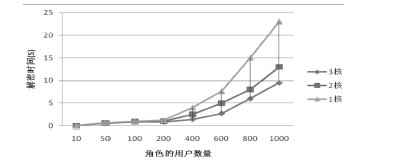
| [1] |
AKL S G, TAYLOR P D.Cryptographic Solution to A Problem of Access Control in A Hierarchy[J]. ACM Transactions on Computer Systems, 1983, 1(3): 239-248.
|
| [2] |
ATALLAH M J, BLANTON M, FAZIO N, et al.Dynamic and Efficient Key Management for Access Hierarchies[J]. ACM Transactions on Information and System Security, 2009, 12(3): 96-139.
|
| [3] |
王淑娥,林柏钢,杨旸,等. 用于PHR云存储的属性密文访问控制方案[J]. 信息网络安全,2014,(5):15-20.
|
| [4] |
VIMERCATI S D C D, FORESTI S, JAJODIA S, et al. Over-encryption: Management of Access Control Evolution on Outsourced Data[C]//Proceedings of the 33rd International Conference on Very Large Data Bases, Vienna. Austria, 2007: 123-134.
|
| [5] |
BLUNDO C, CIMATO S, VIMERCATI S D C D, et al. Efficient Key Management for Enforcing Access Control in Outsourced Scenarios[C]//Proceedings of International Conference on Information Security. New York, USA, 2009: 364-375.
|
| [6] |
张红旗,刘江,代向东,等. 一种多级跨域访问控制管理模型[J]. 信息网络安全,2014,(2):1-6.
|
| [7] |
GENTRY C, SILVERBERG A.Hierarchical ID-based cryptography[C]//Proceedings of the 8th International Conference on the Theory and Application of Cryptology and Information Security. Queenstown, New Zealand: 2002, 548-566.
|
| [8] |
LUO S, CHEN Y, HU J B, et al.New Fully Secure Hierarchical Identity-Based Encryption with Constant Size Ciphertexts[C]//Proceedings of the 7th International Conference on Information Security Practice and Experience. 2011: 55-70.
|
| [9] |
WAN Z G, LIU J, DENG R H.A Hierarchical Attribute-Based Solution for Flexible and Scalable Access Control in Cloud Computing[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(2): 743-754.
|
| [10] |
ALMUTAIRI A, SARFRAZ M, BASALAMAH S, et al.A Distributed Access Control Architecture for Cloud Computing[J]. IEEE Software, 2012, 29(2): 36-44.
|
| [11] |
ZHOU L, VARADHARAJAN V, HITCHENS M.Achieving Secure Role-Based Access Control on Encrypted Data in Cloud Storage[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(12): 1947-1960.
|
| [12] |
YOUNIS A, KASHIF K, MADJID M.An Access Control Model for Cloud Computing[J]. Journal of Information Security and Applications, 2014, 19(1): 45-60.
|
| [13] |
LIU C L.Cloud Service Access Control System based on Ontologies[J]. Advances in Engineering Software, 2014, 69: 26-36.
|
| [14] |
LIN G Y, WANG D R, BIE Y Y, et al.MTBAC: A Mutual Trust based Access Control Model in Cloud Computing[J]. China Communications, 2014, 11(4): 154-162.
|
| [15] |
YANG K, JIA X H, REN K, et al.DAC-MACS: Effective Data Access Control for Multi-authority Cloud Storage Systems[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(11): 1790-1801.
|
| [16] |
YANG K, JIA X H. Expressive, Efficient,Revocable Data Access Control for Multi-Authority Cloud Storage[J]. IEEE Transactions on Parallel and Distributed Systems, 2014, 25(7): 1735-1744.
|
| [17] |
WANG Z W, SHA K W, LV W.Slight Homomorphic Signature for Access Controlling in Cloud Computing[J]. Wireless Personal Communications, 2013, 73(1): 51-61.
|
| [18] |
CHEN T S, LIU C H, CHEN T L, et al.Secure Dynamic Access Control Scheme of PHR in Cloud Computing[J]. The Journal of Supercomputing, 2014, 67(3): 711-722.
|
| [19] |
XU L L, TANG S H.Verifiable Computation with Access Control in Cloud Computing[J]. The Journal of Supercomputing, 2014, 69(2): 528-546.
|
| [20] |
吕从东,韩臻,马威. 云存储服务端数据存储加密机制的设计和实现[J]. 信息网络安全,2014,(6):1-5.
|
| [21] |
HASSEN H R, BOUABDALLAH A, BETTAHAR H, et al.Key Management for Content Access Control in A Hierarchy[J]. Computer Networks, 2007, 51(11): 3197-3219.
|
 ), Da-jun ZHANG1, Yun-fa LI2
), Da-jun ZHANG1, Yun-fa LI2