Netinfo Security ›› 2019, Vol. 19 ›› Issue (9): 81-85.doi: 10.3969/j.issn.1671-1122.2019.09.017
• Orginal Article • Previous Articles Next Articles
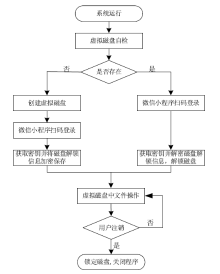
Design and Implementation of File Encryption System Based on Wechat Mini Program
Juru HAN1,2, Zhi YANG3, Zhaoxuan JI1,2, Cunqing MA2
- 1. State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100195, China
2. School of Cyber Security, University of Chinese Academy of Sciences, Beijing 100195,China
3. Beijing Trusted Huatai Information Technology Co., Ltd, Beijing 100195, China
-
Received:2019-07-15Online:2019-09-10Published:2020-05-11
CLC Number:
Cite this article
Juru HAN, Zhi YANG, Zhaoxuan JI, Cunqing MA. Design and Implementation of File Encryption System Based on Wechat Mini Program[J]. Netinfo Security, 2019, 19(9): 81-85.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.09.017
| [1] | WU Sujuan.The Research and Application of Data Encryption Technology in Computer Network Security[J]. Computer Knowledge and Technology, 2014, 10(36): 8633-8634. |
| 吴苏娟. 计算机网络安全中数据加密技术的应用研究[J].电脑知识与技术,2014,10(36): 8633-8634. | |
| [2] | HOU Fangyong.Research on Key Techniques of Memory System Data Confidentiality and Integrity Protection[D]. Changsha: School of Computer National University of Defense Technology, 2015. |
| 侯方勇. 存储系统数据机密性与完整性保护的关键技术研究[D].长沙:国防科学技术大学,2015. | |
| [3] | CHEN Shangyi.Transparent File Encryption Technology and Its Application[J]. Information Security and Communications Privacy, 2007, 7(11): 75-77. |
| 陈尚义. 透明文件加解密技术及其应用[J].信息安全与通信保密,2007,7(11): 75-77. | |
| [4] | HU Hongyin, HE Chengwan.Design of Multiple Security Level Supported File Encryption Tool[J]. Computer Engineering and Design, 2011, 32(8): 2569-2571. |
| 胡宏银,何成万.支持多种安全级别的文件加密工具设计[J].计算机工程与设计,2011,32(8): 2569-2571. | |
| [5] | CHENG Guoyong.Design and Application of Trusted Encryption Disk[D]. Beijing: Beijing University of Technology, 2013. |
| 成国永. 可信加密磁盘的设计与应用[D].北京:北京工业大学,2013. | |
| [6] | SHEN Shanchao.Design and Realization of Disk Encrypt System[D]. Changchun: Jilin University, 2011. |
| 沈善超. 整盘加密系统的设计与实现[D].长春:吉林大学,2011. | |
| [7] | SHAHBAZI M. Mobile Data Security System and Methods: U.S. Patent 8,495,700[P].2013-7-23. |
| [8] | ZHANG Xin, FENG Quanyuan.Dynamic ID-based remote user authentication scheme[J]. Computer Engineering and Design, 2007, 28(3): 545-546. |
| 张馨,冯全源.基于动态ID的远程用户身份认证方案[J].计算机工程与设计,2007,28(3):545-546. | |
| [9] | XIONG Jun.Application of User Identity Authentication Technology in Computer in Information Security[J]. Information Security and Technology, 2013, 4(6): 33-36. |
| 熊俊. 用户身份认证技术在计算机信息安全中的应用[J].信息安全与技术, 2013,4(6): 33-36. | |
| [10] | ZHANG Hong, CHEN Zhigang.Design and Analysis of a New One-time Password Authentication Scheme[J]. Computer Engineering, 2004, 30(17): 112-113. |
| 张宏,陈志刚.一种新型一次性口令身份认证方案的设计与分析[J].计算机工程,2004,30(17):112-113. | |
| [11] | LI Qingjun, GAN Meng.File Encryption Approach Based on Virtual Disk[J]. Computer Engineering and Design, 2006, 27(15): 2835-2838. |
| 李清俊,甘萌.基于虚拟磁盘的文件加密方法[J].计算机工程与设计,2006, 27(15):2835-2838. | |
| [12] | NI Kaibin, YAO Guoxiang, GUAN Quanlong.Security Enhanced Virtual Disk Encryption System and Technology[J]. Journal of Computer Applications, 2009, 29(11): 2987-2989. |
| 倪凯斌,姚国祥,官全龙.安全增强型虚拟磁盘加密系统技术[J].计算机应用,2009, 29(11):2987-2989. | |
| [13] | KORNBLUM J D.Implementing Bitlocker Drive Encryption for Forensic Analysis[J]. Digital Investigation, 2009, 5(3-4): 75-84. |
| [14] | SUBAIR P S, BALAN C, DIJA S, et al. Forensic Decryption of FAT BitLocker Volumes[EB/OL]. , 2018-5-15. |
| [15] | TAO Tianyi.Research and Implementation of Self-Securing Disk Encrypted System Based on TrueCrypt[D]. Beijing: Beijing University of Posts and Telecommunications, 2013. |
| 陶天一. 基于TrueCrypt的自安全磁盘加密系统的研究与实现[D].北京:北京邮电大学,2013. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||