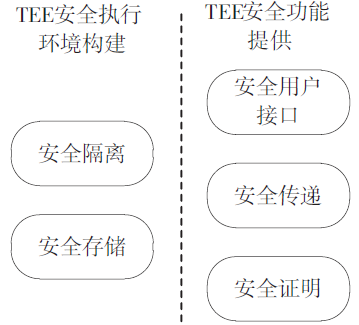
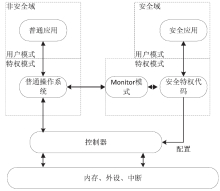
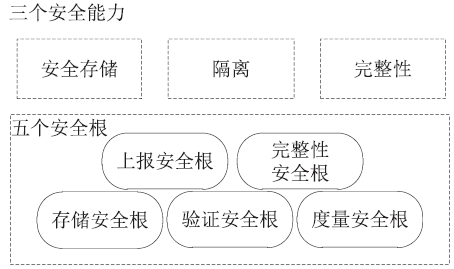
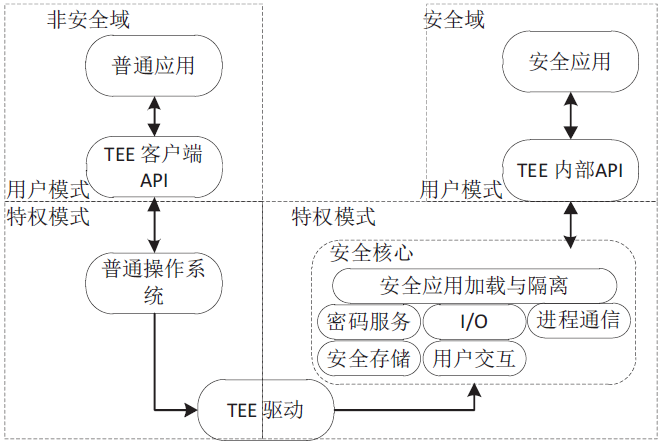
| [1] |
GOOGLE.Google Wallet[EB/OL].,2017-10-15.
|
| [2] |
SAMSUNG.Knox Solutions Covered Every Step of the Way[EB/OL]. ,2017-10-15.
|
| [3] |
ARM.SoC and CPU System-wide Approach to Security[EB/OL]. ,2017-10-15.
|
| [4] |
范冠男,董攀. 基于TrustZone的可信执行环境构建技术研究[J].信息网络安全,2016(3):21-27.
|
| [5] |
MACHIRY A, GUSTAFSON E, SPENSKY C, et al. BOOMERANG: Exploiting the Semantic Gap in Trusted Execution Environments[EB/OL]. , 2017-10-15.
|
| [6] |
GOOGLE.Android Qualcomm Vulnerability Impacts 60 Percent of Devices[EB/OL]. ,2017-10-15.
|
| [7] |
VASUDEVAN A, OWUSU E, ZHOU Z, et al.Trustworthy Execution on Mobile Devices: What Security Properties Can My Mobile Platform Give Me?[C]// Springer .International Conference on Trust and Trustworthy Computing, June 13-15, Vienna, Austria. Berlin: Springer, 2012: 159-178.
|
| [8] |
EKBERG J E, KOSTIAINEN K, ASOKAN N.The Untapped Potential of Trusted Execution Environments on Mobile Devices[J].IEEE Security & Privacy, 2014 , 12(4) :29-37.
|
| [9] |
AZAB A M, SWIDOWSKI K, BHUTKAR R, et al. SKEE: A Lightweight Secure Kernel-level Execution Environment for ARM[EB/OL]. , 2017-10-15.
|
| [10] |
JANG J S, KONG S, KIM M, et al. SeCReT: Secure Channel between Rich Execution Environment and Trusted Execution Environment[EB/OL], 2017-10-15.
|
| [11] |
GE X, VIJAYAKUMAR H, JAEGER T.Sprobes: Enforcing kernel code integrity on the trustzone architecture[J]. Computer Science , 2014 , 25(6) :1793-1795.
|
| [12] |
SUN H, SUN K, WANG Y, et al.Trustotp: Transforming Smartphones into Secure One-time Password Tokens[C]// ACM.Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, October 12 - 16, 2015,Denver, Colorado, USA.New York:ACM, 2015: 976-988.
|
| [13] |
NIST .NIST SP800-164Guidelines on Hardware-Rooted Security in Mobile Devices[EB/OL]. .
|
| [14] |
TRUSTEDCOMPUTINGGROUP.Mobile Trusted Module 2.0 Use Cases FAQ[EB/OL]. .
|
| [15] |
SUN H, SUN K, WANG Y, et al.Trustice: Hardware-assisted Isolated Computing Environments on Mobile Devices[J]. IEEE/IFIP International Conference on Dependable System & Networks, 2015 , 31(2) :367-378.
|
| [16] |
SMALLEY S,CRAIG R.Security Enhanced (SE) Android: Bringing Flexible MAC to Android[EB/OL]..
|
| [17] |
张涛,张勇,宁戈,等. 基于SELinux强制访问控制的进程权限控制技术研究与实现[J].信息网络安全,2015(12):34-41.
|
| [18] |
WANG R, ENCK W, REEVES D S, et al.EASE Android: Automatic Policy Analysis and Refinement for Security Enhanced Android via Large-Scale Semi-Supervised[C]// ACM. SEC'15 Proceedings of the 24th USENIX Conference on Security Symposium,August 12-14, 2015,Washington, D.C.New York:ACM, 2015:351-366.
|
| [19] |
WU C, ZHOU Y, PATEL K, et al. Air Bag: Boosting Smartphone Resistance to Malware Infection[EB/OL]. ,2017-10-15.
|
| [20] |
ANDRUS J,DALL C,HOF A V, et al.Cells: A Virtual Mobile Smartphone Architecture[C]// ACM .Proceedings of the Twenty-Third ACM Symposium on Operating Systems Principles, October 23-26, 2011,Cascais, Portugal. New York:ACM, 2011: 173-187.
|
| [21] |
DALL C, NIEH J.KVM/ARM: the Design and Implementation of the Linux ARM Hypervisor[C]// ACM.ASPLOS '14 Proceedings of the 19th international conference on Architectural support for programming languages and operating systems, March 1-5, 2014,Salt Lake City, Utah, USA.New York:ACM, 2014, 49(4): 333-348.
|
| [22] |
AZAB A M, NING P, SHAH J, et al.Hypervision across Worlds: Real-time Kernel Protection from the Arm Trustzone Secure World[C]// ACM.2014 ACM SIGSAC Conference on Computer and Communications Security. New York:ACM, 2014: 90-102.
|
| [23] |
宫月,李超,吴薇. 虚拟化安全技术研究[J].信息网络安全,2016(9):73-78.
|
 ), Jun GAO2, Qifeng DING3, Yuewu WANG1
), Jun GAO2, Qifeng DING3, Yuewu WANG1