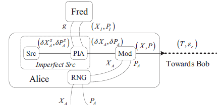
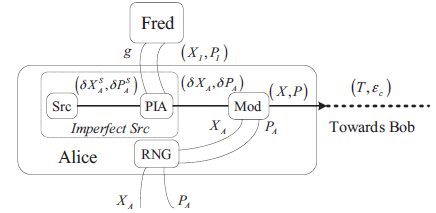
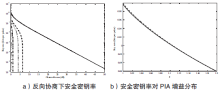
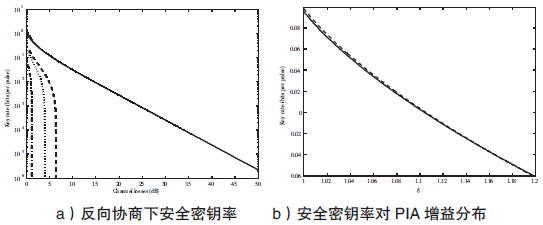
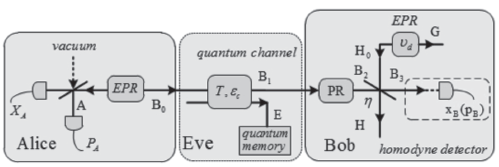
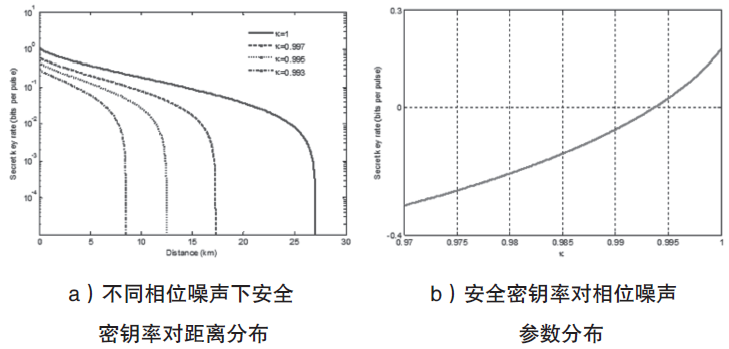
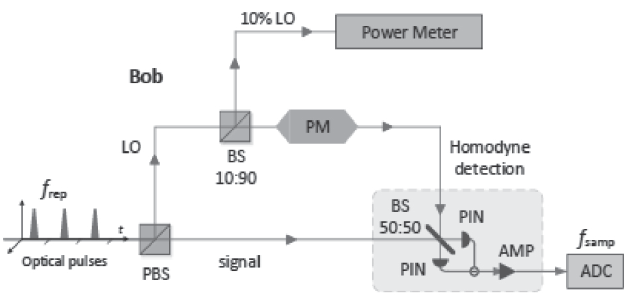
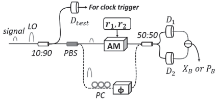
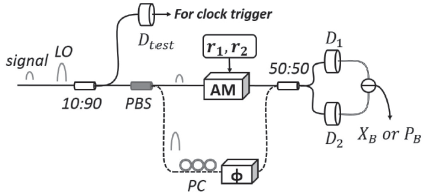
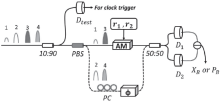
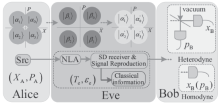
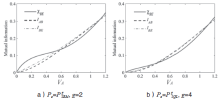
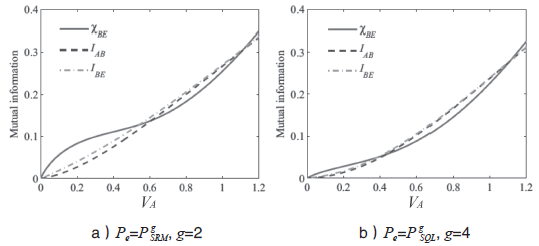
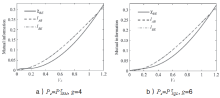
Netinfo Security ›› 2017, Vol. 17 ›› Issue (11): 7-12.doi: 10.3969/j.issn.1671-1122.2017.11.002
• Orginal Article • Previous Articles Next Articles
The Development of Study on Practical Security of Continuous-variable Quantum Key Distribution
- State Key Laboratory of Advanced Optical Communication System and Networks, Shanghai Jiaotong University, Shanghai 200240, China
-
Received:2017-07-01Online:2017-11-20Published:2020-05-12
CLC Number:
Cite this article
Peng HUANG, Guihua ZENG. The Development of Study on Practical Security of Continuous-variable Quantum Key Distribution[J]. Netinfo Security, 2017, 17(11): 7-12.
share this article
| [1] | RALPH T. C. Continuous Variable Quantum Cryptography [J]. Physical Review A, 1999(61):010303(R). |
| [2] | RALPH T C.Security of Continuous-variable Quantum Cryptography[J]. Physical Review A, 2000(62): 062306. |
| [3] | WEEDBROOK C, PIRANDOLA S, CERF N J, et al.Gaussian Quantum Information[J]. Review of Modern Physics, 2012, 84(6): 621. |
| [4] | LEVERRIER A,GRANGIER P.Unconditional Security Proof of Long-distance Continuous-variable Quantum Key Distribution with Discrete Modulation[J]. Physical Review Letters, 2009, 102(18):180504. |
| [5] | LEVERRIER A,GRANGIER P. Erratum: Unconditional Security Proof of Long Distance Continuous-variable Quantum Key Distribution with Discrete Modulation [phys. rev. lett. 102, 180504 (2009)][J]. Phys. Rev. Lett., 2011(106): 259902. |
| [6] | LEVERRIER A, GRANGIER P.Continuous-variable Quantum-key-distribution Protocols with a non-gaussian Modulation[J]. Physical Review A, 2011, 83(4): 042312. |
| [7] | GARCIA-PATRON R, CERF J N.Unconditional Optimality of Guassian Attacks against Continuous-variable Quantum Key Distribution[J].Physical Review Letters, 2006(97):190503. |
| [8] | NAVASCUÉS M, F.GROSSHANS, ACIN A. Optimality Of Gaussian Attacks In Continuous-Variable Quantum Cryptography[J]. Physical Review Letters, 2006(97):190502. |
| [9] | RENNER R, CIRAC J I.Definetti Representation Theorem For Infinite-Dimensional Quantum Systems And Applications To Quantum Cryptography[J]. Physical Review Letters, 2009(102): 110504. |
| [10] | LEVERRIER A, GARCÍA-PATRÓN R, RENNER R, et al. Security Of Continuous-Variable Quantum Key Distribution Against General Attacks[J]. Physical Review Letters, 2013(110): 030502. |
| [11] | LEVERRIER A.Composable Security Proof For Continuous-Variable Quantum Key Distribution With Coherent States[J]. Physical Review Letters, 2015(114): 070501. |
| [12] | HUANG Peng, HE Guangqiang, ZENG Guihua.Bound On Noise Of Coherent Source For Secure Continuous-Variable Quantum Key Distribution[J]. Int. J. Theor. Phys, 2013(52): 1572-1582. |
| [13] | HUANG Peng, LIN Dakai, HUANG Duan, et al.Security Of Continuous-Variable Quantum Key Distribution With Imperfect Phase Compensation[J]. Int. J. Theor. Phys., 2015, 52(5):1572-1582. |
| [14] | WANG Chao, HUANG Peng, HUANG Duan, et al.Practical Security Of Continuous-Variable Quantum Key Distribution With Finite Sampling Bandwidth Effects[J]. Physical Review A, 2016, 93(2): 022315. |
| [15] | MA XiangChun, SUN Shihai, JIANG Musheng, et al.Local Oscillator Fluctuation Opens A Loophole For Eve In Practical Continuous-Variable Quantum-Key-Distribution Systems[J]. Physical Review A, 2013(88):022339. |
| [16] | HUANG Jingzheng, WEEDBROOK C, YIN Zhenqiang, et al.Quantum Hacking Of A Continuous-Variable Quantum-Key-Distributionsystem Using A Wavelength Attack[J]. Physical Review A, 2013(87):062329. |
| [17] | HUANG Jingzheng.Quantum Hacking on Quantum Key Distribution using Homodyne Detection[J].Physical Review A, 2014(89):032304. |
| [18] | MA Xiangchun, SUN Shihai, JIANG Musheng, et al.Wavelength Attack on Practical Continuous-variable Quantum-key-distribution System with a Heterodyne Protocol[J].Physical Review A, 2013(87):052309. |
| [19] | PAUL J, SEBASTIEN K J, ELENI D.Preventing Calibration Attacks on the Local Oscillator in Continuous-variable Quantum Key Distribution[J]. Physical Review A, 2013(87):062313. |
| [20] | QIN H, KUMAR R, ALLEAUME R. Saturation Attack on Continuous-variable Quantum Key Distribution System [EB/OL]. , 2017-8-1. |
| [21] | HUANG Peng, FANG Jian, ZENG Guihua.State-Discrimination Attack On Discretely Modulated Continuous-Variable Quantum Key Distribution[J]. Physical Review A, 2014, 89(4): 042330. |
| [22] | QIN Hao, KUMAR Rupesh, ALLEAUME Romain.Quantum Hacking: Saturation Attack On Practical Continuous-Variable Quantum Key Distribution[J]. Physical Review A, 2016(94): 012325. |
| [23] | LI Zhengyu, ZHANG Yichen, XU Feihu.Continuous-variable Measurement-device-independent QuantumKey Distribution[J]. Physical Review A, 2014(89): 052301. |
| [24] | MA Xiangchun, SUN Shihai, JIANG Musheng.Gaussian-modulated Coherent-state Measurement-device-independent Quantum Key Distribution[J]. Physical Review A, 2014(89):042335. |
| [25] | ZHANG Yichen, LI Zhengyu, YU Song.Continuous-variable Measurement-device-independent Quantum Key Distribution[J]. Physical Review A, 2014(90): 052325. |
| [26] | PIRANDOLA S, OTTAVIANI C, SSPEDALIERI G, et al.High-rate Measurement-device-independent Quantum Cryptography[J]. Nature Photonics, 2015(9): 397-402. |
| [1] | Gaoshou ZHAI, Chen LIU, Yong XIANG. Study and Implementation of Systematic Protection by Monitoring Abnormal Invocation of Linux Kernel Functions [J]. Netinfo Security, 2018, 18(3): 26-38. |
| [2] | Zhuoqun XIA, Lei ZHAO, Jing WANG, Wenhuan LI. Research on a Privacy Protection Method for Power Users Based on Virtual Ring Architecture [J]. Netinfo Security, 2018, 18(2): 48-53. |
| [3] | Shuning WEI, Xingru CHEN, Yong TANG, Hui LIU. Research on the Application of AR-HELM Algorithm in Network Traffic Classifi cation [J]. Netinfo Security, 2018, 18(1): 9-14. |
| [4] | Guofeng ZHAO, Fei YE, Yongan YAO, Yan ZHAO. Design and Implementation of A Multi-pattern String Matching Algorithm in Cloud Center Network Intrusion Detection System [J]. Netinfo Security, 2018, 18(1): 52-57. |
| [5] | Baoyuan KANG, Jiaqiang WANG, Dongyang SHAO, Chunqing LI. A Secure Authentication and Key Agreement Protocol for Heterogeneous Ad Hoc Wireless Sensor Networks [J]. Netinfo Security, 2018, 18(1): 23-30. |
| [6] | Yue SHI, Xianglong LI, Fangfang DAI. An Enhanced Security Framework of Software Defi ned Network Based on Attribute-based Encryption [J]. Netinfo Security, 2018, 18(1): 15-22. |
| [7] | Jianbiao ZHANG, Zixiao ZHAO, Jun HU, Xiao WANG. The Design Framework of Reconfi gurable Virtual Root of Trust in Cloud Environment [J]. Netinfo Security, 2018, 18(1): 1-8. |
| [8] | ZHANG Hongyan, XU Li, LIN Limei. Research on Pairwise Key Establishment Scheme Based on Hypercube in Wireless Sensor Network [J]. 信息网络安全, 2017, 17(12): 1-5. |
| [9] | SONG Limin, SONG Xiaorui. Design and Implementation of a Data Security Transmission Scheme Based on Hybrid Encryption [J]. 信息网络安全, 2017, 17(12): 6-10. |
| [10] | ZHAO Guofeng, ZHAO Yan, WANG Xinheng, YE Fei. A New Design of Suspicious Domain Name Monitoring System for Web Communication [J]. 信息网络安全, 2017, 17(12): 11-16. |
| [11] | TANG Chunming, GAO Long. Multi-parties Key Agreement Protocol in Block Chain [J]. 信息网络安全, 2017, 17(12): 17-21. |
| [12] | XU Yang, CHEN Yi, HE Rui, XIE Xiaoyao. Research of DDoS Detection and Multi-layer Defense in SDN [J]. 信息网络安全, 2017, 17(12): 22-28. |
| [13] | GUL Khan Safi Qamas, WANG Peng, LUO Senlin, PAN Limin. A Technical Research on High-concurrency Web Application [J]. 信息网络安全, 2017, 17(12): 29-35. |
| [14] | WU Tong, LI Siqi, YANG Weijun, ZHAO Li. Research on Cloud Storage Data Forensics Method Based on KMP Algorithm [J]. 信息网络安全, 2017, 17(12): 36-39. |
| [15] | LI Hongling, ZOU Jianxin. Research of SQL Injection Detection Based on SVM and Text Feature Extraction [J]. 信息网络安全, 2017, 17(12): 40-46. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||