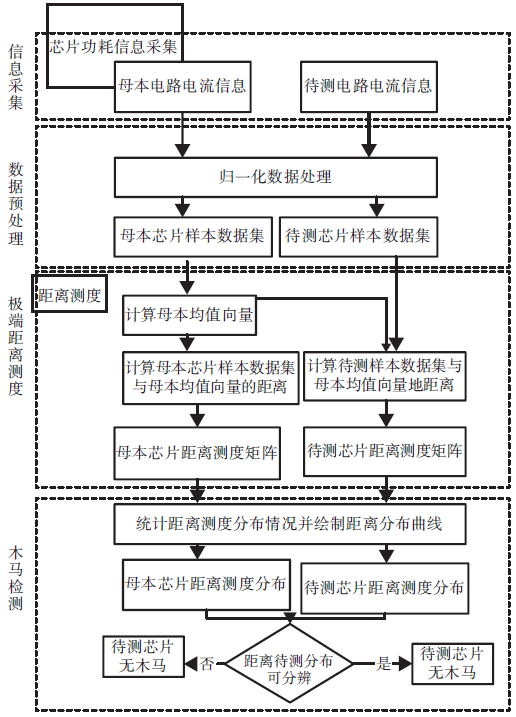
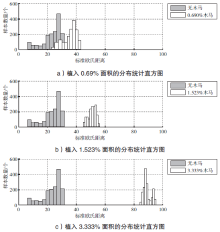
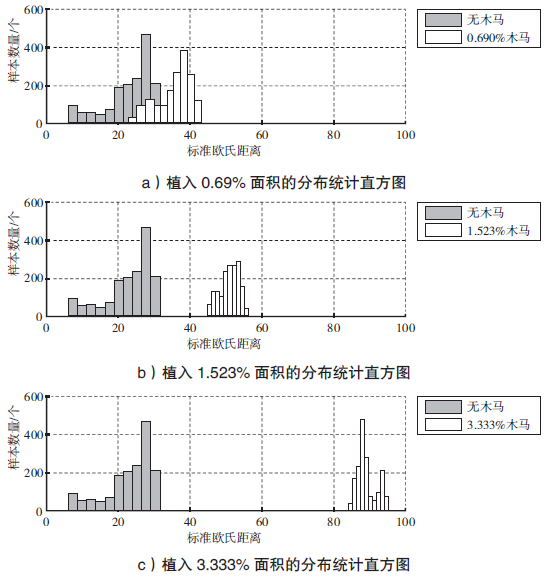
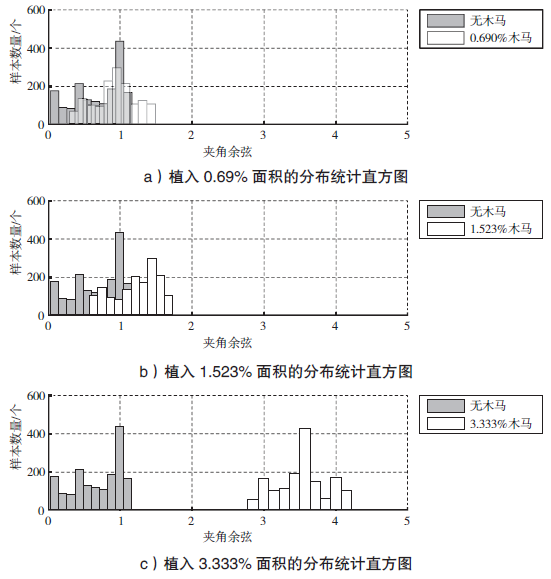
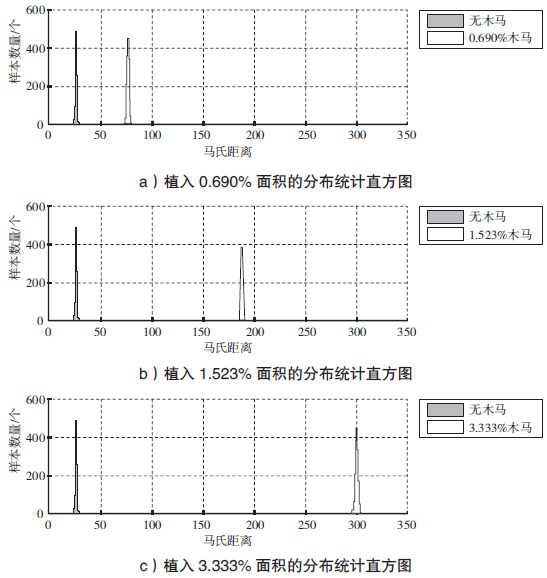
| [1] |
HE L, LIU Q,ZHANG J.A Survey of Hardware Trojan Threat and Defense[J]. INTEGRATION, the VLSI journal, 2016,55:426-437.
|
| [2] |
MITRA S, WONG H S P , WONG S, The Trojan-proof Chip[J]. Spectrum IEEE,2015 , 52(2) :46-51.
|
| [3] |
CHAKRABORTY R S,SAHA I, PALCHAUDHURI A,et al.Hardware Trojan Insertion by Direct Modification of FPGA Configuration Bitstream[J]. IEEE Design & Test , 2013 , 30(2) :45-54.
|
| [4] |
SHILA D M,VENUGOPAL V.Design, Implementation and Security Analysis of Hardware Trojan Threats in FPGA[C]// ACM . FPGA '14 Proceedings of the 2014 ACM/SIGDA international symposium on Field-programmable gate arrays,February 26 - 28, 2014,Monterey, California, USA .ACM:New York, 2014:719-724.
|
| [5] |
KIM L W,VILLASENOR J D.Dynamic Function Replacement for System-on-chip Security in the Presence of Hardware-based Attacks[J]. IEEE Transactions on Reliability , 2014 , 63(2) :661-675.
|
| [6] |
RUDRA M R,DANIEL N A,NAGOORKAR V,et al.Designing Stealthy Trojans with Sequential Logic: A Stream Cipher Case Study[EB/OL]. https://www.researchgate.net/publication/266657437_Designing_Stealthy_Trojans_with_Sequential_Logic_A_Stream_Cipher_Case_Study,2016-7-15.
|
| [7] |
BHASIN S,REGAZZONI F.A Survey on Hardware Trojan Detection Techniques[C]//IEEE.IEEE International Symposium on Circuits and Systems (ISCAS), May 24-27, Lisbon, Portugal. IEEE:New York,2015: 2021-2024.
|
| [8] |
WANG X X, SALMANI H,TEHRANIPOOR M, et al.Hardware Trojan Detection and Isolation Using Current Integration and Localized Current Analysis[C]// IEEE .2012 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems, October 1-3,2008,Boston, MA, USA. IEEE:New York,2008:87-95.
|
| [9] |
AGRAWAL D, BAKTIR S, ARKOYUNLU D, et al.Trojan Detection Using IC Fingerprinting[C]// IEEE .IEEE Symposium on Security and Privacy,May 20-23,Berkeley, CA, USA . IEEE:New York, 2007:296-310.
|
| [10] |
张鹏,王新成,周庆.基于投影寻踪分析的芯片硬件木马检测[J].通信学报, 2013, 34(4):122-126.
|
| [11] |
刘长龙,赵毅强,史亚峰,等.基于相关性分析的硬件木马检测方法[J].计算机工程,2013, 39(9):183-185.
|
| [12] |
王力纬,贾鲲鹏,方文啸,等.基于马氏距离的硬件木马检测方法[J].微电子学, 2013(6):817-820.
|
| [13] |
周昱,于宗光. 硬件木马威胁与识别技术综述[J]. 信息网络安全,2016(1):11-17.
|
| [14] |
赵毅强,杨松,何家骥,等.基于主成分分析的硬件木马检测方法[J].华中科技大学学报(自然科学版), 2015, 43(8):66-69.
|
| [15] |
蒋政君,田海博,张方国. 基于PUF的RFID防伪技术研究综述[J]. 信息网络安全,2016(4):38-43.
|
| [16] |
刘长龙,赵毅强,史亚峰,等.基于侧信道分析的硬件木马的建模与优化[J].华中科技大学学报(自然科学版), 2013, 41(2):53-57.
|
| [17] |
王庆,屠晨阳,沈嘉荟. 侧信道攻击通用框架设计及应用[J]. 信息网络安全,2017(5):57-62.
|
| [18] |
吴晓萍,赵学靖,乔辉,等.基于LASSO-SVM的软件缺陷预测模型研究[J].计算机应用研究, 2013, 43(8):66-69.
|
| [19] |
刘长龙. 基于侧信道分析的硬件木马检测方法研究[D].天津:天津大学电子信息工程学院,2013.
|
| [20] |
冯紫竹. 基于侧信道分析的硬件木马检测平台设计[D].天津:天津大学电子信息工程学院,2013.
|
 ), Yiqiang ZHAO1, Zhongwei ZHANG2, Yanfang XIE2
), Yiqiang ZHAO1, Zhongwei ZHANG2, Yanfang XIE2