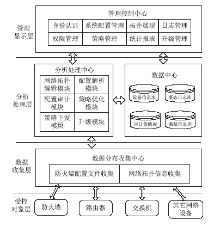
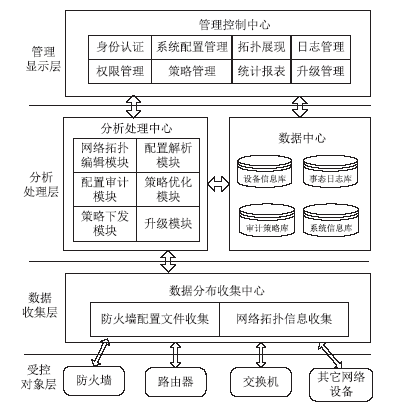
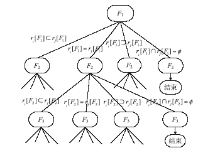
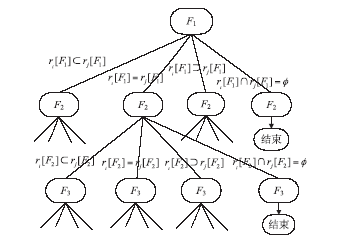
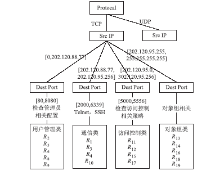
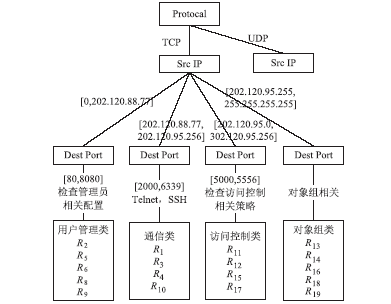
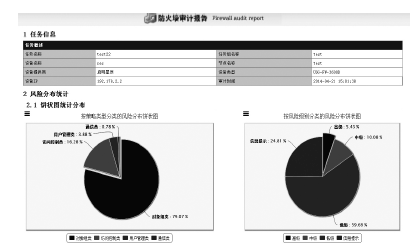
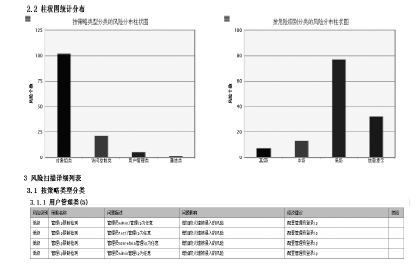
| [1] |
李林,卢显良. 一种快速的防火墙规则冲突检测算法[J]. 计算机应用研究,2008,25(1):266-267.
|
| [2] |
傅鹤岗,张李. 基于默认规则的防火墙优化方法[J]. 计算机工程,2011,37(20):103-104.
|
| [3] |
Wool A.A Quantitative Study of Firewall Configuration Errors[J]. IEEE computer society, 2004, 37(6): 62-67.
|
| [4] |
Hamed H, Al-Shaer E.Dynamic rule-ordering optimization for high-speed firewall filtering[C]//Proceedings of the 2006 ACM Symposium on Information, computer and communications security. ACM, 2006: 332-342.
|
| [5] |
吴晓刚. 防火墙配置的异常检测与优化研究[D]. 广州:广州大学,2007.
|
| [6] |
张昭理,肖海军,洪帆. 一种防火墙规则冲突检测算法[J]. 计算机工程与应用,2007,43(15):111-113.
|
| [7] |
杨奕,杨树堂,陈建宁,等. 基于统计分析与规则冲突检测的防火墙优化[J]. 计算机工程,2008,34(15):129-131.
|
| [8] |
程勇,秦祖福,傅建明. 有序二叉决策图在防火墙规则库设计中的应用[J]. 武汉大学学报:理学版,2006,52(1):77-80.
|
| [9] |
施荣华,莫锐,赵文涛. 一种基于冲突检测的无关联规则集匹配算法[J]. 计算机工程与科学,2010,32(10):1-4.
|
| [10] |
朱思峰,王华东,魏荣华. 基于内分泌机制的防火墙自适应调控算法[J]. 计算机科学2009,36(11):238-241.
|
| [11] |
周东浩,王勇军. 防火墙扩展match模块匹配算法优化[J]. 计算机工程与设计,2011,32(3):766-769.
|
| [12] |
Al-SHARE E, HAMED H.Taxonomy of conflicts in network security policies[J]. Communications Magazine, IEEE, 2006, 44(3): 134-141.
|
| [13] |
袁峰,赵杰,陈靖. 基于ARM的防火墙系统设计与实现[J]. 信息网络安全,2013,(6):46-49.
|
| [14] |
曹子建,赵宇峰,容晓峰. 网络入侵检测与防火墙联动平台设计[J]. 信息网络安全,2012,(9):12-14.
|
| [15] |
傅慧. 动态包过滤防火墙规则优化研究[J]. 信息网络安全,2012,(12):12-14.
|