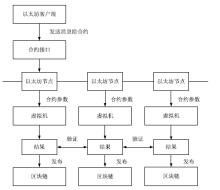
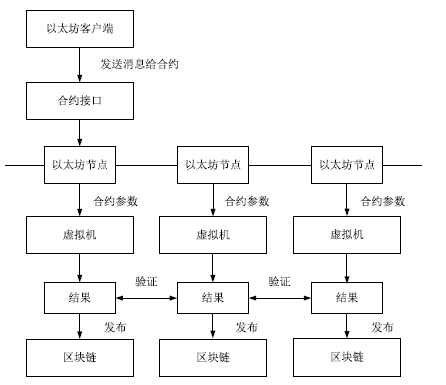
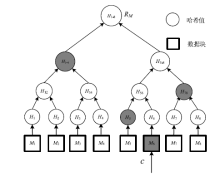
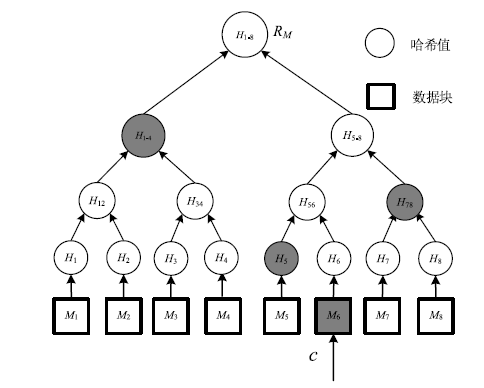
Netinfo Security ›› 2019, Vol. 19 ›› Issue (3): 52-60.doi: 10.3969/j.issn.1671-1122.2019.03.007
• Orginal Article • Previous Articles Next Articles
Blockchain-based Distributed Cloud Storage System with Public Verification
Yiming HEI, Jianwei LIU, Zongyang ZHANG( ), Hui YU
), Hui YU
- School of Cyber Science and Technology, Beihang University, Beijing 100191, China
-
Received:2018-12-12Online:2019-03-19Published:2020-05-11
CLC Number:
Cite this article
Yiming HEI, Jianwei LIU, Zongyang ZHANG, Hui YU. Blockchain-based Distributed Cloud Storage System with Public Verification[J]. Netinfo Security, 2019, 19(3): 52-60.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.03.007
| 符号 | 含义 |
|---|---|
| Flag | 合约类型标识 |
| (pki ,ski) | i的公私钥对 |
| M | 待存数据(常为密文) |
| RM | M的默克尔树根 |
| Nmax | 数据分块最大索引 |
| C-SER | 服务合约 |
| C-STO | 存储合约 |
| ADDserve-i | i的服务合约账户地址 |
| ADDstore | 存储合约账户地址 |
| Tbuild | 合约创建时间 |
| Tserve | 存储服务提供时长 |
| Nserve | 存储空间 |
| Price-unit | 存储市场单价 |
| Contact-i | i的联系方式 |
| PGserve | 存储服务押金 |
| Tvaild | 服务合约有效期 |
| PGstore | 存储押金 |
| PGtotal | 存储合约余额 |
| PGcheck | 用户查询押金 |
| Restore | 存储记录 |
| γ | 单块数据查询费 |
| γ1 | 首次查询某块数据的查询费 |
| Ttrans | 存储合约押金转账时限 |
| Tstore | 数据存储时长 |
| Tcer | 存储证明返回时限 |
| c | 挑战值 |
| Cerstore-c | c对应的存储证明 |
| [1] | FAN Yundong, WU Xiaoping, SHI Xiong.Research on Access Control Model Based on the Trust Value Assessment of Cloud Computing[J]. Netinfo Security, 2016, 16(7):71-77. |
| 范运东,吴晓平,石雄. 基于信任值评估的云计算访问控制模型研究[J]. 信息网络安全,2016,16(7):71-77. | |
| [2] | FIVEASH K. AWS outage knocks Amazon, Netflix,Tinder and IMDb in MEGA data collapse[EB/OL].,2015-9-20. |
| [3] | ZHANG Jinliang. Microsoft Azure Has Suffered a Massive Failure: It Has Now Been Restored[EB/OL].. |
| 张金梁.微软Azure遭遇大面积故障:目前已恢复[EB/OL].. | |
| [4] | SOHU.AWS S3 Cloud Services Disappear Inexplicably: Major Websites and Docker Have Been Tricked[EB/OL]. , 2017-3-1. |
| 搜狐. AWS S3 云服务莫名消失:各大网站和Docker纷纷中招[EB/OL]. . | |
| [5] | GHEMAWAT S, GOBIOFF H, LEUNG S T.The Google File System[J]. Acm Sigops Operating Systems Review, 2003, 37(5): 29-43. |
| [6] | SHVACHKO K, KUANG H, RADIA S, et al.The Hadoop Distributed File System[C]//IEEE. 2010 IEEE 26th Symposium on Mass Storage Systems and Technologies (MSST), May 3-7,2010, Incline Village, NV, USA. NJ: IEEE, 2010: 1-10. |
| [7] | WANG Yujue, WU Qianhong.A Survey on Cryptographic Technologies for Data Integrity Checking in Clouds[J]. Cyber Security, 2017, 2(3): 23-35. |
| 王玉珏, 伍前红. 云存储完整性验证密码学技术研究进展[J]. 信息安全学报, 2017, 2(3): 23-35. | |
| [8] | WANG Qian, WANG Cong, LI Jin, et al.Enabling Public Verifiability and Data Dynamics for Storage Security in Cloud Computing[C]//ESORICS. The 14th European Conference on Research in Computer Security, September 21 - 23, 2009, Saint-Malo, France. Heidelberg: Springer-Verlag Berlin, 2009:355-370. |
| [9] | WANG Qian, WANG Cong, REN Kui, et al.Enabling Public Auditability and Data Dynamics for Storage Security in Cloud Computing[J]. IEEE Transactions on Parallel & Distributed Systems, 2011, 22(5):847-859. |
| [10] | YANG Kan, JIA Xiaohua.An Efficient and Secure Dynamic Auditing Protocol for Data Storage in Cloud Computing[J]. IEEE Transactions on Parallel & Distributed Systems, 2013, 24(9):1717-1726. |
| [11] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. , 2008-10-12. |
| [12] | XIE Hui, WANG Jian.Study on Block Chain Technology and Its Applications[J]. Netinfo Security, 2016,16(9):192-195. |
| 谢辉,王健. 区块链技术及其应用研究[J]. 信息网络安全,2016,16(9):192-195. | |
| [13] | SZABO N.Formalizing and Securing Relationships on Public Networks[EB/OL]. . |
| [14] | JOSEPH P, THADDEUS D. The Bitcoin Lightning Network: Scalable Off-chain Instant Payments[EB/OL].,2015-9-15. |
| [15] | WILKINSON S, BOSHEVSKI T. BRANDOF J, et al. Storj: A Peer-to-Peer Cloud Storage Network[EB/OL].,2017-11-12. |
| [16] | VORICK D, CHAMPINE L. Sia: Simple Decentralized Storage[EB/OL].,2018-1-13. |
| [17] | Protocol Labs. Technical Report: Filecoin: A Decentralized Storage Network [EB/OL]./,2018-2-20. |
| [18] | BENET J.IPFS - Content Addressed,Versioned,P2P File System[EB/OL].. |
| [19] | ZHU Yan, WANG Huaixi, HU Zexing, et al.Zero-knowledge Proofs of Retrievability[J]. Science China(Information Sciences), 2011, 54(8):1608-1617. |
| [20] | Protocol Labs.Technical Report: Proof-of-Replication.[EB/OL].. |
| [21] | BEN-SASSON E, CHIESA A, GENKIN D, et al.Snarks for C: Verifying Program Executions Succinctly and in Zero Knowledge[M]//Springer. Advances in Cryptology-CRYPTO 2013.Heidelberg :Springer Berlin Heidelberg,2013:90-108. |
| [22] | BUTERIN V. Ethereum[EB/OL]. , 2017-9-5. |
| [23] | Codius.Codius[EB/OL].,2018-4-6. |
| [24] | Hyperledger.Hyperledger[EB/OL].,2018-4-6. |
| [1] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [2] | Zhilai MAO, Yanan LIU, Huiping SUN, Zhong CHEN. Research on Blockchain Performance Scalability and Security [J]. Netinfo Security, 2020, 20(3): 56-64. |
| [3] | Weimin LANG, Han ZHANG, Yifeng ZHAO, Jinfang YAO. A Blockchain-based Behavior Regulation and Activities Management Scheme for Internet of Things [J]. Netinfo Security, 2020, 20(2): 22-29. |
| [4] | ZHOU Yihua, LV Zhuqing, YANG Yuguang, SHI Weimin. Data Deposit Management System Based on Blockchain Technology [J]. Netinfo Security, 2019, 19(8): 8-14. |
| [5] | LU Aitong, ZHAO Kuo, YANG Jingying, WANG Feng. Research on Cross-chain Technology of Blockchain [J]. Netinfo Security, 2019, 19(8): 83-90. |
| [6] | ZHENG Min, WANG Hong, LIU Hong, TAN Chong. Survey on Consensus Algorithms of Blockchain [J]. Netinfo Security, 2019, 19(7): 8-24. |
| [7] | ZHOU Yuanjian, QING Dongmei, LIU Yining, LV Songzhan. Design of Electronic Warehouse Receipts System Based on Blockchain [J]. Netinfo Security, 2019, 19(6): 84-90. |
| [8] | WANG Wenming, SHI Chongyang, WANG Yinghao, WEI Dejian. Research on Transaction and Security Based on Blockchain Technology [J]. 信息网络安全, 2019, 19(5): 1-9. |
| [9] | Guofeng ZHAO, Mingcong ZHANG, Jihua ZHOU, Tao ZHAO. Research and Application of Block File Storage Model Based on Blockchain System of Erasure Code [J]. Netinfo Security, 2019, 19(2): 28-35. |
| [10] | LI Peili, XU Haixia, MA Tianjun, MU Yongheng. The Application of Blockchain Technology in Network Mutual Aid and User Privacy Protection [J]. 信息网络安全, 2018, 18(9): 60-65. |
| [11] | DUAN Qiongqiong, XIANG Dinghua, SHI Hongzhou. Design on the Blockchain-based Authentication for Smart Objects [J]. 信息网络安全, 2018, 18(9): 95-101. |
| [12] | LIU Jinghao, PING Jianchuan, FU Xiaomei. Research on A Distributed Public Key System Based on Blockchain [J]. 信息网络安全, 2018, 18(8): 25-33. |
| [13] | HU Wei, WU Qiuhan, LIU Shengli, FU Wei. Design of Secure eID and Identity Authentication Agreement in Mobile Terminal Based on Guomi Algorithm and Blockchain [J]. 信息网络安全, 2018, 18(7): 7-9. |
| [14] | WANG Xing, WENG Jian, ZHANG Yue, LI Ming. Blockchain System for Creating Digital Assets Based on Reputation Value [J]. 信息网络安全, 2018, 18(5): 59-65. |
| [15] | MA Chunguang, AN Jing, BI Wei, YUAN Qi. Smart Contract in Blockchain [J]. 信息网络安全, 2018, 18(11): 8-17. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||