Netinfo Security ›› 2017, Vol. 17 ›› Issue (11): 62-66.doi: 10.3969/j.issn.1671-1122.2017.11.010
• Orginal Article • Previous Articles Next Articles
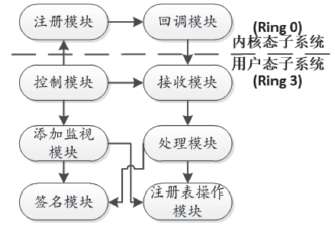
Research on DLL Loading Vulnerability Defense Technology Based on Signature Verification
- College of Computer, National University of Defense Technology, Changsha Hunan 410073, China
-
Received:2017-08-28Online:2017-11-20Published:2020-05-12
CLC Number:
Cite this article
Fengyu LIU, Wei XIE. Research on DLL Loading Vulnerability Defense Technology Based on Signature Verification[J]. Netinfo Security, 2017, 17(11): 62-66.
share this article
| [1] | 梅瑞,孟正,霍玮. 典型文档类CVE漏洞检测工具的研究与实现[J]. 信息网络安全,2014(6):18-22. |
| [2] | HARITHA U, NAIDU V L.A Survey on Windows Component Loading Vulnerabilities[J]. International Journal of Advanced Research in Computer Engineering & Technology (IJARCET), 2013, 2(5): 1780-1783. |
| [3] | LUK C K, COHN R, MUTH R, et al.Pin: Building Customized Program Analysis Tools with Dynamic Instrumentation[C]//ACM. Proceedings of the 2005 ACM SIGPLAN Conference on Programming Language Design and Implementation, June 12 - 15, 2005. Chicago, IL, USA.New York: ACM, 2005: 190-200. |
| [4] | 杜雷,辛阳. 基于规则库和网络爬虫的漏洞检测技术研究与实现[J]. 信息网络安全,2014(10):38-43. |
| [5] | KWON T, SU Zhendong.Automatic Detection of Unsafe Dynamic Component Loadings[J]. IEEE Transactions on Software Engineering, 2012, 38(2): 293-313. |
| [6] | 傅建明, 彭碧琛, 杜浩. 一种组件加载漏洞的动态检测[J].清华大学学报: 自然科学版, 2012, 52(10): 1356-1363. |
| [7] | KWON T, SU Zhendong.Static Detection of Unsafe Component Loadings[A]// Compiler Construction[M]. Heidelberg :Springer Berlin Heidelberg, 2012: 122-143. |
| [8] | MIN B, VARADHARAJAN V.Secure Dynamic Software Loading and Execution Using Cross Component Verification[C]//IEEE. 2015 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), June 22-25, 2015. Rio de Janeiro, Brazil .NJ:IEEE, 2015: 113-124. |
| [9] | 关通,任馥荔,文伟平,等. 基于Windows的软件安全典型漏洞利用策略探索与实践[J]. 信息网络安全,2014(11):59-65. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||