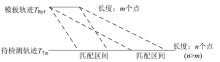
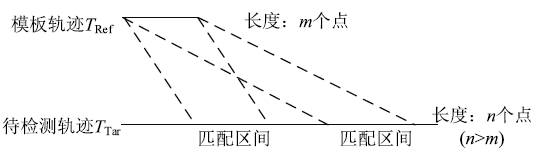
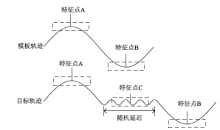
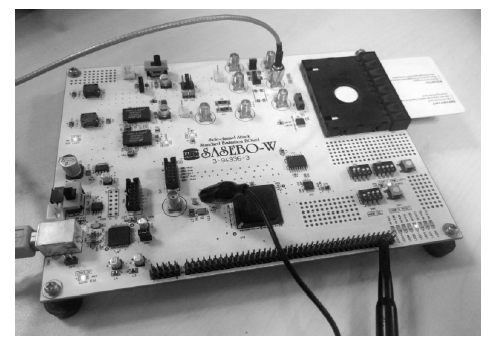
| [1] |
KOCHER P C.Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems[C]//Springer. 1996 Annual International Cryptology Conference, August 18-22, 1996, Santa Barbara, CA, USA. Heidelberg: Springer, 1996: 104-113.
|
| [2] |
KOCHER P, JAFFE J, JUN B.Differential Power Analysis[C]//Springer. 1999 Annual International Cryptology Conference, August 15-19, 1999, Santa Barbara, CA, USA. Heidelberg: Springer, 1999: 388-397.
|
| [3] |
MENG Qingquan, YANG Xiaoyuan, ZHONG Weidong, et al.Implementation and Optimization of S-box Resisting DPA Attacks Based on Secret Sharing[J]. Netinfo Security, 2018, 18(2): 71-77.
|
|
孟庆全,杨晓元,钟卫东,等.抵抗差分功耗攻击的秘密共享S盒实现与优化[J].信息网络安全,2018,18(2):71-77.
|
| [4] |
QUISQUATER J J, SAMYDE D. Electromagnetic Analysis(EMA): Measures and Counter-measures for Smart Cards[C]//Springer. 2001 International Conference on Research in Smart Cards, September 19-21, 2001, Cannes, France. Heidelberg: Springer, 2001: 200-210.
|
| [5] |
BONEH D, DEMILLO R A, LIPTON R J.On the Importance of Checking Cryptographic Protocols for Faults[C]//Springer. 1997 International Conference on the Theory and Applications of Cryptographic Techniques, May 11-15, 1997, Konstanz, Germany. Heidelberg: Springer, 1997: 37-51.
|
| [6] |
PIRET G, QUISQUATER J J.A Differential Fault Attack Technique Against SPN Structures, with Application to the AES and KHAZAD[C]//Springer. 2003 International Workshop on Cryptographic Hardware and Embedded Systems, September 8-10, 2003, Cologne, Germany. Heidelberg: Springer, 2003: 77-88.
|
| [7] |
RIVAIN M, PROUFF E.Provably Secure Higher-order Masking of AES[C]//Springer. 2010 International Workshop on Cryptographic Hardware and Embedded Systems, August 17-20, Santa Barbara, CA, USA. Heidelberg: Springer, 2010: 413-427.
|
| [8] |
CNUDDE D T, REPARAZ O, BILGIN B, et al.Masking AES with d+1 Shares in Hardware[C]//Springer. 2016 International Conference on Cryptographic Hardware and Embedded Systems, August 17-19, Santa Barbara, USA. Heidelberg: Springer, 2016: 194-212.
|
| [9] |
TUNSTALL M, BENOIT O.Efficient Use of Random Delays in Embedded Software[C]//Springer. 2007 IFIP International Workshop on Information Security Theory and Practices, May 9-11, Heraklion, Crete, Greece. Heidelberg: Springer, 2007: 27-38.
|
| [10] |
VAN WOUDENBERG J G J, WITTEMAN M, BAKKER B. Improving Differential Power Analysis by Elastic Alignment[C]//ACM. 11th International Conference on Topics in Cryptology, February 14-18, 2011, San Francisco, CA, USA. New York: ACM, 2011: 104-119.
|
| [11] |
PAAR C.When Reverse-engineering Meets Side-channel Analysis-digital Lockpicking in Practice[C]//Springer. 2013 International Conference on Selected Areas in Cryptography, August 14-16, 2013, Burnaby, BC, Canada. Heidelberg: Springer, 2013, 571-588.
|
| [12] |
ABOULKASSIMI D, AGOYAN M, FREUND L, et al. ElectroMagnetic Analysis(EMA) of Software AES on Java Mobile Phones[EB/OL]. , 2018-11-21.
|
| [13] |
NAKANO Y, SOUISSI Y, NGUYEN R, et al.A Pre-processing Composition for Secret Key Recovery on Android Smartphone[C]//Springer. 2014 IFIP International Workshop on Information Security Theory and Practice, June 30-July 2, 2014, Heraklion, Crete, Greece. Heidelberg: Springer, 2014: 76-91.
|
| [14] |
O’FLYNN C, CHEN Z. Power Analysis Attacks Against IEEE 802.15. 4 Nodes[C]//Springer. 2016 International Workshop on Constructive Side-Channel Analysis and Secure Design, April 14-15, 2016, Graz, Austria. Heidelberg: Springer, 2016: 55-70.
|
| [15] |
MÜLLER M. Dynamic Time Warping[EB/OL].1007%2F978-3-540-74048-3_4, 2018-11-21.
|
| [16] |
MUIJRERS R A,VAN WOUDENBERG J G J,BATINA L.RAM: Rapid Alignment Method[C]//ACM. 10th IFIP WG 8.8/11.2 international conference on Smart Card Research and Advanced Applications, September 14-16, 2011, Leuven, Belgium. New York: ACM, 2011: 266-282.
|
| [17] |
WANG Qing, TU Chenyang, SHEN Jiahui.Design and Application of General Framework for Side Channel Attack[J]. Netinfo Security, 2017, 17(5): 57-62.
|
|
王庆,屠晨阳,沈嘉荟.侧信道攻击通用框架设计及应用[J].信息网络安全,2017,17(5):57-62.
|
| [18] |
PERNG C S, WANG H, ZHANG S R, et al.Landmarks: a New Model for Similarity-based Pattern Querying in Time Series Databases[C]//IEEE. 16th International Conference on Data Engineering, February 29-March 3, 2000, San Diego, CA, USA. New Jersey: IEEE, 2000: 33-42.
|