Netinfo Security ›› 2022, Vol. 22 ›› Issue (12): 87-95.doi: 10.3969/j.issn.1671-1122.2022.12.010
Previous Articles Next Articles
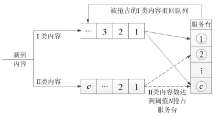
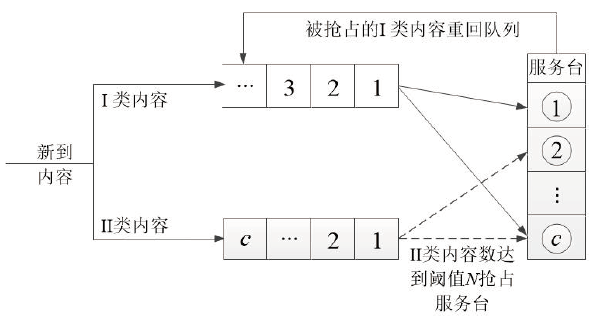
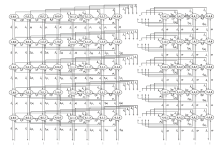
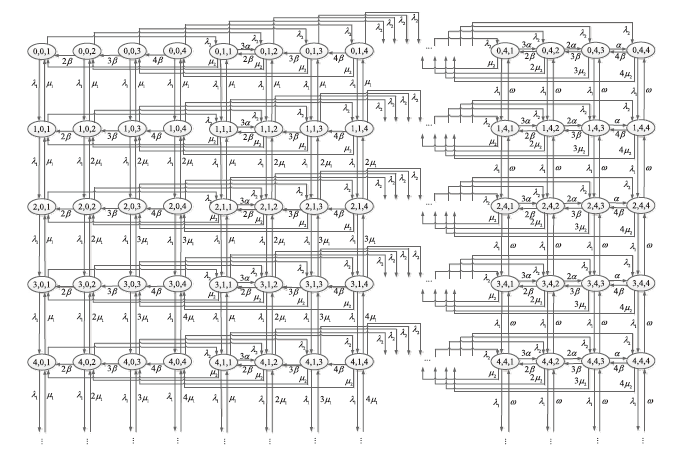
Performance Analysis of P2P Networks Based on N-Preemptive Strategy and Variable Number of Players
YAN Miao, MA Zhanyou( ), JIANG Zishu, QIN Guoli
), JIANG Zishu, QIN Guoli
- School of Science, Yanshan University, Qinhuangdao 066004, China
-
Received:2022-08-26Online:2022-12-10Published:2022-12-30 -
Contact:MA Zhanyou E-mail:mzhy55@ysu.edu.cn
CLC Number:
Cite this article
YAN Miao, MA Zhanyou, JIANG Zishu, QIN Guoli. Performance Analysis of P2P Networks Based on N-Preemptive Strategy and Variable Number of Players[J]. Netinfo Security, 2022, 22(12): 87-95.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.12.010
| [1] | CAI Kunqi, ZHAO Anxue, XING Jieqing. Implementation of Process Communication Based on Client/Server Mode[J]. Wireless Internet Technology, 2021, 18(24): 5-6. |
| 蔡坤琪, 赵安学, 邢洁清. 基于Client/Server模式的进程通信实现研究[J]. 无线互联科技, 2021, 18(24):5-6. | |
| [2] | HUANG Yan, XU Ke, LI Haitao, et al. Large-Scale P2P VOD System: Focusing on Clients[J]. Science China: Information Sciences, 2011, 41(11): 1356-1371. |
| 黄琰, 徐恪, 李海涛, 等. 大规模P2P视频点播系统:聚焦客户端[J]. 中国科学:信息科学, 2011, 41(11): 1356-1371. | |
| [3] | LIU Xianpo, WANG Yamin, WEN Haoyu. Research of the Queues of Searching Information Resource in P2P Based on the Theory of Queues[J]. Journal of Information, 2008(2): 125-128. |
| 刘先泼, 王亚民, 温浩宇. 基于排队论的P2P信息资源搜索请求队列模型研究[J]. 情报杂志, 2008(2):125-128. | |
| [4] | LI Yipeng, REN Yong, YUAN Jian, et al. Traffic Analysis Model for P2P File Sharing Network[J]. Journal of Tsinghua University(Science and Technology), 2011, 51(6): 745-749. |
| 李一鹏, 任勇, 袁坚, 等. 一种P2P文件共享网络流量分析模型[J]. 清华大学学报(自然科学版), 2011, 51(6):745-749. | |
| [5] | JIN Shunfu, LI Yang, LIU Jianping, et al. Strategies of Nash Equilibrium and Social Optimization for Online Mechanisms of P2P Nodes[J]. Journal of Jilin University(Engineering and Technology Edition), 2016, 46(1): 296-302. |
| 金顺福, 李洋, 刘建平, 等. P2P节点在线机制的纳什均衡和社会最优策略[J]. 吉林大学学报(工学版), 2016, 46(1): 296-302. | |
| [6] | SAMA H R, VEMURI V K, TALAGADADEEVI S R, et al. Analysis of an N-Policy M X/M/1 Two-Phase Queueing System with State-Dependent Arrival Rates and Unreliable Server[J]. International Information and Engineering Technology Association, 2019, 24(3): 233-240. |
| [7] | CHEN Wei, SHUANG Kai, SU Sen, et al. A Heuristic Chunk Scheduling Algorithm Reducing Delay for Mesh-Pull P2P Live Streaming[C]// IEEE.2009 2nd IEEE International Conference on Broadband Network& Multimedia Technology. New York: IEEE, 2009: 706-710. |
| [8] |
WANG Zhaobin, FANG Lei, ZHU Sheng. Strategic Behavior in Queues with the Effect of the Number of Customers Behind[J]. Operations Research Letters, 2020, 48(5): 646-651.
doi: 10.1016/j.orl.2020.08.003 URL |
| [9] | LIU Bin, ZHAO Yiqiang. Tail Asymptotics for a Retrial Queue with Bernoulli Schedule[EB/OL]. [2022-07-06]. https://arxiv.org/pdf/1804.00984.pdf. |
| [10] | YANG Yahui, NIU Zhenying, XU Ke. Optimizing Design of Server Deployment in P2P Streaming System[J]. Journal of Computer Research and Development, 2010, 47(7): 1219-1224. |
| 杨雅辉, 钮振瑛, 徐恪. P2P流媒体系统服务器部署的优化设计[J]. 计算机研究与发展, 2010, 47(7):1219-1224. | |
| [11] | CHEN Xiaoming, LI Zhoujun. A Survey: The Performance Optimization in P2P System[J]. Computer Science, 2006, 33(11): 21-24. |
| 陈小明, 李舟军. P2P系统的性能优化:研究综述[J]. 计算机科学, 2006, 33(11):21-24. | |
| [12] |
PRIYA B, GNANASEKARAN T. To Optimize Load of Hybrid P2P Cloud Data-Center Using Efficient Load Optimization and Resource Minimization Algorithm[J]. Peer-to-Peer Networking and Applications, 2020, 13(2): 717-728.
doi: 10.1007/s12083-019-00795-3 URL |
| [13] | ARIRIGUZO M, MBACHU C B. Performance and Stability Analyses of TCP Queue Based Computer Network[J]. Journal of Engineering Research and Reports, 2020, 17(4): 18-24. |
| [14] | WANG Miao, XU Lisong, RAMAMURTHY B. Linear Programming Models for Multi-Channel P2P Streaming Systems[C]// IEEE. 2010 Proceedings IEEE INFOCOM. New York: IEEE, 2010: 1-5. |
| [15] | MA Zhanyou, WANG Wenbo, WANG Zhe, et al. The Discrete Time Working Vacation Queue with Non-Preemptive Priority and Variable Service Rates[J]. Journal of Henan Normal University(Natural Science Edition), 2018, 46(1): 23-28. |
| 马占友, 王文博, 王哲, 等. 带非抢占优先权和可变服务率的离散工作休假排队[J]. 河南师范大学学报(自然科学版), 2018, 46(1):23-28. | |
| [16] | WEI Hongyuan, WEI Yingyuan. Delayed N-Strategy Geo/G/1 Queuing System with Start-Up Timeand its Application in ATM Network[J]. Journal of Hexi University, 2019, 35(2): 6-15. |
| 魏宏源, 魏瑛源. 带启动时间的延迟N-策略Geo/G/1排队系统及其在ATM网络中的应用[J]. 河西学院学报, 2019, 35(2):6-15. | |
| [17] | MA Zhanyou, WANG Wenbo, ZHENG Xiaoming. The M/M/c Queueing Model with Preemptive Priority and Multiple Synchronous Working Vacation[J]. Journal of Chongqing Normal University(Natural Science), 2018, 35(3): 96-100. |
| 马占友, 王文博, 郑晓铭. 带抢占优先权和同步多重工作休假的M/M/c排队模型[J]. 重庆师范大学学报(自然科学版), 2018, 35(3):96-100. | |
| [18] | TIAN Longmei, ZHAO Ning, LIU Wenqi. Customer Strategy Analysis of M/G/1 Queueing System with Purchasable Priority[J]. Journal of Nanjing University of Science and Technology, 2020, 44(2): 224-229. |
| 田龙妹, 赵宁, 刘文奇. 可购买优先权的M/G/1排队系统顾客策略分析[J]. 南京理工大学学报, 2020, 44(2):224-229. | |
| [19] |
WANG Shuo, XU Xiuli. The Balking Strategies of Fluid Vacation Model with Setup Time[J]. Acta Mathematicae Applicatae Sinica, 2018, 41(6): 846-857.
doi: 10.12387/C2018066 |
|
王硕, 徐秀丽. 带启动时间的休假流体模型的止步策略分析[J]. 应用数学学报, 2018, 41(6):846-857.
doi: 10.12387/C2018066 |
|
| [20] |
SINGLA N, KAUR H. A Two-State Retrial Queueing Model with Feedback Having Two Identical Parallel Servers[J]. Indian Journal of Science and Technology, 2021, 14(11): 915-931.
doi: 10.17485/IJST/v14i11.1167 URL |
| [21] | NEUTS M F. Matrix-Geometric Solutions in Stochastic Models[M]. Baltimore: Johns Hokpins University Press, 1981. |
| [22] |
VINOD B. Exponential Queues with Server Vacations[J]. Journal of the Operational Research Society, 1986, 37(10): 1007-1014.
doi: 10.1057/jors.1986.170 URL |
| [1] | LYU Kewei, CHEN Chi. Research on Proactive Generation Protocol of Beaver Triples [J]. Netinfo Security, 2022, 22(12): 16-24. |
| [2] | WANG Qing, XU Guotian. An Encryption Algorithm Based on Improved Logistic Mapping and Dual-Image Blending [J]. Netinfo Security, 2022, 22(12): 76-86. |
| [3] | GUO Sensen, WANG Tongli, MU Dejun. Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder [J]. Netinfo Security, 2022, 22(12): 7-15. |
| [4] | WANG Sidie, MA Zhaofeng, LUO Shoushan, XU Danheng. Data Privacy-Preserving Scheme on Blockchain for Heterogeneous Multi-Chain [J]. Netinfo Security, 2022, 22(12): 67-75. |
| [5] | YIN Ying, ZHOU Zhihong, YAO Lihong. Research on LSTM-Based CAN Intrusion Detection Model [J]. Netinfo Security, 2022, 22(12): 57-66. |
| [6] | WANG Yong, CHEN Lijie, ZHONG Meiling. Progress in Blockchain Solutions Based on Zero-Knowledge Proof [J]. Netinfo Security, 2022, 22(12): 47-56. |
| [7] | XU Ruzhi, LYU Changran, LONG Yan, LIU Yuanbin. Defense Research of High-Hidden Data Attack in Industry Control System [J]. Netinfo Security, 2022, 22(12): 34-46. |
| [8] | ZHANG Yu, SUN Guangmin, ZHAI Peng, LI Yu. A Provably Secure Traceability Authentication Protocol Based on Chebyshev Chaotic Map [J]. Netinfo Security, 2022, 22(12): 25-33. |
| [9] | CHEN Yan, WEI Xiang, LU Zhen. Research on Testing Approaches for Network Security Products in Cloud Computing Environment [J]. Netinfo Security, 2022, 22(12): 1-6. |
| [10] | YAN Yan, ZHANG Xiong, FENG Tao. Proportional Differential Privacy Budget Allocation Method for Partition and Publishing of Statistical Big Data [J]. Netinfo Security, 2022, 22(11): 24-35. |
| [11] | LIU Zhenya, LIN Jingqiang. Analysis of SM2 Encryption and Decryption Vulnerability in OpenSSL [J]. Netinfo Security, 2022, 22(11): 47-54. |
| [12] | PENG Shufan, CAI Manchun, LIU Xiaowen, MA Rui. Deepfake Detection Algorithm Based on Image Fine-Grained Features [J]. Netinfo Security, 2022, 22(11): 77-84. |
| [13] | HUANG Zilong, ZHAN Dongyang, YE Lin, ZHANG Hongli. A Secure Container Management Approach Based on Virtual Machine Introspection [J]. Netinfo Security, 2022, 22(11): 55-61. |
| [14] | LIN Faxin, ZHANG Jian. Design and Implementation of Abnormal Behavior Detection System for Virtualization Platform [J]. Netinfo Security, 2022, 22(11): 62-67. |
| [15] | SONG Jing, DIAO Run, ZHOU Jie, QI Jianhuai. The Optimization Method of Industrial Control System Functional Safety and Information Security Policy [J]. Netinfo Security, 2022, 22(11): 68-76. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||