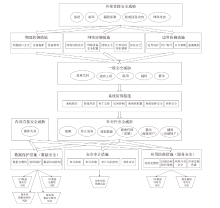
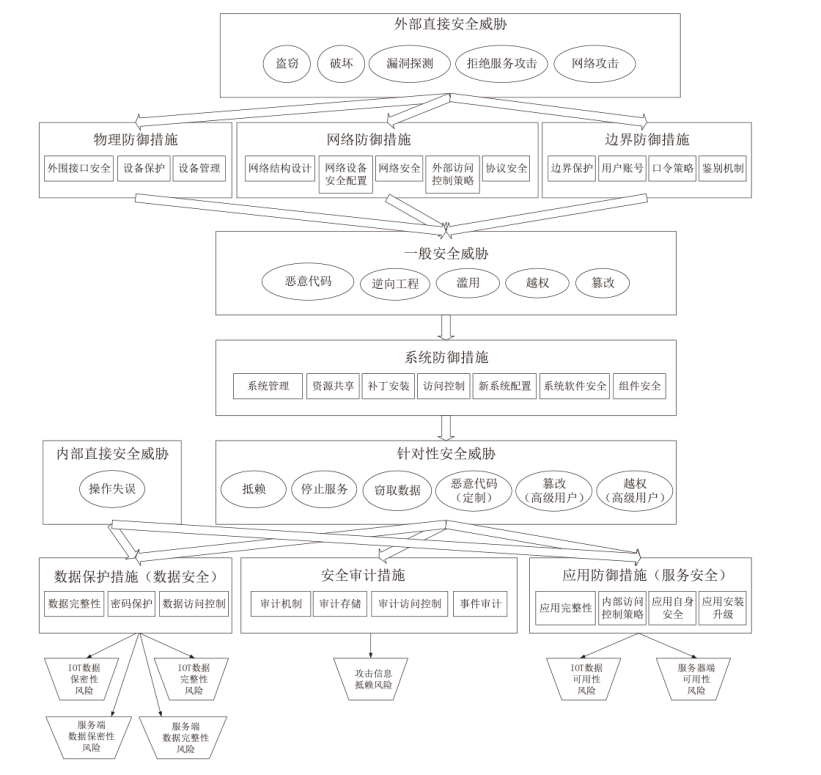
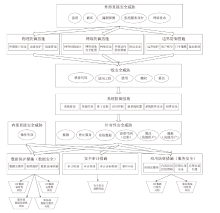
Netinfo Security ›› 2024, Vol. 24 ›› Issue (10): 1595-1603.doi: 10.3969/j.issn.1671-1122.2024.10.014
Previous Articles Next Articles
Systematic Risk Assessment Analysis for Smart Wearable Devices
ZHAO Ge1,2( ), ZHENG Yang3, TAO Zelin3,4
), ZHENG Yang3, TAO Zelin3,4
- 1. The Third Research Institute of the Ministry of Public Security, Shanghai 200031, China
2. Shanghai Engineering Research Center of Cyber and Information Security Evaluation, Shanghai 200031, China
3. Wuxi Trusted Computing Technology Research Institute Co., Ltd., Wuxi 214187, China
4. Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
-
Received:2024-06-01Online:2024-10-10Published:2024-09-27
CLC Number:
Cite this article
ZHAO Ge, ZHENG Yang, TAO Zelin. Systematic Risk Assessment Analysis for Smart Wearable Devices[J]. Netinfo Security, 2024, 24(10): 1595-1603.
share this article
| 脆弱性 分类 | 脆弱点 | 检测项 | 检测 结果 |
|---|---|---|---|
| 边界防御 | 边界保护/用户账号 | — | — |
| 口令策略/鉴别机制 | — | — | |
| 网络通信 | 网络结构设计 | — | — |
| 网络设备安全配置 | 联网环境检测 | 低危 | |
| 网络安全 | HTTPS未校验服务器证书漏洞 | 中危 | |
| 外部访问控制 | 访问境外服务器危险 | 高危 | |
| 协议安全 | 中间人攻击风险 | 高危 | |
| 物理安全 | 外围接口安全/设备管理 | — | — |
| 设备保护 | SD卡数据泄露风险 | 中危 | |
| 系统防御 | 系统管理 | 恶意可执行程序管理漏洞 | 中危 |
| 资源共享/补丁安装 | — | — | |
| 访问控制 | 资源文件泄露风险 | 中危 | |
| 系统配置 | 测试信息残留风险 | 低危 | |
| 系统软件安全 | 敏感函数检测 | 中危 | |
| 组件安全 | WebView组件远程代码执行漏洞 | 高危 | |
| 数据保护 | 数据完整性 | — | — |
| 密码保护 | AES/DES加密算法不安全使用风险 | 高危 | |
| 应用防御 | 应用完整性 | WebView组件忽略SSL证书 验证错误漏洞 | 低危 |
| 内部访问控制 | 证书明文存储风险 | 高危 | |
| 应用自身安全 | 敏感函数检测 | 中危 | |
| 应用安装升级 | 资源文件包含APK检测 | 低危 | |
| 安全审计 | 审计机制/审计存储/ 事件审计 | — | — |
| 审计访问控制 | 日志函数泄露风险 | 高危 |
| 脆弱性分类 | 脆弱点 | 测评方法 | 评估结果 |
|---|---|---|---|
| 边界防御 | 边界保护/用户账号 | 估算 | 中危 |
| 口令策略/鉴别机制 | 估算 | 高危 | |
| 网络通信 | 网络结构设计 | 估算 | 中危 |
| 网络设备安全配置 | 实测 | 低危 | |
| 网络安全/外部访问控制 | 实测合并 | 高危 | |
| 协议安全 | 实测 | 高危 | |
| 物理安全 | 外围接口安全/设备管理 | 估算 | 中危 |
| 设备保护 | 实测 | 中危 | |
| 系统防御 | 系统管理 | 实测合并 | 中危 |
| 资源共享/补丁安装 | 估算 | 高危 | |
| 访问控制 | 实测合并 | 中危 | |
| 系统配置 | 实测合并 | 低危 | |
| 系统软件安全/组件安全 | 实测合并 | 高危 | |
| 数据保护 | 数据完整性 | 估算 | 高危 |
| 密码保护/数据访问控制 | 实测合并 | 高危 | |
| 应用防御 | 应用完整性 | 实测 | 低危 |
| 内部访问控制 | 实测合并 | 高危 | |
| 应用自身安全/应用安装升级 | 实测合并 | 中危 | |
| 安全审计 | 审计机制/审计存储 | 估算 | 高危 |
| 审计访问控制 | 实测 | 高危 | |
| 审计日志 | 估算 | 中危 |
| [1] | ZHOU Min. Research on Personal Information Protection and Evaluation Model of Wearable Devices[D]. Nanjing: Southeast University, 2022. |
| 周敏. 可穿戴设备个人信息保护与评价模型研究[D]. 南京: 东南大学, 2022. | |
| [2] | NI Xueli, WANG Qun, LIANG Guangjun. Research on Security and Privacy Threats of Smart Wearable Devices[J]. Netinfo Security, 2022, 22(10): 98-107. |
| 倪雪莉, 王群, 梁广俊. 智能穿戴设备的安全与隐私威胁研究[J]. 信息网络安全, 2022, 22(10): 98-107. | |
| [3] | WU Jiacheng, YU Xiao. A Review of Research on Cybersecurity Risk Assessment Methods[J]. Electronic Science and Technology, 2024, 37(3): 10-17. |
| 吴嘉诚, 余晓. 网络安全风险评估方法研究综述[J]. 电子科技, 2024, 37(3):10-17. | |
| [4] | ZHANG Yan, LI Jiatong, SONG Xiaoyi, et al. Survey of IoT Device Security Detection[J]. Journal of Computer Research and Development, 2023, 60(10): 2271-2290. |
| 张妍, 黎家通, 宋小祎, 等. 物联网设备安全检测综述[J]. 计算机研究与发展, 2023, 60(10):2271-2290. | |
| [5] | WANG Jinfang, GUO Yuanbo. Network Security Risk Assessment of Cyber Physical System Based on Attack Graph[J]. Science Technology and Engineering, 2023, 23(28): 12175-12181. |
| 王金芳, 郭渊博. 基于攻击图的物理信息系统网络安全风险评估[J]. 科学技术与工程, 2023, 23(28):12175-12181. | |
| [6] | LIAO Xiaoqian, HUANG Zhenyong, JIN Mei, et al. Secure Backup and Recovery Methods and Systems for User Data in Wearable Smart Hardware: China, CN105760257A[P]. 2016-07-13. |
| 廖小谦, 黄真勇, 金梅, 等. 可穿戴智能硬件中用户数据的安全备份、恢复方法及系统:中国,CN105760257A[P]. 2016-07-13. | |
| [7] | ZHANG Huanguo. Information Security Engineer Course[M]. Beijing: Tsinghua University Press, 2016. |
| 张焕国. 信息安全工程师教程[M]. 北京: 清华大学出版社, 2016. | |
| [8] | GB/T 20278-2022 Information Security Technology-Security Technical Requirements and Testing Assessment Approaches for Network Vulnerability Scanners[S]. Beijing: Standards Press of China, 2022. |
| GB/T 20278-2022信息安全技术网络脆弱性扫描产品安全技术要求和测试评价方法[S]. 北京: 中国标准出版社, 2022. | |
| [9] | GB/T28448-2019 Information Security Technology-Evaluation Requirement for Classified Protection of Cybersecurity[S]. Beijing: Standards Press of China, 2019. |
| GB/T28448-2019信息安全技术网络安全等级保护测评要求[S]. 北京: 中国标准出版社, 2019. | |
| [10] | XINHUA News Agency. Data Security Law of the People’s Republic of China[N]. People’s Daily, 2021-06-19 (7). |
| 新华社. 中华人民共和国数据安全法[N]. 人民日报, 2021-06-19(7). | |
| [11] | LOI F, SIVANATHAN A, GHARAKHEILI H H, et al. Systematically Evaluating Security and Privacy for Consumer IoT Devices[C]// ACM. Proceedings of the 2017 Workshop on Internet of Things Security and Privacy. New York: ACM, 2017: 1-6. |
| [12] | GEORGE G, THAMPI S M. A Graph-Based Security Framework for Securing Industrial IoT Networks from Vulnerability Exploitations[J]. IEEE Access, 2018, 6: 43586-43601. |
| [13] | WANG Huan, CHEN Zhanfang, ZHAO Jianping, et al. A Vulnerability Assessment Method in Industrial Internet of Things Based on Attack Graph and Maximum Flow[J]. IEEE Access, 2018, 6: 8599-8609. |
| [14] | ZHAO Jian, WANG Rui, LI Zhengmin, et al. Security Threats and Risk Assessment of IoT System[J]. Journal of Beijing Uuiversity of Posts & Telecom, 2017, 40(s1): 135-139. |
| [15] | LIU Shengwa, GAO Xiang, WANG Min. Application of Attack Graph Method Based on Bayesian Network in Network Security Assessment[J]. Modern Electronics Technique, 2013, 36(9): 84-87. |
| 刘胜娃, 高翔, 王敏. 基于贝叶斯网络的攻击图方法在网络安全评估中的应用[J]. 现代电子技术, 2013, 36(9):84-87. | |
| [16] |
YANG Hongyu, YUAN Haihang, ZHANG Liang. Host Security Assessment Method Based on Attack Graph[J]. Journal on Communications, 2022, 43(2): 89-99.
doi: 10.11959/j.issn.1000-436x.2022030 |
|
杨宏宇, 袁海航, 张良. 基于攻击图的主机安全评估方法[J]. 通信学报, 2022, 43(2):89-99.
doi: 10.11959/j.issn.1000-436x.2022030 |
|
| [17] | YAN Jishan. Analysis on Network Security Risk Assessment Based on Attack Graph Behavior Pattern[J]. Microcontrollers & Embedded Systems, 2018, 18(10): 1-3. |
| 严纪珊. 基于攻击图行为模式分析的网络安全风险评估[J]. 单片机与嵌入式系统应用, 2018, 18(10):1-3. | |
| [18] | QIU Yue. Security Analysis for the Information of Wearable Devices[J]. Netinfo Security, 2016, 16(9): 79-83. |
| 裘玥. 智能可穿戴设备信息安全分析[J]. 信息网络安全, 2016, 16(9):79-83. | |
| [19] | SENEVIRATNE S, HU Yining, NGUYENET Tham, et al. A Survey of Wearable Devices and Challenges[J]. IEEE Communications Surveys & Tutorials, 2017, 19(4): 2573-2620. |
| [20] | TSENG T W, WU C T, LAI Feipei. Threat Analysis for Wearable Health Devices and Environment Monitoring Internet of Things Integration System[J]. IEEE Access, 2019, 7: 144983-144994. |
| [1] | YIN Jie, CHEN Pu, YANG Guinian, XIE Wenwei, LIANG Guangjun. Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence [J]. Netinfo Security, 2024, 24(11): 1615-1623. |
| [2] | LI Pengchao, ZHANG Quantao, HU Yuan. Smart Contract Vulnerability Detection Method Based on Graph Convolutional Network with Dual Attention Mechanism [J]. Netinfo Security, 2024, 24(11): 1624-1631. |
| [3] | CHEN Baogang, ZHANG Yi, YAN Song. Research on Multi-Factor Continuous Trustworthy Identity Authentication for Users in Civil Aviation Air Traffic Control Operational Information Systems [J]. Netinfo Security, 2024, 24(11): 1632-1642. |
| [4] | LAN Haoliang, WANG Qun, XU Jie, XUE Yishi, ZHANG Bo. Review of Research on Blockchain-Based Federated Learning [J]. Netinfo Security, 2024, 24(11): 1643-1654. |
| [5] | ZHANG Zhiqiang, BAO Yadong. Anomaly Traffic Detection Algorithm Integrating RF and CNN [J]. Netinfo Security, 2024, 24(11): 1655-1664. |
| [6] | XIA Lingling, MA Zhuo, GUO Xiangmin, NI Xueli. Target Personnel Importance Ranking Algorithm Based on Improved Weighted LeaderRank [J]. Netinfo Security, 2024, 24(11): 1665-1674. |
| [7] | HU Wentao, XU Jingkai, DING Weijie. Unsupervised Network Traffic Anomaly Detection Based on Abductive Learning [J]. Netinfo Security, 2024, 24(11): 1675-1684. |
| [8] | MA Zhuo, CHEN Dongzi, HE Jiahan, WANG Qun. Joint Prediction for User and Point of Interest Based on Disentangling Influences [J]. Netinfo Security, 2024, 24(11): 1685-1695. |
| [9] | ZHOU Shengli, XU Rui, CHEN Tinggui, JIANG Keyi. Research on the Evolution of Defrauded Network Behavior Risk Based on Eventic Graph [J]. Netinfo Security, 2024, 24(11): 1696-1709. |
| [10] | MA Rupo, WANG Qun, YIN Qiang, GAO Gugang. Analysis of Security Risks and Countermeasures for Modbus TCP Protocol [J]. Netinfo Security, 2024, 24(11): 1710-1720. |
| [11] | PEI Bingsen, LI Xin, FAN Zhijie, JIANG Zhangtao. Design and Implementation of a Cross-Domain Secure Sharing Transmission Control System for Video Surveillance Data [J]. Netinfo Security, 2024, 24(11): 1721-1730. |
| [12] | GU Haiyan, LIU Qi, MA Zhuo, ZHU Tao, QIAN Hanwei. Research on Data Noise Addition Method Based on Availability [J]. Netinfo Security, 2024, 24(11): 1731-1738. |
| [13] | ZHANG Peng, LUO Wenhua. Blockchain-Based Log Data Provenance Mechanism Using Bloom Filter Search Tree [J]. Netinfo Security, 2024, 24(11): 1739-1748. |
| [14] | LUAN Runsheng, JIANG Ping, SUN Yinxia, ZHANG Qinzhi. The Research and Development of Digital Forensics Technology [J]. Netinfo Security, 2024, 24(11): 1749-1762. |
| [15] | GAO Guangliang, LIANG Guangjun, HONG Lei, GAO Gugang, WANG Qun. Disambiguation-Based Partial Multi-Label Learning Algorithm Augmented by Fusing Instance and Label Correlations [J]. Netinfo Security, 2024, 24(11): 1763-1772. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||