Netinfo Security ›› 2024, Vol. 24 ›› Issue (11): 1721-1730.doi: 10.3969/j.issn.1671-1122.2024.11.011
Previous Articles Next Articles
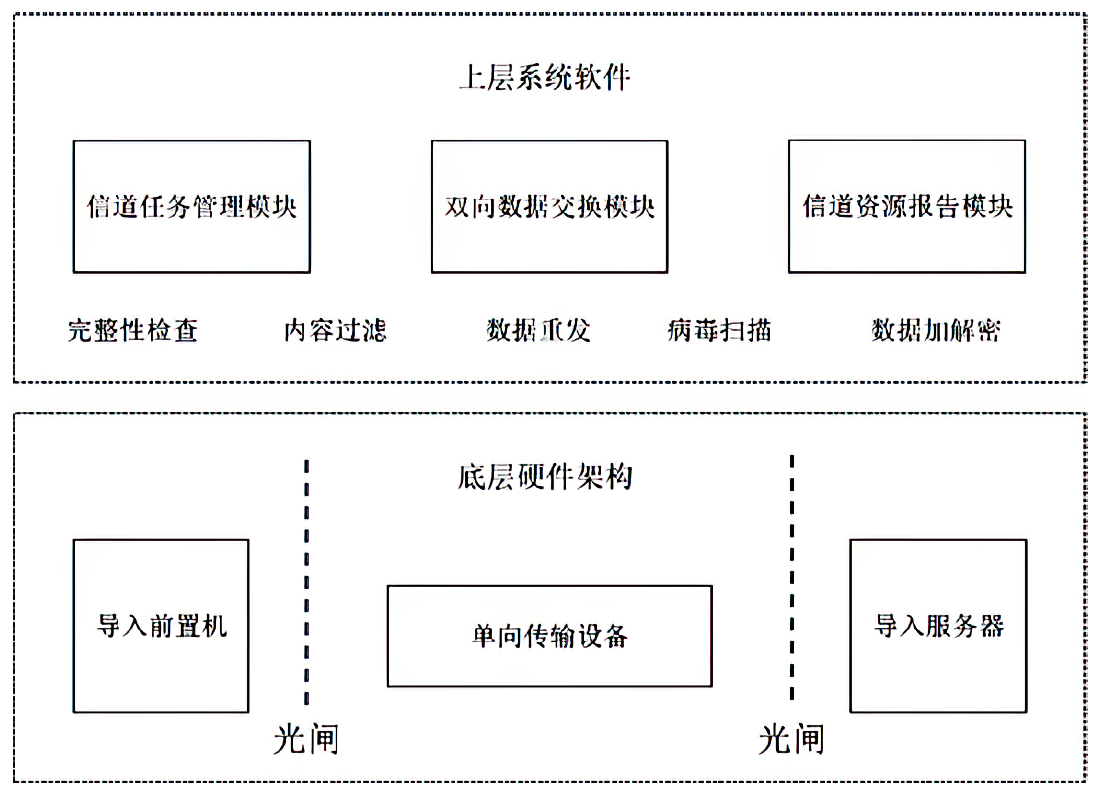
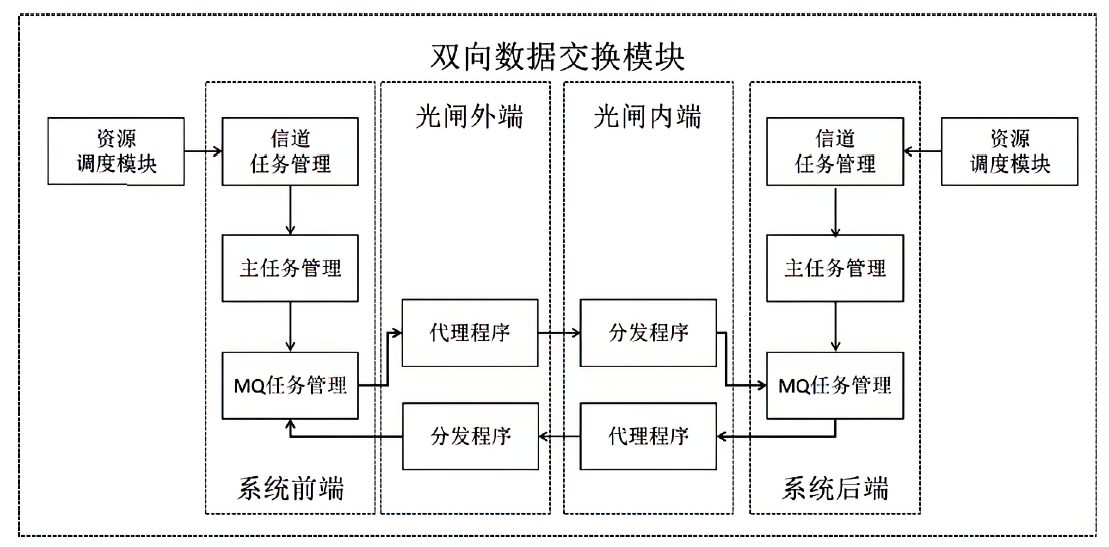
Design and Implementation of a Cross-Domain Secure Sharing Transmission Control System for Video Surveillance Data
PEI Bingsen1, LI Xin1( ), FAN Zhijie2, JIANG Zhangtao1
), FAN Zhijie2, JIANG Zhangtao1
- 1. Information Network Security Academy, People’s Public Security University of China, Beijing 100038, China
2. Information Security Technology Division, Third Research Institute of Ministry of Public Security, Shanghai 201204, China
-
Received:2024-06-17Online:2024-11-10Published:2024-11-21
CLC Number:
Cite this article
PEI Bingsen, LI Xin, FAN Zhijie, JIANG Zhangtao. Design and Implementation of a Cross-Domain Secure Sharing Transmission Control System for Video Surveillance Data[J]. Netinfo Security, 2024, 24(11): 1721-1730.
share this article
| [1] | MARKETSANDMARKETS. Video Surveillance Market by Offering, System, Vertical and Geography-Global Forecast to 2028[EB/OL]. (2023-08-26)[2024-05-26]. https://www.marketsandmarkets.com/Market-Reports/video-surveillance-market-645. |
| [2] | HUANG Shuhua, GUANG Kuan. Video Network Security Analysis and Countermeasure Research[J]. China Information Security, 2019(4): 32-34, 42. |
| 黄淑华, 广宽. 视频网络安全分析与对策研究[J]. 中国信息安全, 2019(4): 32-34, 42. | |
| [3] | COLLINS R T, LIPTON A J, KANADE T, et al. A System for Video Surveillance and Monitoring[J]. VSAM Final Report Carnegie Mellon University Technical Report, 2000, 59(5): 329-337. |
| [4] | KALBO N, MIRSKY Y, SHABTAI A, et al. The Security of Ip-Based Video Surveillance Systems[J]. Sensors, 2020, 20(17): 4806-4815. |
| [5] | LI Chao, HAN Xiang, LIU Zhao, et al. Cross-Network Data Security Exchange Technology Based on Trusted Computing[J]. Computer Engineering and Design, 2021, 42 (10): 2762-2769. |
| 李超, 韩翔, 刘钊, 等. 基于可信计算的跨网数据安全交换技术[J]. 计算机工程与设计, 2021, 42 (10): 2762-2769. | |
| [6] | FU Wenbo. Mass Internet of Things Data Security Exchange Model Under Heterogeneous Environment[J]. International Journal of Embedded Systems, 2020, 12(4): 484-490. |
| [7] | YANG Ming. One-Way Information Transmission System Based on Two-Dimensional Bar Code and Image Processing[D]. Shanghai: Shanghai Jiaotong University, 2013. |
| 杨明. 基于二维条码和图像处理的单向信息传输系统[D]. 上海: 上海交通大学, 2013. | |
| [8] | BAO Yimin. Research and Implementation of One-Way Secure Transmission System Based on Optical Gate[D]. Hangzhou: Zhejiang University of Technology, 2011. |
| 包益民. 基于光闸单向安全传输系统的研究与实现[D]. 杭州: 浙江工业大学, 2011. | |
| [9] | ZHANG Xinqi. One-Way Light Gate Principle and Function Analysis[J]. Network Security Technology & Application, 2016(5):99-100. |
| 张欣琦. 单向光闸原理及功能浅析[J]. 网络安全技术与应用, 2016(5):99-100. | |
| [10] | WANG Wenyan, LI Cheng, YU Huagang. Research on Information Controlled Exchange System Between Air Pipeline Networks[J]. Communications Technology, 2019, 52 (8): 2003-2007. |
| 王文琰, 李成, 禹华钢. 空管网间信息受控交换系统研究[J]. 通信技术, 2019, 52 (8): 2003-2007. | |
| [11] | LUO Huiyong. Application of Network Security Isolation Based on Cloud Desktop[J]. Computer Applications and Software, 2020, 37 (2): 15-17, 38. |
| 骆慧勇. 基于云桌面实现网络安全隔离的应用[J]. 计算机应用与软件, 2020, 37 (2): 15-17, 38. | |
| [12] | ZHANG Wuquan, HU Fei. Exploration of Indepth Protection of Network Security Based on Host Micro-Isolation Technology[J]. Financial Computer of China, 2023(2): 85-87. |
| 张伍全, 扈飞. 基于主机微隔离技术的网络安全纵深防护探索[J]. 中国金融电脑, 2023(2): 85-87. | |
| [13] | LYU Bo. Research on Network Security Defense System Based on Remote Browser Isolation[J]. Modern Information Technology, 2022, 6(7): 133-136. |
| 吕波. 基于远程浏览器隔离的网络安全防御系统研究[J]. 现代信息科技, 2022, 6(7): 133-136. | |
| [14] | HE Xinzhou. Research on Computer Network Security Based on Firewall Technology[J]. Journal of Physics: Conference Series, 2021(4): 2037-2046. |
| [15] | YANG Heng, ZHANG Yan, JIANG Yi, et al. Design of Secret Network Data Transmission System Based on Two-Dimensional Code[J]. Computing Technology and Automation, 2020, 39(3): 183-188. |
| 阳恒, 张岩, 蒋怡, 等. 基于二维码的涉密网络数据传输系统设计[J]. 计算技术与自动化, 2020, 39 (3): 183-188. | |
| [16] | YUAN Deyu, HUANG Shuhua, GAO Jian, et al. Research on the Security Status and Countermeasures of Video Surveillance Network Based on Scanning Analysis[J]. Science and Technology Management Research, 2021, 41 (4): 198-204. |
| 袁得嵛, 黄淑华, 高见, 等. 基于扫描分析的视频监控网络安全现状及对策研究[J]. 科技管理研究, 2021, 41(4): 198-204. | |
| [17] | WANG Jingfeng. Design and Implementation of Transmission Control System Based on One-Way Light Gate[D]. Beijing: Northern Polytechnic University, 2016. |
| 王精丰. 基于单向光闸的传输控制系统的设计与实现[D]. 北京: 北方工业大学, 2016. | |
| [18] | FAN Zhijie, HU Zhengliang, XIONG Yixing, et al. Design and Implementation of Data Security Transmission Control System Based on One-Way Light[J]. Computer Measurement & Control, 2021, 29(2): 103-107, 115. |
| 樊志杰, 胡正梁, 熊已兴, 等. 基于单向光的数据安全传输控制系统的设计与实现[J]. 计算机测量与控制, 2021, 29(2): 103-107, 115. | |
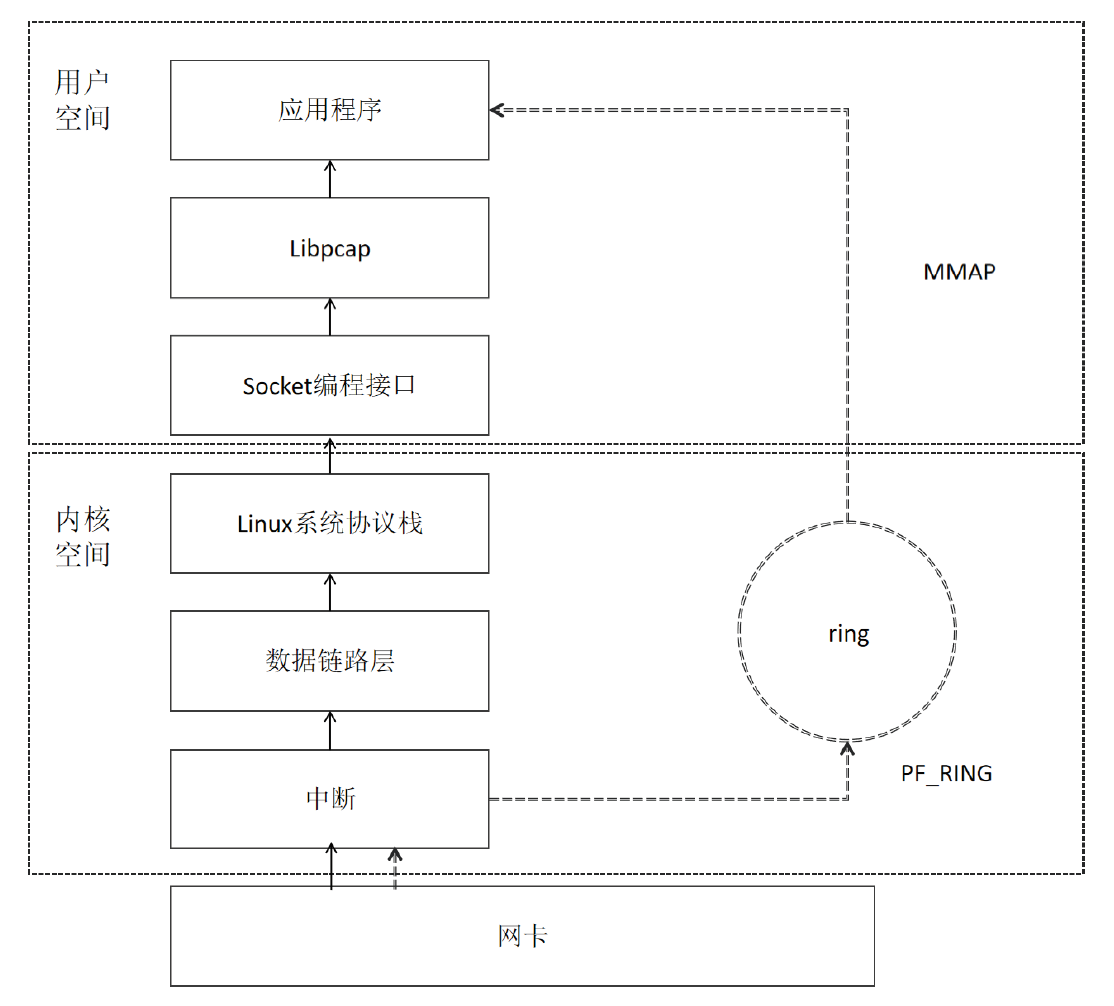
| [19] | LI Xin, FAN Zhijie, CAO Zhiwei, et al. High-Performance Transmission Model of Multi-Core Video Stream Based on PF_RING[J]. Journal of Beijing University of Aeronautics and Astronautics, 2020, 46(9): 1670-1676. |
| 李欣, 樊志杰, 曹志威, 等. 基于PF_RING的多核视频流高性能传输模型[J]. 北京航空航天大学学报, 2020, 46 (9): 1670-1676. | |
| [20] | WU Kehe, WANG Dongdong. High-Speed Network Data Capture Method Based on PF_RING[J]. Computer & Digital Engineering, 2019, 47 (3): 598-604. |
| 吴克河, 王冬冬. 基于PF_RING的高速网络数据捕获方法[J]. 计算机与数字工程, 2019, 47 (3): 598-604. |
| [1] | YIN Jie, CHEN Pu, YANG Guinian, XIE Wenwei, LIANG Guangjun. Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence [J]. Netinfo Security, 2024, 24(11): 1615-1623. |
| [2] | LI Pengchao, ZHANG Quantao, HU Yuan. Smart Contract Vulnerability Detection Method Based on Graph Convolutional Network with Dual Attention Mechanism [J]. Netinfo Security, 2024, 24(11): 1624-1631. |
| [3] | CHEN Baogang, ZHANG Yi, YAN Song. Research on Multi-Factor Continuous Trustworthy Identity Authentication for Users in Civil Aviation Air Traffic Control Operational Information Systems [J]. Netinfo Security, 2024, 24(11): 1632-1642. |
| [4] | LAN Haoliang, WANG Qun, XU Jie, XUE Yishi, ZHANG Bo. Review of Research on Blockchain-Based Federated Learning [J]. Netinfo Security, 2024, 24(11): 1643-1654. |
| [5] | ZHANG Zhiqiang, BAO Yadong. Anomaly Traffic Detection Algorithm Integrating RF and CNN [J]. Netinfo Security, 2024, 24(11): 1655-1664. |
| [6] | XIA Lingling, MA Zhuo, GUO Xiangmin, NI Xueli. Target Personnel Importance Ranking Algorithm Based on Improved Weighted LeaderRank [J]. Netinfo Security, 2024, 24(11): 1665-1674. |
| [7] | HU Wentao, XU Jingkai, DING Weijie. Unsupervised Network Traffic Anomaly Detection Based on Abductive Learning [J]. Netinfo Security, 2024, 24(11): 1675-1684. |
| [8] | MA Zhuo, CHEN Dongzi, HE Jiahan, WANG Qun. Joint Prediction for User and Point of Interest Based on Disentangling Influences [J]. Netinfo Security, 2024, 24(11): 1685-1695. |
| [9] | ZHOU Shengli, XU Rui, CHEN Tinggui, JIANG Keyi. Research on the Evolution of Defrauded Network Behavior Risk Based on Eventic Graph [J]. Netinfo Security, 2024, 24(11): 1696-1709. |
| [10] | MA Rupo, WANG Qun, YIN Qiang, GAO Gugang. Analysis of Security Risks and Countermeasures for Modbus TCP Protocol [J]. Netinfo Security, 2024, 24(11): 1710-1720. |
| [11] | GU Haiyan, LIU Qi, MA Zhuo, ZHU Tao, QIAN Hanwei. Research on Data Noise Addition Method Based on Availability [J]. Netinfo Security, 2024, 24(11): 1731-1738. |
| [12] | ZHANG Peng, LUO Wenhua. Blockchain-Based Log Data Provenance Mechanism Using Bloom Filter Search Tree [J]. Netinfo Security, 2024, 24(11): 1739-1748. |
| [13] | LUAN Runsheng, JIANG Ping, SUN Yinxia, ZHANG Qinzhi. The Research and Development of Digital Forensics Technology [J]. Netinfo Security, 2024, 24(11): 1749-1762. |
| [14] | GAO Guangliang, LIANG Guangjun, HONG Lei, GAO Gugang, WANG Qun. Disambiguation-Based Partial Multi-Label Learning Algorithm Augmented by Fusing Instance and Label Correlations [J]. Netinfo Security, 2024, 24(11): 1763-1772. |
| [15] | QIN Zhenkai, XU Mingchao, JIANG Ping. Research on the Construction Method and Application of Case Knowledge Graph Based on Prompt Learning [J]. Netinfo Security, 2024, 24(11): 1773-1782. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||