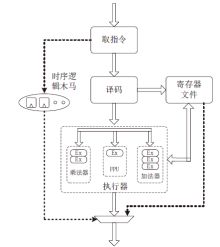
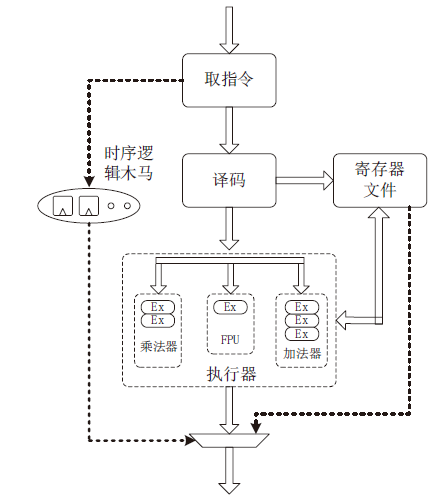
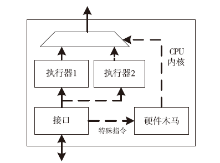
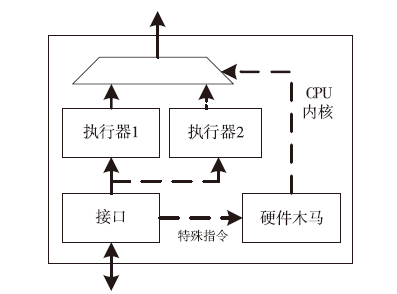
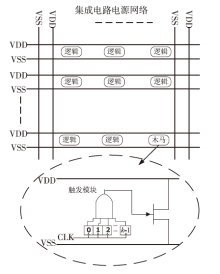
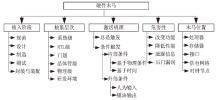
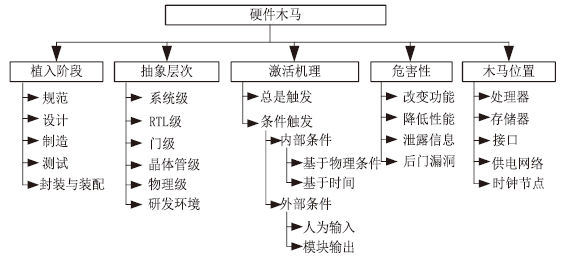
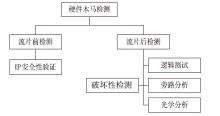
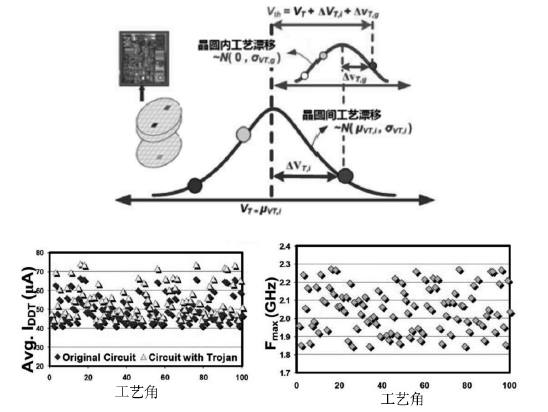
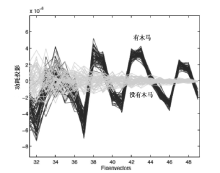
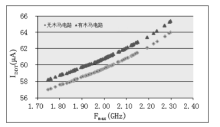
| [1] |
DEFENSE SIENCE BOARD.Report of the Defense Science Board Task Force on High Performance Microchip Supply [R]. Washington DC: Defense Science Board, Feb 2005.
|
| [2] |
LIEBERMAN J.White Paper: National Security Aspects of the Global Migration of the U.S. Semiconductor Industry[R]. Airland Subcommittee, US Senate Armed Services Committee, June 2003.
|
| [3] |
ADEE S.The Hunt for the Kill Switch[J]. IEEE Spectrum, 2008, 45(5): 34-39.
|
| [4] |
MUTSCHLER A S.SEMI:Semi Equipment Industry Stands to Lose up to $4B Annually due to IP Infringements[J]. Electronic News, 2008,54(18):17-22.
|
| [5] |
DEAN COLLINS.Trust in Integrated Circuits and 3rd Party IP[C]//IEEE. International Workshop on Hardware-Oriented Trust Security,2008, Anaheim, CA. New York:IEEE. 2008:19-30.
|
| [6] |
AGRAWAL D, BAKTIR S, KARAKOYUNLU D, et al.Trojan Detection Using IC Fingerprinting[C]//IEEE. Symposium on Security and Privacy, 2007, Berkeley, California. New York: IEEE, 2007:296-310.
|
| [7] |
ABRAMOVICI M, BRADLEY P.Integrated Circuit Security New Threats and Solutions[C]//ACM. 5th Annual Workshop on Cyber Security Information Intellengence Research,2009. Oak Ridge,USA. New York:ACM, 2009:25-27.
|
| [8] |
CHAKRABORTY R S.Hardware Trojan: Threats and Emerging Solutions[C//IEEE. International High Level Design Validation Test Workshop,2009, San Francisco, CA. New York:IEEE, 2009:166-171.
|
| [9] |
LIN L, BURLESON W, PARR C.MOLES: Malicious Off-Chip Leakage Enabled by Side-Channels[C]//IEEE. International Conference on Computer-Aided Design, 2009, San Jose, CA. New York: IEEE, 2009:117-122.
|
| [10] |
KING S.Designing and Implementing Malicious Hardware[C]//USENIX. 1st Usenix Workshop on Large-Scale Exploits and Emergent Threats, 2008, San Francisco, CA. Berkeley: USENIX Association,2008:1-8.
|
| [11] |
Tehranipoor M, Koushanfar F.A survey of Hardware Trojan Taxonomy and Detection[J]. IEEE Design Test Comput., 2010, 27(1) : 10-25.
|
| [12] |
RAJENDRAN J.Towards a Comprehensive and Systematic Classification of Hardware Trojans[C]//IEEE. International Symposium on Circuits and Systems,2010, Pairs. New York: IEEE, 2010:1871-1874.
|
| [13] |
KARRI R, RAJENDRAN J, ROSENFELD K, et al.Trustworthy Hardware: Identifying and Classifying Hardware Trojans[J]. IEEE Computer, 2011, 43(10):39-46.
|
| [14] |
BANGA M, HSIAO M.Trusted RTL: Trojan Detection Methodology in Pre-silicon Designs[C]//IEEE. International Workshop on Hardware-Oriented Trust Security,2010, Anaheim,CA. New York: IEEE.2010:56-59.
|
| [15] |
SMITH S, DI J.Detecting Malicious Logic through Structural Checking[C]//IEEE. Region 5 Technical Conference, 2007, Fayetteville, AR. New York:IEEE, 2007:217-222.
|
| [16] |
ACHARYYA D, PLUSQUELLIC J.Calibrating Power Supply Signal Measurements for Process and Probe Card Variations[C]//IEEE. International Workshop on Current Defect Based Test,2004, Napa Valley, CA. New York:IEEE, 2004:23-30.
|
| [17] |
JIN Y, MAKRIS Y.Hardware Trojan Detection Using Path Delay Fingerprint[C]//IEEE. International Workshop on Hardware-Oriented Trust Security, 2008, Anaheim,CA. New York:IEEE, 2008:51-57.
|
| [18] |
ALKABANI Y, KOUSHANFAR F.Consistency-based Characterization for IC Trojan Detection[C]//IEEE. International Conference on Comput-aided Design, 2009, San Jose, CA. New York:IEEE, 2009:123-127.
|
| [19] |
POTKONJAK M, NAHAPETIAN A, NELSON M, et al.Hardware Trojan Horse Detection Using Gate-level Characterization[C]//IEEE. Proc. Design Automation Conference, 2009.San Francisco, CA. New York:IEEE, 2009:688-693.
|
| [20] |
RAI D, LACH J.Performance of Delay-Based Trojan Detection Techniques under Parameter Variations[C]//IEEE. IEEE International Workshop on Hardware-Oriented Security Trust,2009, Francisco, CA. New York:IEEE, 2009:58-65.
|
| [21] |
AARESTAD J, ACHARYYA D, RAD R, et al.Detecting Trojans though Leakage Current Analysis Using Multiple Supply Pad IDDQs[J]. IEEE Transaction on Information Forensics Security, 2010, 5(4): 893-904.
|
| [22] |
LAMECH C, RAD R M, Tehranipoor M, et al. An experimental Analysis of Power and Delay Signal-to-noise Requirements for Detecting Trojans and Methods for Achieving the Required Detection Sensitivities[J]. IEEE Transaction on Information. Forensics Security, 2011,6(3), pt. 2 : 1170-1179.
|
| [23] |
NARASIMHAN S.Hardware Trojan Detection by Multiple-parameter Side-channel Analysis[J]. IEEE Transaction on Computers. 2013,62(10): 2183-2195.
|
| [24] |
CHAKRABORTY RS, WOLFF F, PAUL S, PAPACHRISTOU C, et al.A Statistical Approach for Hardware Trojan Detection[C]//Springer. Workshop on Cryptographic. Hardware Embedded System, 2009, Lausanne. Berling:Springer 2009:396-410.
|
| [25] |
SALMANI H, TEHRANIPOOR M, PLUSQUELLIC J.A novel Technique for Improving Hardware Trojan Detection and Reducing Trojan Activation Time[J]. IEEE Transaction on Very Large Scale Integrated System, 2011, 20(1): 112-125.
|
| [26] |
ELENA DUBROVA.Keyed Logic BIST for Trojan Detection in SoC[C]//IEEE. International Symposium on System-on-Chip, 2014, Tampere. New York:IEEE, 2014:1-4.
|
| [27] |
BHUNIA S.Protection Against Hardware Trojan Attacks: Towards A Comprehensive Solution[J]. IEEE Design and Test of Computers, 2013, 30(3) : 6-17.
|
| [28] |
SONG P.Malicious Alteration Recognition and Verification by Emission of Light[C]//IEEE. International Symposium on Hardware-Oriented Security and Trust, 2011, San Diego, CA. New York:IEEE, 2011:117-121.
|
| [29] |
STELLARI F.Testing and Diagnostics of CMOS Circuits Using Light Emission from Off-state Leakage Current[J]. IEEE Transaction on Electron Devices, 2004, 51(9): 1455-1462.
|
| [30] |
STELLARI F.Verification of Untrusted Chips Using Trusted Layout and Emission Measurements[C]//IEEE. International Symposium on Hardware-Oriented Security and Trust, 2014, Arlington, VA. New York:IEEE, 2014:19-24.
|