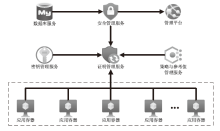
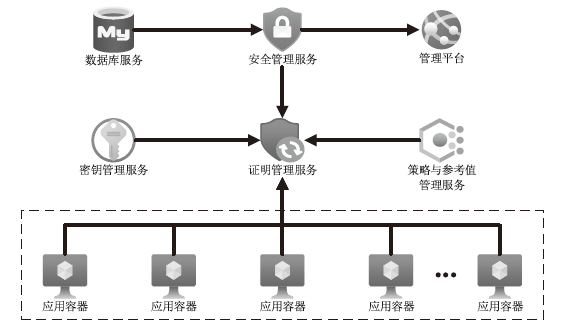
Netinfo Security ›› 2025, Vol. 25 ›› Issue (2): 306-326.doi: 10.3969/j.issn.1671-1122.2025.02.011
Previous Articles Next Articles
A Trusted Runtime Monitoring Method Based on eBPF for Container
HUANG Ke1, LI Xuan2, ZHOU Qingfei2, SHANG Ketong1, QIN Yu1( )
)
- 1. Trusted Computing and Information Assurance Laboratory, Institute of Software Chinese Academy of Sciences, Beijing 100190, China
2. China Greatwall Technology Group Co., Ltd., Shenzhen 518028, China
-
Received:2024-04-18Online:2025-02-10Published:2025-03-07
CLC Number:
Cite this article
HUANG Ke, LI Xuan, ZHOU Qingfei, SHANG Ketong, QIN Yu. A Trusted Runtime Monitoring Method Based on eBPF for Container[J]. Netinfo Security, 2025, 25(2): 306-326.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.02.011
| 日志 类别 | 日志内容 |
|---|---|
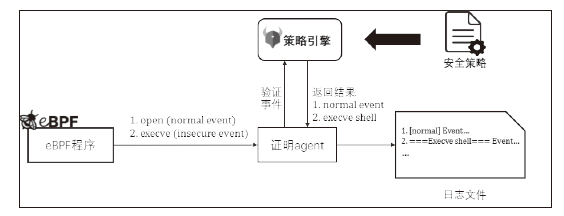
| 安全 事件 | 2024/03/18 18:22:56 [NORMAL] Event:{host:iscas, syscall: openat}, Container:{image: ubuntu, id: 7c963ca76858}, Process:{proc: cat, pid: 1964179, args: cat a.txt} |
| 非安全 事件 | 2024/03/18 18:23:26 [INSECURE] Unsafe:[execve shell], Event:{host:iscas, syscall: execve, args:filename=/usr/bin/sh, time: 1710757407140027468},Container:{image: ubuntu, id: 7c963ca76858, name: pedantic_joliot},Process:{proc: exe, pid: 1964363, parent: exe, args: exe, caps: CAP_CHOWN …} |
| 日志 类别 | 日志内容 |
|---|---|
| 进程 | 2023/10/11 11:37:34 [INSECURE] Unsafe:[execve shell], Event:[host:iscas, syscall: execve, args:filename-/usr/bin/sh, time: 1696995457372813650}, Container:{image: ubuntu, id: b4863b267450, name: zealous booth), Process:(proc: bash, pid: 586640, parent: bash, args: bash, caps:CHOWN…} |
| 权能 | 2023/10/11 11:57:09 [INSECURE] Unsafe:[illegal capability], Event:{host:iscas, syscall: openat, args:dirfd=-100(AT_FDCWD) name= /etc/inputrc flags=1(O_RDONLY) mode=0, time:1696996632007667434}, Container:{image:ubuntu, id: 19d1a223351c, name: bold_cartwright}, Process:{proc: bash, pid: 590051, parent: null, args: bash, caps: CHOWN…} |
| 文件 | 2023/10/11 15:11:56 [INSECURE] Unsafe:[opening passwd], Event:{host:iscas, syscall: openat, args:dirfd=-100(AT_FDCWD) name=passwd(/etc/passwd) flags=1(O_RDONLY) mode=0, time:1697008319216479547}, Container:{image: ubuntu, id: a3da9f2deb4b, name: vigilant_carv er}, Process:{proc: cat, pid: 593176, parent: bash, args: cat passwd, caps: CHOWN…} |
| 网络 | 2023/10/11 15:45:15 [INSECURE] Unsafe:[connect outside], Event:{host:iscas, syscall: connect, args:fd=3(<4>) addr=192.168.190.133:8888, time: 1697010318361221228}, Container:{image: ubuntu, id: a3da9f2deb4b, name: vigilant_carver}, Process:{proc: client, pid: 596930, parent: bash, args: client, caps: CHOWN…} |
| Benchmark | 对照组 | 本文方案 |
|---|---|---|
| Apache/请求数·s-1 | 43232.90 | 38370.13(-11.25%) |
| 内核编译/s | 121.58 | 124.68(2.55%) |
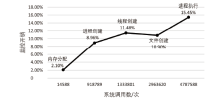
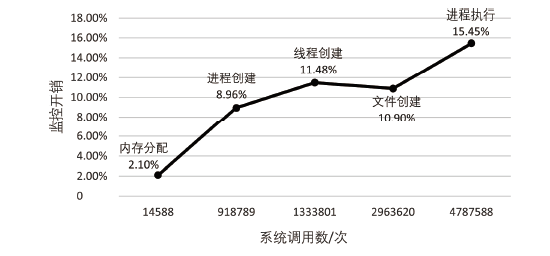
| 文件创建/ms·事件-1 | 14.96 | 16.59(10.90%) |
| 线程创建/ms·事件-1 | 17.51 | 19.52(11.48%) |
| 进程创建/ms·事件-1 | 26.44 | 28.81(8.96%) |
| 进程执行/ms·事件-1 | 35.99 | 41.55(15.45%) |
| 内存分配/ns·事件-1 | 54.73 | 55.88(2.10%) |
| 随机读/MB·s-1 | 67.50 | 66.40(-1.63%) |
| 随机写/MB·s-1 | 732.00 | 681.00(-6.97%) |
| [1] | CNCF. CNCF 2022 ANNUAL SURVEY[EB/OL]. (2022-12-04)[2024-04-12]. https://www.cncf.io/reports/cncf-annual-survey-2022/. |
| [2] | SYSDIG. Sysdig 2023 Cloud-Native Security and Usage Report[EB/OL]. (2023-09-06)[2024-04-12]. https://sysdig.com/2023-cloud-native-security-and-usage-report/. |
| [3] | LINUX. eBPF Instruction Set Specification, v1.0[EB/OL]. (2023-09-08)[2024-04-12]. https://www.kernel.org/doc/html/next/bpf/instruction-set.html. |
| [4] | JONATHAN C. A JIT for Packet Filters[EB/OL]. (2011-04-08)[2024-04-12]. https://lwn.net/Articles/437981/. |
| [5] | LINUX. eBPF Verifier[EB/OL]. (2024-04-08)[2024-04-12]. https://docs.kernel.org/bpf/verifier.html. |
| [6] | GREGG B. BPF Performance Tools[M]. New York: Addison-Wesley Professional, 2019. |
| [7] | STEVEN R. Unified Tracing Platform[EB/OL]. (2019-10-28)[2024-04-12]. https://static.sched.com/hosted_files/osseu19/5f/unified-tracing-platform-oss-eu-2019.pdf. |
| [8] | JIM K. Kernel Probes (Kprobes)[EB/OL]. (2023-05-12)[2024-04-08]. https://docs.kernel.org/trace/kprobes.html. |
| [9] | MATHIEU D. Using the Linux Kernel Tracepoints[EB/OL]. (2024-01-08)[2024-04-12]. https://docs.kernel.org/trace/tracepoints.html#using-the-linux-kernel-tracepoints. |
| [10] | FOURNIER G, AFCHAIN S, BAUBEAU S. Runtime Security Monitoring with eBPF[EB/OL]. (2021-09-08)[2024-04-12]. https://www.semanticscholar.org/paper/Runtime-Security-Monitoring-with-eBPF-Fournier-Afchain/8a768ccb634f7527885cae4cd5348eba01065b80. |
| [11] | LINUX. Seccomp BPF (SECure COMPuting with Filters)[EB/OL]. (2024-01-18)[2024-04-12]. https://www.kernel.org/doc/html/latest/userspace-api/seccomp_filter.html. |
| [12] | JONATHAN C. KRSI — The Other BPF Security Module[EB/OL]. (2019-12-27)[2024-04-12]. https://lwn.net/Articles/808048/. |
| [13] | FINDLAY W, SOMAYAJI A, BARRERA D. Bpfbox: Simple Precise Process Confinement with Ebpf[C]// ACM. Proceedings of the 2020 ACM SIGSAC Conference on Cloud Computing Security Workshop. New York: ACM, 2020: 91-103. |
| [14] | TIAN D J, HERNANDEZ G, CHOI J I, et al. Lbm: A Security Framework for Peripherals within the Linux Kernel[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 967-984. |
| [15] | AGMAN Y, HENDLER D. BPFroid: Robust Real Time Android Malware Detection Framework[EB/OL]. (2021-06-01)[2024-04-12]. https://arxiv.org/pdf/2105.14344v1. |
| [16] | FALCO. Falco[EB/OL]. (2024-01-21)[2024-03-21]. https://falco.org/. |
| [17] | LIM S Y, STELEA B, HAN X, et al. Secure Namespaced Kernel Audit for Containers[C]// ACM. Proceedings of the ACM Symposium on Cloud Computing. New York: ACM, 2021: 518-532. |
| [18] | FINDLAY W, BARRERA D, SOMAYAJI A. Bpfcontain: Fixing the Soft Underbelly of Container Security[EB/OL]. (2021-02-13)[2024-04-12]. https://arxiv.org/pdf/2102.06972. |
| [19] | BELAIR M, LANIEPCE S, MENAUD J M. SNAPPY: Programmable Kernel-Level Policies for Containers[C]// ACM. Proceedings of the 36th Annual ACM Symposium on Applied Computing. New York: ACM, 2021: 1636-1645. |
| [20] | ISOVALENT. Tetragon[EB/OL]. (2023-12-01)[2024-04-12]. https://github.com/cilium/tetragon. |
| [21] | GHAVAMNIA S, PALIT T, BENAMEUR A, et al. Confine: Automated System Call Policy Generation for Container Attack Surface Reduction[EB/OL]. (2020-09-03)[2024-04-12]. https://www.xueshufan.com/publication/3092506792. |
| [22] | SULTAN S, AHMAD I, DIMITRIOU T. Container Security: Issues, Challenges, and the Road Ahead[J]. IEEE access, 2019, 7: 52976-52996. |
| [23] | BOGAERTS P. Arp Spoofing Docker Containers[EB/OL]. (2024-02-07)[2024-03-26]. https://dockersec.blogspot.com/2017/01/arp-spoofing-docker-containers_26.html. |
| [24] | SPAHN N, HANKE N, HOLZ T, et al. Container Orchestration Honeypot: Observing Attacks in the Wild[C]// IEEE. Proceedings of the 26th International Symposium on Research in Attacks, Intrusions and Defenses. New York: IEEE, 2023: 381-396. |
| [25] | Michael Larabel and Matthew Tippett. Phoronix Test Suite[EB/OL]. (2024-02-12)[2024-04-12]. http://www.phoronix-test-suite.com/. |
| [1] | LIU Sinuo, RUAN Shuhua, CHEN Xingshu, ZHENG Tao. An eBPF-Based Threat Observability System for Cloud-Oriented Environment [J]. Netinfo Security, 2024, 24(4): 534-544. |
| [2] | XIA Yihang, ZHANG Zhilong, WANG Muzi, CHEN Libo. Dependency-Based Vulnerability Detection Method in Container Supply Chain [J]. Netinfo Security, 2023, 23(2): 76-84. |
| [3] | WU Shenglin, LIU Wanggen, YAN Ming, WU Jie. A Real-Time Anomaly Detection System for Container Clouds Based on Unsupervised System Call Rule Generation [J]. Netinfo Security, 2023, 23(12): 91-102. |
| [4] | BIAN Manlin, WANG Liming. Analysis and Research on Vulnerability of Docker Container Isolation in Cloud Environment [J]. Netinfo Security, 2020, 20(7): 85-95. |
| [5] | Jin WANG, Xiao YU, Chang LIU, Bo ZHAO. A Remote Attestation Scheme for Intelligent Mobile Terminal Based on SDKey in Smart Grid Environment [J]. Netinfo Security, 2018, 18(7): 1-6. |
| [6] | Bo FAN, Runkai YANG, Lin LI. Research on Establish SSH-based Trusted Channels [J]. Netinfo Security, 2018, 18(1): 45-51. |
| [7] | Yaqi ZHANG, Yongzhong HE, Aimin YU. A SSH Protocol Based on the Trusted Attestation of a Third Party Platform [J]. Netinfo Security, 2016, 16(12): 34-45. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||