Netinfo Security ›› 2025, Vol. 25 ›› Issue (1): 13-26.doi: 10.3969/j.issn.1671-1122.2025.01.002
Previous Articles Next Articles
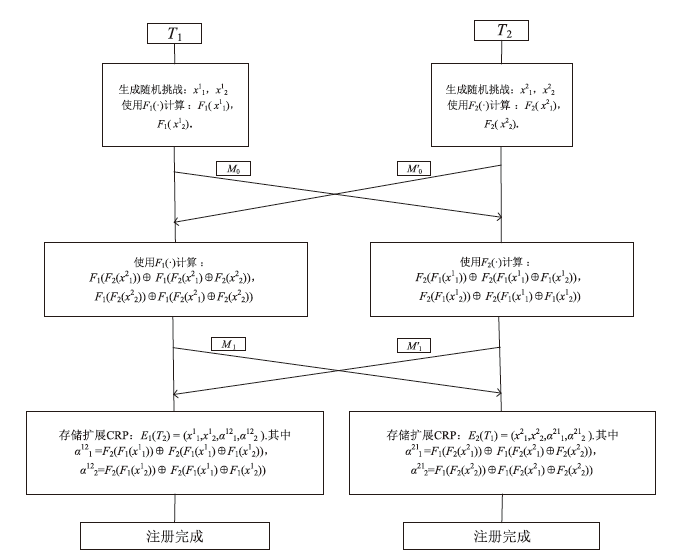
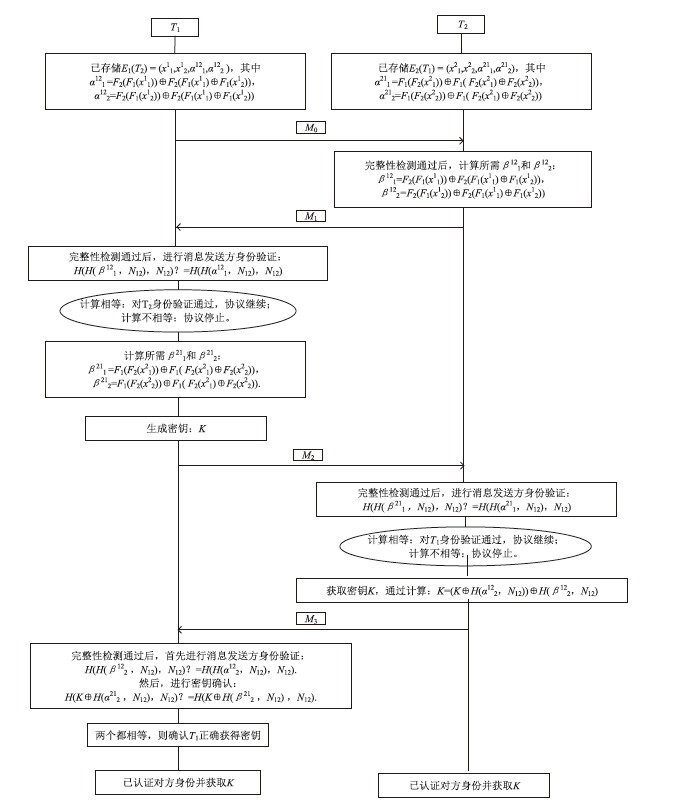
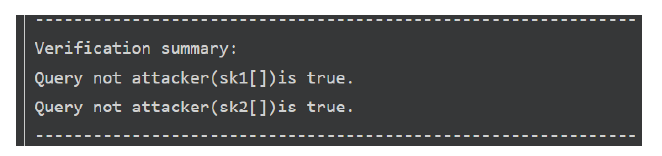
PUF-Based Smart Terminal Authentication Protocol for Power Internet of Things
YUAN Zheng1,2( ), ZHANG Yuefei1, FENG Xiao3, QIAO Yaxin1
), ZHANG Yuefei1, FENG Xiao3, QIAO Yaxin1
- 1. Department of Cryptography Science and Technology, Beijing Institute of Electronic Science and Technology, Beijing 100070, China
2. China StarNet Network System Research Institute Co., Ltd., Beijing 100029, China
3. State Grid Information & Telecommunication Industry Co., Ltd., Beijing 100031, China
-
Received:2024-07-11Online:2025-01-10Published:2025-02-14 -
Contact:YUAN Zheng E-mail:sxzyyz5318@163.com
CLC Number:
Cite this article
YUAN Zheng, ZHANG Yuefei, FENG Xiao, QIAO Yaxin. PUF-Based Smart Terminal Authentication Protocol for Power Internet of Things[J]. Netinfo Security, 2025, 25(1): 13-26.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.01.002
| 符号 | 描述 |
|---|---|
| Ti | 智能终端i |
| idi | 智能终端i身份标识号 |
| xis | 智能终端i生成的第s个挑战x |
| αijs | 智能终端i用于验证智能终端j的真实性的第s个模糊响应α |
| βijs | 智能终端j用来向智能终端i证明其真实性的第s个模糊响应β |
| Fi(·) | 智能终端i的PUF函数 |
| Fi(xis) | 智能终端i的PUF函数对智能终端i生成的第s个挑战x的响应 |
| H(·) | 一个公共散列函数 |
| H(*) | 用于保护消息M完整性的散列 |
| ⊕ | 异或运算符 |
| Ei(Tj) | 智能终端i用于挑战和验证智能终端j的真实性的扩展CRP |
| Ni | 智能终端i生成的随机数 |
| Nij | Ni和Nj的异或,即Ni⊕Nj |
| i|j | i或者j,两者其中的一个 |
| K | 加解密密钥 |
| [1] | LIANG Xiaolin, SUN Donglei, LI Wensheng. Composition Form and Function Configuration of Intelligent Terminal Based on Edge Computing for Power Internet of Things[C]// The Organizing Committee of the International Conference on Renewable Energy and Environmental Protection. 2020 5th International Conference on Renewable Energy and Environmental Protection (ICREEP2020). Bristol: IOP, 2021: 1-7. |
| [2] | ZOU Zhenwan, LI Feng, HOU Yingsa, et al. Research on Security Protection Technology of Intelligent Terminal of Electricity Internet of Things[C]// IEEE. 2021 IEEE 5th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC). New York: IEEE, 2021: 1467-1470. |
| [3] | GAO Yansong, Al-SARAWI S F, ABBOTT D. Physical Unclonable Functions[J]. Nature Electronics, 2020, 3(2): 81-91. |
| [4] |
PAPPU R, RECHT B, TAYLOR J, et al. Physical One-Way Functions[J]. Science, 2002, 297(5589): 2026-2030.
pmid: 12242435 |
| [5] | LIU Dan, GUO Limin, YU Jun, et al. A Safe Two-Way Certification Agreement Based on SRAM PUF[J]. Code Journal, 2017, 4(4): 360-371. |
|
刘丹, 郭丽敏, 俞军, 等. 一种基于SRAM PUF的安全双向认证协议[J]. 密码学报, 2017, 4(4):360-371.
doi: 10.13868/j.cnki.jcr.000188 |
|
| [6] | SHAMSOSHOARA A, KORENDA A, AFGHAH F, et al. A Survey on Physical Unclonable Function (PUF)-Based Security Solutions for Internet of Things[EB/OL]. (2020-12-24)[2024-05-08]. https://www.sciencedirect.com/science/article/pii/S1389128620312275. |
| [7] | YOON S, KIM B, KANG Y, et al. Puf-Based Authentication Scheme for Iot Devices[C]// IEEE. 2020 International Conference on Information and Communication Technology Convergence (ICTC). New York: IEEE, 2020: 1792-1794. |
| [8] | GHAFI B K, MAYBODI B M N. A Distributed PUF-Based Mutual Authentication System with Self-Correction[C]// IEEE. 2020 28th Iranian Conference on Electrical Engineering (ICEE). New York: IEEE, 2020: 1-5. |
| [9] | QURESHI M A, MUNIR A. PUF-RAKE: A PUF-Based Robust and Lightweight Authentication and Key Establishment Protocol[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 19(4): 2457-2475. |
| [10] | ZHENG Yue, CHANG C H. Secure Mutual Authentication and Key-Exchange Protocol Between PUF-Embedded IoT Endpoints[C]// IEEE. 2021 IEEE International Symposium on Circuits and Systems (ISCAS). New York: IEEE, 2021: 1-5. |
| [11] | GUO Xuan. The Company Has Issued the Opinion on Comprehen Sively Deepening Reform and Striving for Breakthroughs[N]. State Grid Corporation of China, 2020-01-14( 2). |
| 郭萱. 公司印发《关于全面深化改革奋力攻坚突破的意见》[N]. 国家电网报, 2020-01-14(2). | |
| [12] | HE Fenglu, CHEN Jiaqi, LI Qinhao, et al. The Internet of Things Technology in the Smart Grid[J]. Power System Protection and Control, 2020, 48(3): 58-69. |
| 何奉禄, 陈佳琦, 李钦豪, 等. 智能电网中的物联网技术应用与发展[J]. 电力系统保护与控制, 2020, 48(3):58-69. | |
| [13] |
DONGSHENG Y, DAOHAO W, BOWEN Z, et al. Key Technologies and Application Prospects of Ubiquitous Power Internet of Things[J]. Power Generation Technology, 2019, 40(2): 107-114.
doi: 10.12096/j.2096-4528.pgt.19061 |
| [14] | National Energy Administration. Notice from the National Energy Administration on Issuing the “Action Plan for Electricity Safety Production (2018-2020)”: National Energy Development Safety[2018] No. 55[EB/OL]. (2018-06-27)[2024-05-09]. https://zfxxgk.nea.gov.cn/auto93/201807/t20180705_3206.htm. |
| 国家能源局. 国家能源局关于印发《电力安全生产行动计划(2018-2020年)》的通知:国能发安全[2018]55号[EB/OL]. (2018-06-27)[2024-05-09]. https://zfxxgk.nea.gov.cn/auto93/201807/t20180705_3206.htm. | |
| [15] | TAN Weijie, YANG Yuting, NIU Kun, et al. MI-PUF-Based V2X Vehicle Networking Communication Security Certification Agreement[J]. Information Network Security, 2023, 23(12): 38-48. |
| 谭伟杰, 杨雨婷, 牛坤, 等. 基于MI-PUF的V2X车联网通信安全认证协议[J]. 信息网络安全, 2023, 23(12):38-48. | |
| [16] | SHAMIR A. How to Share A Secret[J]. Communications of the ACM, 1979, 22(11): 612-613. |
| [17] | YANAMBAKA V P, MOHANTY S P, KOUGIANOS E, et al. PMsec: Physical Unclonable Function-Based Robust and Lightweight Authentication in the Internet of Medical Things[J]. IEEE Transactions on Consumer Electronics, 2019, 65(3): 388-397. |
| [18] | DIJK M V, RÜHRMAIR U. Protocol Attacks on Advanced PUF Protocols and Countermeasures[C]// IEEE. 2014 Design, Automation & Test in Europe Conference & Exhibition (DATE). New York: IEEE, 2014: 1-6. |
| [19] | PANDYA D, NARAYAN K R, THAKKAR S, et al. An Overview of Various Authentication Methods and Protocols[J]. International Journal of Computer Applications, 2015, 131(9): 25-27. |
| [20] | KHALAFALLA M, GEBOTYS C. PUFs Deep Attacks: Enhanced Modeling Attacks Using Deep Learning Techniques to Break the Security of Double Arbiter PUFs[C]// IEEE. 2019 Design, Automation & Test in Europe Conference & Exhibition (DATE). New York: IEEE, 2019: 204-209. |
| [21] | BOYD C, GELLERT K. A Modern View on Forward Security[J]. The Computer Journal, 2021, 64(4): 639-652. |
| [22] | YANG Ting, ZHAI Feng, ZHAO Yingjie, et al. Definition and Research Prospects of Ubiquitous Power Internet of Things[J]. Power System Automation, 2019, 43 (13): 9-20, 53. |
| 杨挺, 翟峰, 赵英杰, 等. 泛在电力物联网释义与研究展望[J]. 电力系统自动化, 2019, 43(13): 9-20,53. | |
| [23] | GOPE P. PMAKE: Privacy-Aware Multi-Factor Authenticated Key Establishment Scheme for Advancemetering Infrastructure in Smart Grid[J]. Computer Communications, 2020, 152: 338-344. |
| [24] | AYSU A, GULCAN E, MORIYAMA D, et al. End-to-End Design of a PUF-Based Privacy Preserving Authentication Protocol[C]// Springer. Cryptographic Hardware and Embedded Systems-CHES 2015: 17th International Workshop. Heidelberg: Springer, 2015: 556-576. |
| [1] | XIA Zhe, XIA Xuezhi, LYU Wenjie, ZHANG Mingwu. Certificate-Based Locally Verifiable Aggregate Signature Scheme in VANETs [J]. Netinfo Security, 2025, 25(1): 48-62. |
| [2] | DUAN Haozhe, LI Zhihui, WEI Xingjia, HU Kexin. Quantum Identity Authentication Protocol without Entanglement in d-Dimensional Quantum System [J]. Netinfo Security, 2024, 24(9): 1364-1374. |
| [3] | SUN Zhongxiu, PENG Cheng, FAN Wei. System Broadcast Information Authentication Protocol Based on Certificateless Signature for 5G Network [J]. Netinfo Security, 2024, 24(8): 1220-1230. |
| [4] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [5] | ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems [J]. Netinfo Security, 2024, 24(7): 1015-1026. |
| [6] | HU Chengcong, HU Honggang. Lattice-Based Round-Optimal Password Authenticated Secret Sharing Protocol [J]. Netinfo Security, 2024, 24(6): 937-947. |
| [7] | SHEN Zhuowei, WANG Renbo, SUN Xianjun. A Hierarchical Lightweight Authentication Scheme Based on Merkle Tree and Hash Chain [J]. Netinfo Security, 2024, 24(5): 709-718. |
| [8] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [9] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [10] | CHEN Baogang, ZHANG Yi, YAN Song. Research on Multi-Factor Continuous Trustworthy Identity Authentication for Users in Civil Aviation Air Traffic Control Operational Information Systems [J]. Netinfo Security, 2024, 24(11): 1632-1642. |
| [11] | YAO Mengmeng, WANG Yu, HONG Yuping. The Formal Analysis of SIP Protocol Based on the Recursive Authentication Test [J]. Netinfo Security, 2024, 24(10): 1586-1594. |
| [12] | ZHANG Min, FENG Yongqiang, XU Chunxiang, ZHANG Jianhua. Research on Multi-Factor Authenticated Key Agreement Protocol for Smart Home Networks [J]. Netinfo Security, 2024, 24(1): 133-142. |
| [13] | DAI Yu, ZHOU Fei, XUE Dan. Handover Authentication Protocol Based on Chinese Remainder Theorem Secret Sharing [J]. Netinfo Security, 2023, 23(9): 118-128. |
| [14] | ZHANG Wei, LI Zixuan, XU Xiaoyu, HUANG Haiping. SDP-CoAP: Design of Security Enhanced CoAP Communication Framework Based on Software Defined Perimeter [J]. Netinfo Security, 2023, 23(8): 17-31. |
| [15] | TAN Weijie, YANG Yuting, NIU Kun, PENG Changgen. MI-PUF-Based Secure Authentication Protocol for V2X Communication [J]. Netinfo Security, 2023, 23(12): 38-48. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||