Netinfo Security ›› 2018, Vol. 18 ›› Issue (10): 37-44.doi: 10.3969/j.issn.1671-1122.2018.10.006
Previous Articles Next Articles
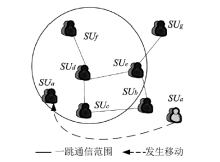
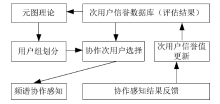
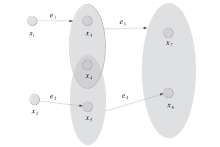
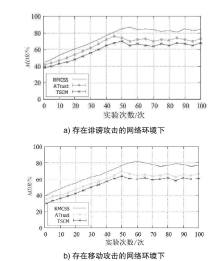
Research on a Trusted Collaborative Second Users Selection Strategy in Distributed Cognitive Radio Networks
Xuli RAO1,2, Hui LIN1( ), Youliang TIAN3, Li XU1
), Youliang TIAN3, Li XU1
- 1.Laboratory of Network Security and Cryptography, Fujian Normal University, Fuzhou Fujian 350007,China
2. Department of Computer, Fuzhou Polytechnic, Fuzhou Fujian 350108, China
3. Guizhou Provincial Key Laboratory of Public Big Data, Guiyang Guizhou 550025, China
-
Received:2018-07-05Online:2018-10-10Published:2020-05-11
CLC Number:
Cite this article
Xuli RAO, Hui LIN, Youliang TIAN, Li XU. Research on a Trusted Collaborative Second Users Selection Strategy in Distributed Cognitive Radio Networks[J]. Netinfo Security, 2018, 18(10): 37-44.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2018.10.006
| [1] | KOLODZY P.Spectrum Policy Task Force Report[J]. Federal Communications Commission Tech, 2002, 40(4):147-158. |
| [2] | MITOLA J I, MAGUIRE G Q.Cognitive Radio: Making Software Radios More Personal[J]. IEEE Personal Communications, 1999, 6(4):13-18. |
| [3] | LANG Weimin, YANG Depeng, LI Husheng.Research on the Spectrum Sensing Data Falsification Attack in the Cognitive Internet of Things[J]. Netinfo Security, 2011,11(10):1-3. |
| 郎为民, 杨德鹏, 李虎生. 认知物联网频谱感知数据伪造攻击研究[J]. 信息网络安全, 2011,11(10):1-3. | |
| [4] | CAO Xianghui, ZHOU Xiangwei, LIU Lu, et al.Energy-Efficient Spectrum Sensing for Cognitive Radio Enabled Remote State Estimation over Wireless Channels[J]. IEEE Transactions on Wireless Communications, 2015, 14(4):2058-2071. |
| [5] | ALTHUNIBAT S, RENZO M D, GRANELLI F.Towards Energy-efficient Cooperative Spectrum Sensing for Cognitive Radio Networks: an Overview[J]. Telecommunication Systems, 2015, 59(1):77-91. |
| [6] | ARIENZO L, TARCHI D.Statistical Modeling of Spectrum Sensing Energy in Multi-Hop Cognitive Radio Networks[J]. IEEE Signal Processing Letters, 2015, 22(3):356-360. |
| [7] | ZHANG Wenlin, GUO Yi, LIU Hongbo, et al.Distributed Consensus-based Weight Design for Cooperative Spectrum Sensing[J]. IEEE Transactions on Parallel & Distributed Systems, 2015, 26(1):54-64. |
| [8] | MOUSAVIFAR S A, LEUNG C.Energy Efficient Collaborative Spectrum Sensing Based on Trust Management in Cognitive Radio Networks[J]. IEEE Transactions on Wireless Communications, 2015, 14(4):1927-1939. |
| [9] | SINGH J S P, SINGHS R, RAI M K, et al. Cooperative Sensing for Cognitive Radio: A Powerful Access Method for Shadowing Environment[J]. Wireless Personal Communications, 2015, 80(4):1363-1379. |
| [10] | CASO G, SOLEIMANI H, NARDIS L D, et al.SENSIC: Mobility-aware Cluster-based Cooperative Spectrum Sensing for Cognitive Radio Networks[C]//IEEE. 2014 IEEE International Conference on Ultra-WideBand (ICUWB), September 1-3, 2014, Saint-Martin, Paris, France. NJ: IEEE, 2014:102-107. |
| [11] | WANG Weiran, YUAN Chaowei.The Design and Implementation of Data Processing Module with Cognitive Radio Function[J]. Netinfo Security, 2015,15(4):68-73. |
| 汪蔚然, 袁超伟. 一种具有认知功能数据处理模块的设计与实现[J]. 信息网络安全, 2015,15(4):68-73. | |
| [12] | CAO Long, ZHAO Hangsheng, ZHANG Jianzhao, et al.Secure Cooperative Spectrum Sensing Based on Energy Efficiency under SSDF Attack[C]//IEEE. 2015 IEEE International Wireless Symposium (IWS 2015), March 30-April 1, 2015, Shenzhen, China. NJ: IEEE, 2015: 1-4. |
| [13] | LANG Weimin, ZHOU Jianhua, LI Jianjun.The Design and Implementation of Data Processing Module with Cognitive Radio Function[J]. Netinfo Security, 2011,11(6):22-25. |
| 郎为民, 周建华, 李建军. 一种对抗无线认知传感器网络攻击的分布式防护研究[J]. 信息网络安全, 2011,11(6):22-25. | |
| [14] | CHATTERJEE S, CHATTERJEE P S.A Comparison Based Clustering Algorithm to Counter SSDF Attack in CWSN[C]//IEEE. 2015 International Conference on Computational Intelligence and Networks (CINE), January 12-13, 2014, Bhubaneswar, India. NJ: IEEE, 2015:194-195. |
| [15] | WANG Hongyue, WANG Shubin, LIU S, et al.An Improved Spectrum Sensing Data-fusion Algorithm Based on Reputation[M]// Springer. The Proceedings of the Third International Conference on Communications, Signal Processing, and Systems. Cham :Springer, Cham, 2015:359-364. |
| [16] | MUHAMMAD S K, INSOO K.Mitigation of Adverse Effects of Malicious Users on Cooperative Spectrum Sensing by Using Hausdorff Distance in Cognitive Radio Networks[J]. Journal of Information and Communication Convergence Engineering, 2015, 13(2): 74-80. |
| [17] | KASIRI B, CAJ J, ALFA A S.Securing Coalitional Game for Distributed Cooperative Spectrum Sensing in Multi-channel Cognitive Radio Networks[J]. Electronic Commerce Research, 2015, 15(1):121-146. |
| [18] | CHAKRABARTI C, ROY S.Adapting Mobility of Observers for Quick Reputation Assignment in a Sparse Post-disaster Communication Network[C]//IEEE. Applications and Innovations in Mobile Computing (AIMoC), February 12-14, 2015, Kolkata, India. NJ: IEEE, 2015:29-35. |
| [19] | YU Han, SHEN Zhiqi, MIAO Chunyan, et al.A Survey of Trust and Reputation Management Systems in Wireless Communications[J]. Proceedings of the IEEE, 2010, 98(10):1755-1772. |
| [20] | EZHEI M, LADANI B T.Gtrust: A Group-based Trust Model[J]. International Journal of Information Security, 2014, 5(2): 155-169. |
| [21] | BASU A, BLANNING R W.Metagraphs and Their Applications[M]. New York: Springer-Verlag, 2006. |
| [22] | POURYAZDAN M, KANTARCI B, SOYATA T, et al.Anchor-Assisted and Vote-based Trustworthiness Assurance in Smart City Crowdsensing[J]. IEEE Access, 2016(4): 529-541. |
| [23] | KANTARIC B, MOUFTAH H T.Trustworthy Sensing for Public Safety in Cloud-centric Internet of Things[J]. IEEE Internet of Things Journal, 2014, 1(4): 360-368. |
| [24] | SUN Yuxing, ZHAO Yanfei, LI Ya, et al.On Incentive Strategies for Trust Recommendations in Wireles Ad Hoc Networks with Probability Game[J]. Computer Science, 2011, 38(4):65-71. |
| 孙玉星,赵燕飞, 李娅, 等. 基于概率博弈的无线自组网信任推荐激励策略的研究[J]. 计算机科学, 2011, 38(4):65-71. | |
| [25] | BIAN Li, ZHU Qi.Cooperative Spectrum Sensing Algorithm Based on Data Fusion[J].Journal of Nanjing University of Posts and Telecommunications, 2009, 29(2):73-78. |
| 卞荔, 朱琦. 基于数据融合的协作频谱感知算法[J]. 南京邮电大学学报, 2009, 29(2):73-78. | |
| [26] | ZHANG Tongjie, Li Zongpeng, SAFAVI-NAINI R.Incentivize Cooperative Sensing in Distributed Cognitive Radio Networks with Reputation-based Pricing[C]//IEEE. IEEE Conference on Computer Communications, April 27-May 2, 2014, Toronto, Canada. NJ:IEEE,2014:2490-2498. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||