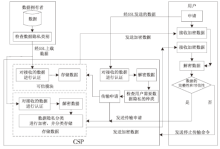
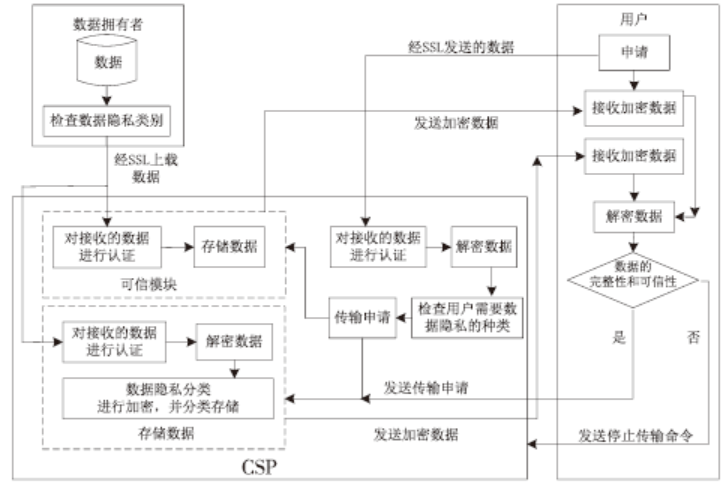
| [1] |
赵洋,包文意,熊虎,等. 云计算里一种陷门无法识别的公钥搜索加密方案[J]. 信息网络安全,2016(1):1-5.
|
| [2] |
SCHAFFER, H E.X as a Service, Cloud Computing, and the Need for Good Judgment[J].IT Professiona,2009,11(5):4-5.
|
| [3] |
程思嘉,张昌宏,潘帅卿. 基于CP-ABE算法的云存储数据访问控制方案设计[J]. 信息网络安全,2016(2):1-6.
|
| [4] |
KAUFMAN L M.Data Security in the World of Cloud Computing[J].IEEE Security & Privacy, 2009,7(4):61-64.
|
| [5] |
SANKA S, HOTA C, RAJARAJAN M.Secure Data Access in Cloud Computing[C]// IEEE. 4th International Conference on Internet Multimedia Services Architecture and Application,December 15-17,2010,Bangalore,India.New York: IEEE,2010: 1-6.
|
| [6] |
PANDA S N, KUMAR G.IDATA - an Effective Intercept Detection Algorithm for Packet Transmission in Trust Architecture[J].Global Journal of Computer Science & Technology,2010,13(15):15-18.
|
| [7] |
ITANI W, KAYSSI A, CHEHAB A.Privacy as a Service: Privacy-aware Data Storage and Processing in Cloud Computing Architectures[C]//IEEE.8th International Conference on Dependable, Autonomic and Secure Computing,December 12-14, 2009,Chengdu,China. New York: IEEE,2009:711-717.
|
| [8] |
GELLMAN R. Privacy in the Clouds: Risks to Privacy and Confidentiality from Cloud Computing[EB/OL].,2009-2-23.
|
| [9] |
PEARSON S.Taking Account of Privacy when Designing Cloud Computing Services[C]// IEEE.2009 ICSE Workshop on Software Engineering Challenges of Cloud Computing, May 23, 2009, Washington, DC, USA. New York: IEEE, 2009: 44-52.
|
| [10] |
PEARSON S, CHARLESWORTH A.Accountability as a Way Forward for Privacy Protection in the Cloud[C]// Springer.First International Conference on Cloud Computing,December 1-4, 2009 ,Beijing,China. Berlin Heidelberg:Springer,2009:131-144.
|
| [11] |
YOUSRA A A S A, MAZLEENA S, YAZAN A. An Innovative Privacy Preserving Technique for Incremental Datasets on Cloud Computing[J].Journal of Biomedical Informatics,2016,62: 107-116.
|
| [12] |
SYAM K P,SUBRAMANIAN R,RAJKUMAR B.An Efficient and Secure Privacy-preserving Approach for Outsourced Data of Resource Constrained Mobile Devices in Cloud Computing[J].Journal of Network and Computer Applications, 2016, 64: 12-22.
|
| [13] |
HUI L,LI X,YI M,et al.A Reliable Recommendation and Privacy-preserving based Cross-layer Reputation Mechanism for Mobile Cloud Computing[J].Future Generation Computer Systems,2015,52:125-136.
|
| [14] |
WEI S,BING W,QIAN W,et al.A Privacy-preserved Full-text Retrieval Algorithm over Encrypted Data for Cloud Storage Applications[J].Journal of Parallel and Distributed Computing,2017, 99:14-27.
|
| [15] |
JIN L, ZhELI L, XIAOFENG C, et al. L-EncDB: A Lightweight Framework for Privacy-preserving Data Queries in Cloud Computing[J].Knowledge-Based Systems, 2015, 79: 18-26.
|
| [16] |
MEHDI S, ABDULLAH G, MUHAMMAD K K, et al.Dynamic Remote Data Auditing for Securing Big Data Storage in Cloud Computing[J].Information Sciences, 2017, 380:101-116.
|
| [17] |
XIN D,JIADI Y,YUAN L,et al.Achieving an Effective, Scalable and Privacy-preserving Data Sharing Service in Cloud Computing[J].Computers & Security, 2014, 42: 151-164.
|
| [18] |
WEI L F, ZHU H J, CAO Z F, et al.Security and Privacy for Storage and Computation in Cloud Computing[J].Information Sciences, 2014, 258: 371-386.
|
| [19] |
HUANG Q L,MA Z F, YANG Y X, et al.Secure and Privacy-preserving DRM Scheme Using Homomorphic Encryption in Cloud Computing[J].The Journal of China Universities of Posts and Telecommunications, 2013, 20(6): 88-95.
|
| [20] |
廖子渊,陈明志,邓辉. 基于评价可信度的云计算信任管理模型研究[J]. 信息网络安全,2016(2):33-39.
|
 )
)