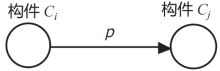
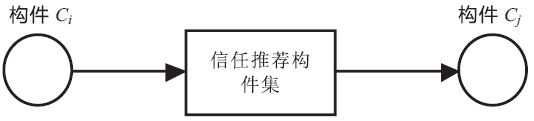
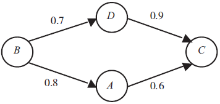
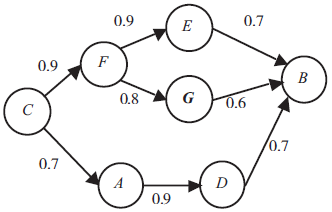
Netinfo Security ›› 2018, Vol. 18 ›› Issue (1): 31-37.doi: 10.3969/j.issn.1671-1122.2018.01.005
• Orginal Article • Previous Articles Next Articles
Analysis and Measurement of Components Trust Relationship in Internetware System
Yong YU1,2( ), Yonggang LIU3, Jie GU1
), Yonggang LIU3, Jie GU1
- 1. School of Software, Yunnan University, Kunming Yunnan 650091, China
2. Key Laboratory of Software Engineering of Yunnan Province, Kunming Yunnan 650091, China
3. School of Software, Beihang University, Beijing 100191, China
-
Received:2017-11-04Online:2018-01-20Published:2020-05-11
CLC Number:
Cite this article
Yong YU, Yonggang LIU, Jie GU. Analysis and Measurement of Components Trust Relationship in Internetware System[J]. Netinfo Security, 2018, 18(1): 31-37.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2018.01.005
| [1] | 杨芙清. 软件工程技术发展思索[J]. 软件学报, 2005, l6(1): 1-7. |
| [2] | REUSSNER R H, SCHMIDT H W, POERNOMO I H.Reliability Prediction for Component-based Software Architectures[J]. Journal of Systems and Software, 2003, 66(3):241-252. |
| [3] | MEYER B.The Grand Challenge of Trusted Components[C] // IEEE. Proc of the 25th International Conference on Software Engineering, May 3-10,2003, Portland, Oregon. Piscataway, NJ:IEEE, 2003:660-667. |
| [4] | BOBBIO A, PORTINALE L, MINICHINO M, et a1. Improving the Analysis of Dependable Systems by Mapping Fault Trees into Bayesian Net Works[J]. Reliability Engineering and System Safety, 2001,71(3):249-260. |
| [5] | SEPANDAR D K, MARIO T S, HECTOR G M.The EigenTrust Algorithm for Reputation Management in P2P Networks[C] //ACM. Proceedings of the 12th International Conference on World Wide Web, May 20-24, 2003, Budapest, Hungary. New York, USA:ACM, 2003:640-651. |
| [6] | 李建, 管卫利, 刘吉强, 等. 基于信任评估的网络访问模型[J]. 信息网络安全, 2015(10):14-23. |
| [7] | WANG Yao, VASSILEVA J.A Review on Trust and Reputation for Web Service Selection[C]// IEEE Computer Society. Proceedings of the 27th International Conference on Distributed Computing Systems Workshops, June 25-29, 2007, Toronto, Canada. Washington, D.C., USA : IEEE, 2007:25. |
| [8] | 肖传奇, 陈明志. 云环境下基于IFAHP的用户行为信任模型研究[J]. 信息网络安全, 2015(12) :14-20. |
| [9] | 李小勇, 桂小林. 动态信任预测的认知模型[J]. 软件学报, 2010, 21(1):163-176. |
| [10] | 印桂生, 王莹洁, 董宇欣. 基于Rough-Fuzzy的网构软件信任度量模型[J]. 哈尔滨工程大学学报, 2013, 34(2):221-226. |
| [11] | 司冠南, 任宇涵, 许静, 等. 基于贝叶斯网络的网构软件可信性评估模型[J]. 计算机研究与发展, 2012, 49(5):1028-1038. |
| [12] | 廖子渊,陈明志,邓辉. 基于评价可信度的云计算信任管理模型研究[J]. 信息网络安全, 2016(2):33-39. |
| [13] | 郭树行, 兰雨晴, 金茂忠. 软件构件的可信保证研究[J]. 计算机科学, 2007, 34(5):243-246. |
| [14] | 邵剑雨, 陈福臻, 秦鹏宇, 等. 移动互联网环境下基于动态信任值的访问控制方法研究[J]. 信息网络安全, 2016(8):46-53. |
| [15] | 王远, 吕建, 徐锋, 等. 一个适用于网构软件的信任度量及演化模型[J]. 软件学报,2006, 17(4):682-690. |
| [16] | 徐锋, 吕建, 郑玮, 等. 一个软件服务协同中信任评估模型的设计[J]. 软件学报, 2003, 14(6): 1043-1051. |
| [17] | 谢新强, 周进刚, 张德阳, 等. 基于复杂网络的网构软件信任模型研究[J].计算机科学与探索,2016, 10(1):56-64. |
| [18] | 张焕国, 赵波. 可信计算[M]. 武汉:武汉大学出版社, 2011. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||