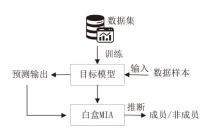
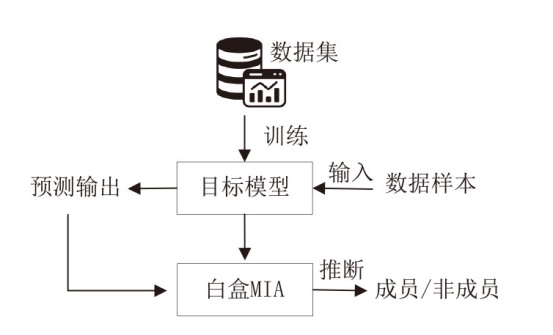
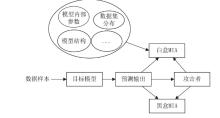
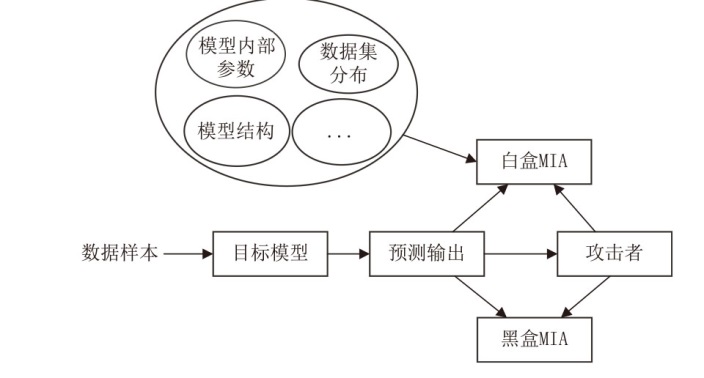
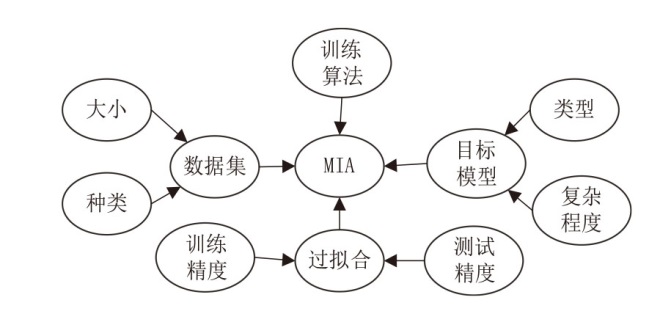
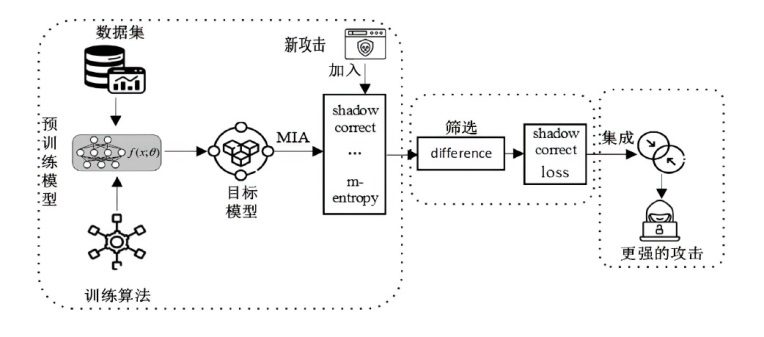
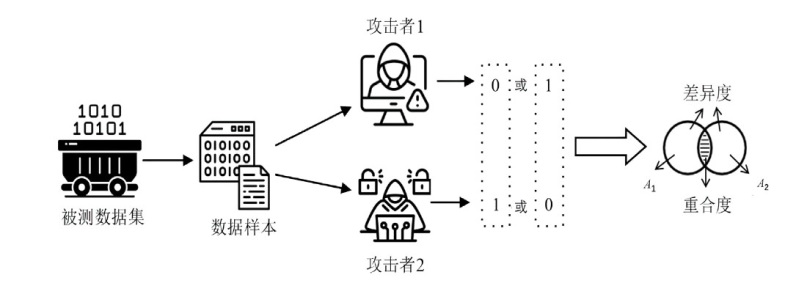
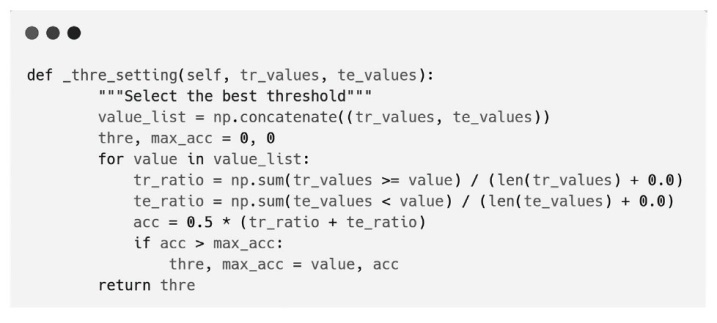
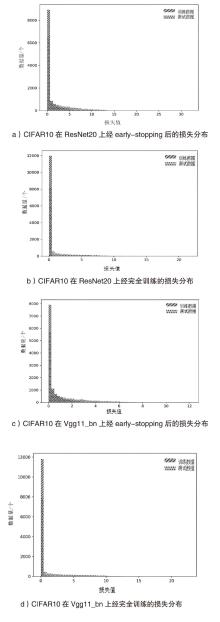
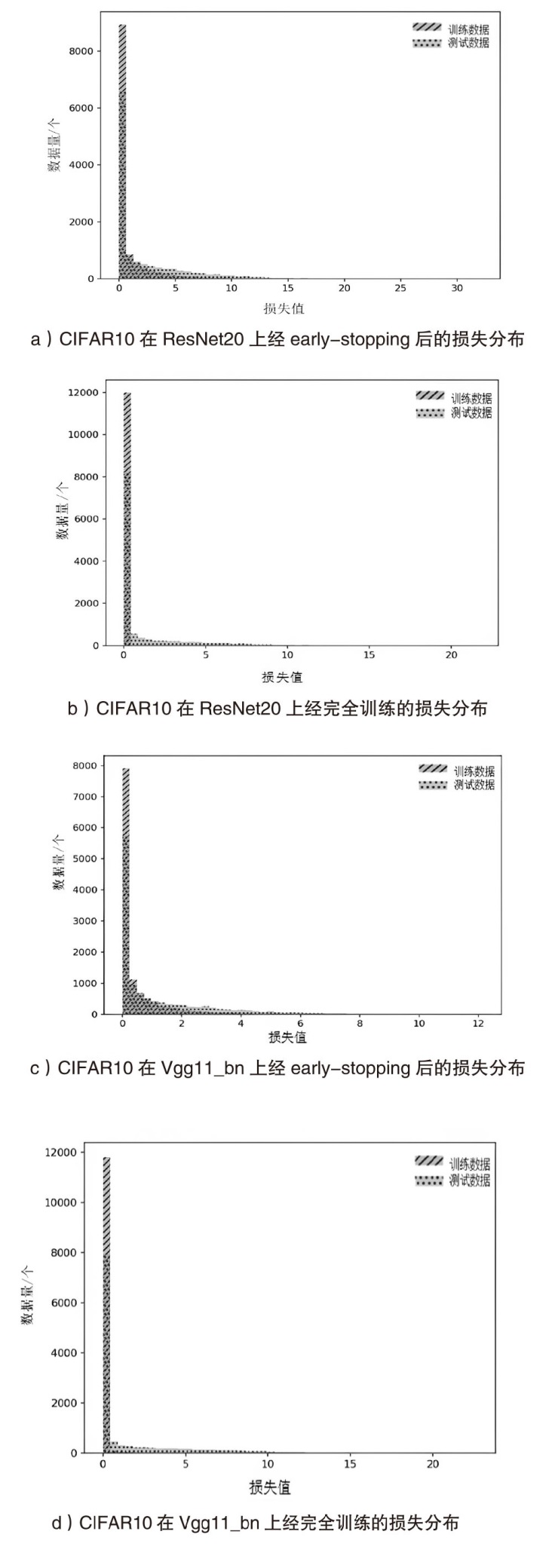
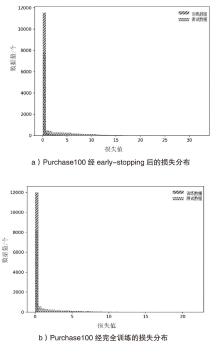
Netinfo Security ›› 2024, Vol. 24 ›› Issue (8): 1252-1264.doi: 10.3969/j.issn.1671-1122.2024.08.011
Previous Articles Next Articles
Membership Inference Attacks Method Based on Ensemble Learning
ZHAO Wei, REN Xiaoning, XUE Yinxing( )
)
- School of Computer Science and Technology, University of Science and Technology of China, Hefei 230027, China
-
Received:2023-11-07Online:2024-08-10Published:2024-08-22
CLC Number:
Cite this article
ZHAO Wei, REN Xiaoning, XUE Yinxing. Membership Inference Attacks Method Based on Ensemble Learning[J]. Netinfo Security, 2024, 24(8): 1252-1264.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.08.011
| 数据集 模型 | CIFAR10 (ResNet20) | CIFAR10 (Vgg11_bn) | CIFAR100 (ResNet20) | CIFAR100 (Vgg11_bn) | Texas 100 | Purchase 100 |
|---|---|---|---|---|---|---|
| train_acc | 100% | 100% | 100% | 100% | 99.80% | 100% |
| test_acc | 72.30% | 74.20% | 34.30% | 42.50% | 50.70% | 88.70% |
| gap | 27.70% | 25.80% | 65.70% | 57.50% | 49.10% | 11.30% |
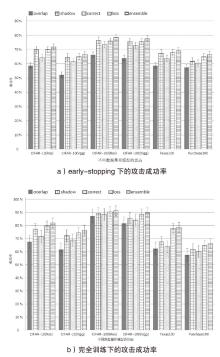
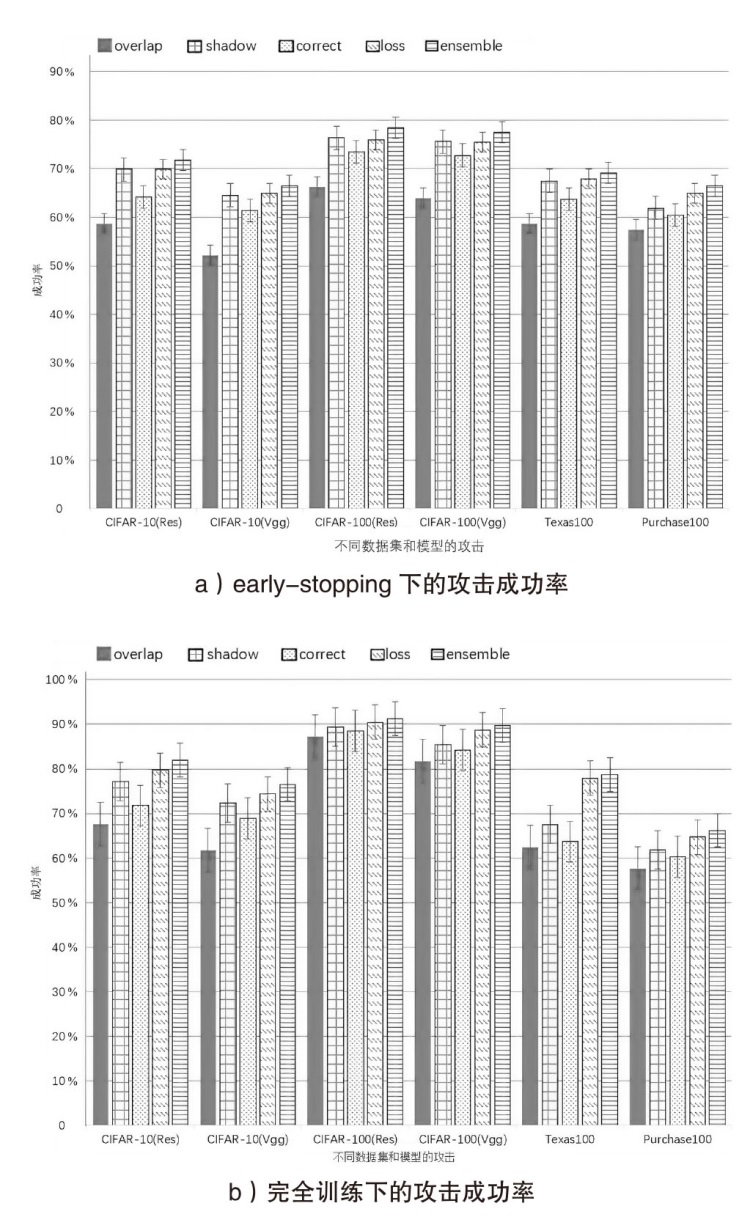
| shadow attack | 77.11% | 72.34% | 89.45% | 85.38% | 67.46% | 61.85% |
| correctness | 71.78% | 68.93% | 88.56% | 84.22% | 63.68% | 60.30% |
| m-entropy | 79.80% | 74.19% | 90.50% | 88.74% | 77.62% | 63.41% |
| entropy | 78.83% | 73.47% | 88.93% | 87.75% | 70.75% | 63.38% |
| loss | 79.72% | 74.35% | 90.44% | 88.74% | 77.92% | 64.77% |
| confidence | 79.61% | 74.42% | 90.48% | 88.57% | 77.46% | 63.35% |
| 数据集 模型 | CIFAR10 (ResNet20) | CIFAR10 (Vgg11_bn) | CIFAR100 (ResNet20) | CIFAR100 (Vgg11_bn) | Texas 100 | Purchase 100 |
|---|---|---|---|---|---|---|
| epoch | 10.00% | 20.00% | 20.00% | 15.00% | 15.00% | 10.00% |
| train_acc | 81.30% | 83.20% | 64.70% | 69.60% | 67.40% | 84.50% |
| test_acc | 59.70% | 66.10% | 24.80% | 32.70% | 32.40% | 72.90% |
| gap | 21.60% | 17.10% | 39.90% | 36.90% | 35.00% | 11.60% |
| shadow attack | 69.87% | 64.55% | 76.37% | 75.63% | 67.46% | 61.88% |
| correctness | 64.23% | 61.37% | 73.52% | 72.78% | 63.68% | 60.41% |
| loss | 69.96% | 65.02% | 75.98% | 75.54% | 67.92% | 65.02% |
| 攻击差异度 | CIFAR10(ResNet20) | CIFAR10(Vgg11_bn) | CIFAR100(ResNet20) | |||
|---|---|---|---|---|---|---|
| 完全 训练 | early-stopping | 完全 训练 | early- stopping | 完全 训练 | early-stopping | |
| (C, S) | 8.99% | 8.64% | 7.19% | 5.86% | 2.33% | 6.37% |
| (C, L) | 11.92% | 8.81% | 8.94% | 6.15% | 3.46% | 5.58% |
| (S, L) | 5.97% | 0.09% | 5.77% | 2.75% | 2.05% | 3.53% |
| (L, P) | 0.07% | 0.06% | 0.05% | 0.05% | 0.03% | 0.04% |
| 攻击差异度 | CIFAR100 (Vgg11_bn) | Texas100 | Purchase100 | |||
| (C, S) | 2.62% | 5.87% | 4.96% | 5.96% | 3.65% | 3.67% |
| (C, L) | 6.06% | 5.98% | 15.62% | 6.32% | 6.85% | 6.83% |
| (S, L) | 4.78% | 3.47% | 11.88% | 2.44% | 6.14% | 5.52% |
| (L, P) | 0.01% | 0.01% | 0.03% | 0.03% | 0.02% | 0.01% |
| 数据集 模型 | CIFAR10 (ResNet20) | CIFAR10 (Vgg11_bn) | CIFAR100 (ResNet20) | CIFAR100 (Vgg11_bn) | Texas 100 | Purchase 100 |
|---|---|---|---|---|---|---|
| shadow attack | 99.74% | 99.72% | 100% | 99.98% | 98.45% | 96.01% |
| correctness | 99.35% | 98.89% | 99.99% | 100% | 97.86% | 95.67% |
| loss | 99.82% | 99.84% | 99.96% | 99.98% | 99.04% | 98.89% |
| m-entropy | 99.86% | 99.84% | 99.97% | 99.98% | 99.11% | 99.02% |
| confidence | 99.85% | 99.82% | 99.99% | 99.96% | 99.13% | 98.99% |
| ensemble | 99.89% | 99.92% | 100% | 100% | 99.21% | 99.10% |
| [1] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2016: 770-778. |
| [2] | DEVLIN J, CHANG Mingwei, KENTON L, et al. BERT: Pre-Training of Deep Bidirectional Transformers for Language Understanding[EB/OL]. (2018-10-11)[2023-11-02]. https://arxiv.org/abs/1810.04805. |
| [3] | LIANG Xiao, WAN Xiaoyue, LU Xiaozhen, et al. IoT Security Techniques Based on Machine Learning: How do IoT Devices Use AI to Enhance Security?[J]. IEEE Signal Processing Magazine, 2018, 35 (5): 41-49. |
| [4] | CARLINI N, LIU Chang, ERLINGSSON U, et al. The Secret Sharer: Evaluating and Testing Unintended Memorization in Neural Networks[C]// USENIX. 28th USENIX Security Symposium (USENIX Security 19). Berkeley: USENIX, 2019: 267-284. |
| [5] | SONG Congzheng, RISTENPART T, SHMATIKOV V. Machine Learning Models that Remember Too Much[C]// ACM. The 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 587-601. |
| [6] | FREDRIKSON M, JHA S, RISTENPART T. Model Inversion Attacks that Exploit Confidence Information and Basic Countermeasures[C]// ACM. Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2015: 1322-1333. |
| [7] | GANJU K, WANG Qi, YANG Wei, et al. Property Inference Attacks on Fully Connected Neural Networks Using Permutation Invariant Representations[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 619-633. |
| [8] | TRAMÈR F, ZHANG Fan, JUELS A, et al. Stealing Machine Learning Models via Prediction APIs[C]// USENIX. 25th USENIX Security Symposium (USENIX Security 16). Berkeley: USENIX, 2016: 601-618. |
| [9] | SHOKRI R, STRONATI M, SONG Congzheng, et al. Membership Inference Attacks Against Machine Learning Models[C]// IEEE. 2017 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2017: 3-18. |
| [10] | SALEM A, ZHANG Yang, HUMBERT M, et al. ML-Leaks: Model and Data Independent Membership Inference Attacks and Defenses on Machine Learning Models[C]// Internet Society. Proceedings 2019 Network and Distributed System Security Symposium. New York: Internet Society, 2019: 1-15. |
| [11] | YEOM S, GIACOMELLI I, FREDRIKSON M, et al. Privacy Risk in Machine Learning: Analyzing the Connection to Overfitting[C]// IEEE. 31st Computer Security Foundations Symposium. New York: IEEE, 2018: 268-282. |
| [12] | NASR M, SHOKRI R, HOUMANSADR A. Comprehensive Privacy Analysis of Deep Learning: Passive and Active White-Box Inference Attacks against Centralized and Federated Learning[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 739-753. |
| [13] | JIA Jinyuan, SALEM A, BACKES M, et al. MemGuard: Defending against Black-Box Membership Inference Attacks via Adversarial Examples[C]// ACM. Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 259-274. |
| [14] | SONG Liwei, MITTAL P. Systematic Evaluation of Privacy Risks of Machine Learning Models[C]// USENIX. 30th USENIX Security Symposium (USENIX Security 21). Berkeley: USENIX, 2021: 2615-2632. |
| [15] | LONG Yunhui, BINDSCHAEDLER V, WANG Lei, et al. Understanding Membership Inferences on Well-Generalized Learning Models[EB/OL]. (2018-02-13)[2023-11-02]. https://arxiv.org/pdf/1802.04889.pdf. |
| [16] | SHOKRI R, STROBEL M, ZICK Y. On the Privacy Risks of Model Explanations[C]// ACM. The 2021 AAAI/ACM Conference on AI, Ethics, and Society. New York: ACM, 2021: 231-241. |
| [17] | TRUEX S, LIU Ling, GURSOY M E, et al. Demystifying Membership Inference Attacks in Machine Learning as a Service[C]// IEEE. IEEE Transactions on Services Computing. New York: IEEE, 2021: 2073-2089. |
| [18] | CHEN Junjie, WANG W H, SHI Xinghua. Differential Privacy Protection against Membership Inference Attack on Machine Learning for Genomic Data[C]// World Scientific. Proceedings of the Pacific Symposium (Biocomputing 2021). Singapore: World Scientific, 2020: 26-37. |
| [19] | CHEN Dingfan, YU Ning, ZHANG Yang, et al. GAN-Leaks: A Taxonomy of Membership Inference Attacks against Generative Models[C]// ACM. Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2020: 343-362. |
| [20] | LEINO K, FREDRIKSON M. Stolen Memories: Leveraging Model Memorization for Calibrated White-Box Membership Inference[C]// USENIX. 29th USENIX Security Symposium (USENIX Security 2020). Berkeley: USENIX, 2020: 1605-1622. |
| [21] | YEOM S, GIACOMELLI I, FREDRIKSON M, et al. Privacy Risk in Machine Learning: Analyzing the Connection to Overfitting[C]// IEEE. 2018 IEEE 31st Computer Security Foundations Symposium (CSF). New York: IEEE, 2018: 268-282. |
| [22] | BENTLEY J W, GIBNEY D, HOPPENWORTH G, et al. Quantifying Membership Inference Vulnerability via Generalization Gap and Other Model Metrics[EB/OL]. (2020-09-11)[2023-11-02]. https://arxiv.org/abs/2009.05669v1. |
| [23] | SONG Liwei, MITTAL P. Systematic Evaluation of Privacy Risks of Machine Learning Models[C]// USENIX. 30th USENIX Security Symposium (USENIX Security 21). Berkeley: USENIX, 2021: 2615-2632. |
| [24] | NASR M, SHOKRI R, HOUMANSADR A. Machine Learning with Membership Privacy Using Adversarial Regularization[C]// ACM. The 2018 ACM SIGSAC Conference on Computer and Communications Security (CCS). New York: ACM, 2021: 634-646. |
| [25] | ABADI M, CHU A, GOODFELLOW I, et al. Deep Learning with Differential Privacy[C]// ACM. The 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 308-318. |
| [26] | SHEJWALKAR V, HOUMANSADR A. Membership Privacy for Machine Learning Models through Knowledge Transfer[J]. Proceedings of the AAAI Conference on Artificial Intelligence, 2021, 35(11): 9549-9557. |
| [27] | HUI Bo, YANG Yuchen, YUAN Haolin, et al. Practical Blind Membership Inference Attack via Differential Comparisons[C]// Internet Society. Network and Distributed System Security (NDSS) Symposium 2021. New York: Internet Society, 2021: 1-17. |
| [1] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning [J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| [2] | TU Xiaohan, ZHANG Chuanhao, LIU Mengran. Design and Implementation of Malicious Traffic Detection Model [J]. Netinfo Security, 2024, 24(4): 520-533. |
| [3] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [4] | XING Lingkai, ZHANG Jian. Research and Implementation on Abnormal Behavior Detection Technology of Virtualization Platform Based on HPC [J]. Netinfo Security, 2023, 23(10): 64-69. |
| [5] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [6] | Zewen MA, Yang LIU, Hongping XU, Hang YI. DoS Traffic Identification Technology Based on Integrated Learning [J]. Netinfo Security, 2019, 19(9): 115-119. |
| [7] | Di XIAO, Ying WANG, Yanting CHANG, Jiaqi ZHOU. Reversible Data Hiding in Encrypted Image Based on Additive Homomorphism and Multi-level Difference Histogram Shifting [J]. Netinfo Security, 2016, 16(4): 9-16. |
| [8] | TANG Jian, SUN Chun-lai, LI Dong. Discussion about the Industrial Control Network Intrusion Prevention Technology based on On-line Ensemble Learning [J]. 信息网络安全, 2014, 14(9): 86-91. |
| [9] | . NULL [J]. , 2012, 12(12): 0-0. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||