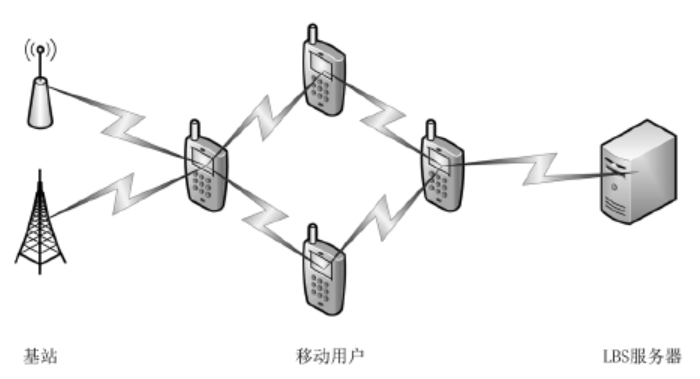
| [1] |
Gruteser M, Grunwald D.Anonymous Usage of Location-based Services through Spatial and Temporal Cloaking[C] Proceedings of the 1stinternational conference on Mobile systems, applications and services. New York: ACM, 2003: 31-42.
|
| [2] |
Chow C Y,Mokbel M F,Aref W G.Casper*: Query processing for location services without compromisingprivacy[J].ACM Transactions on Database Systems,2009,34(4):24-48.
|
| [3] |
Gedik B, Liu L.Location Privacy in Mobile Systems: A Personalized Anonymization Model[C] Proceedings of the 25th IEEE International Conference on Distributed Computing Systems. Washington:IEEE,2005:620-629.
|
| [4] |
YiuM L, Jensen C S, Huang X, et al. SpaceTwist Managing the Trade-Offs Among Location Privacy, Query Performance,and Query Accuracy in Mobile Services[C] IEEE 24th International Conference on Data Engineering. Caucun:ICDE, 2008:366-375.
|
| [5] |
黄毅,霍峥,孟小峰.CoPrivacy:一种用户协作无匿名区域的位置隐私保护方法[J].计算机学报,2011,34(10):1976-1985.
|
| [6] |
Chow C Y, Mokbel M F, Liu X.Spatial Cloaking for Anonymous Location-based Services in Mobile Peer-to-Peer Environment[J]. Geoinformatica,2011,15(2):351-380.
|
| [7] |
王嘉慧,程久军. P2P模式下基于网格扩增的位置匿名算法[J].计算机科学,2014,04:90-94.
|
| [8] |
Xue M, Kalnis P, Pung H K.Location Diversity: Enhanced Privacy Protection in Location Based Services[C] Proceedings of the 4th International Symposium on Location and Context Awareness. Berlin Heidelberg:Springer-Verlag,2009:70-87.
|
| [9] |
Brinkhoff T.A framework for generating network based moving objects[J].Geoinformatica,2000,6(2):153-180.
|
| [10] |
韩伟红,隋品波,贾焰. 大规模网络安全态势分析与预测系统YHSAS[J]. 信息网络安全,2012,(8):11-14.
|
| [11] |
黄心砚,易平. DSR协议下数据包攻击及防御机制[J]. 信息网络安全,2012,(7):35-39.
|
| [12] |
蒲石,陈周国,祝世雄. 震网病毒分析与防范[J]. 信息网络安全,2012,(2):40-43.
|
 ), HE Yong-zhong, LIU Ji-qiang
), HE Yong-zhong, LIU Ji-qiang