Netinfo Security ›› 2016, Vol. 16 ›› Issue (11): 12-18.doi: 10.3969/j.issn.1671-1122.2016.11.003
• Orginal Article • Previous Articles Next Articles
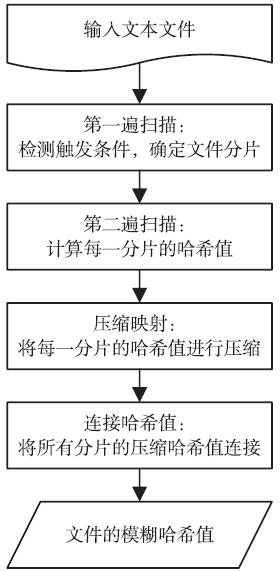
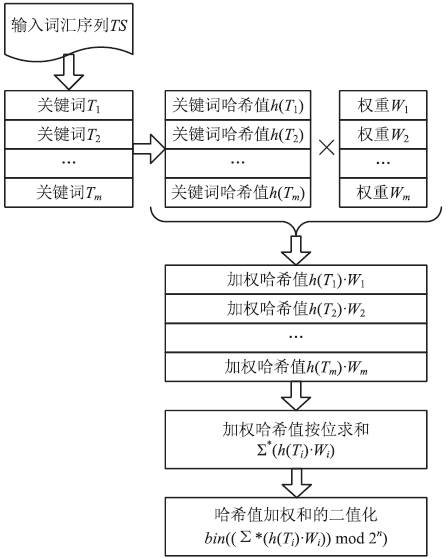
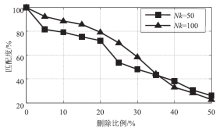
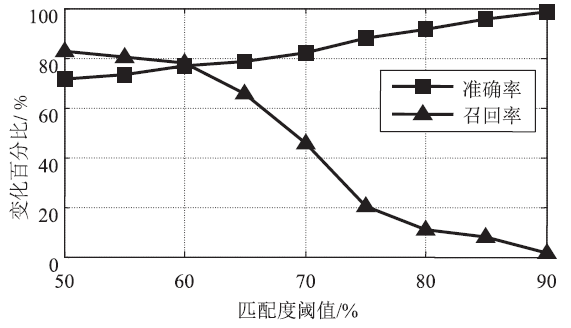
Research on Document Comparison Algorithm Based on Modified Fuzzy Hash
Hongyu DI1, Jing ZHANG1, Yi YU2, Lianyin WANG2( )
)
- 1. Beijing Wondersoft Technology Co., Ltd., Beijing 100097, China
2. Information Center of the General Administration of Quality Supervision Inspection and Quarantine of the People’s Republic of China, Beijing 100088, China;
-
Received:2016-09-18Online:2016-11-20Published:2020-05-13
CLC Number:
Cite this article
Hongyu DI, Jing ZHANG, Yi YU, Lianyin WANG. Research on Document Comparison Algorithm Based on Modified Fuzzy Hash[J]. Netinfo Security, 2016, 16(11): 12-18.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2016.11.003
| [1] | 胡雪,封化民,李明伟,等. 数据挖掘中一种增强的Apriori算法分析[J]. 信息网络安全,2015(11):77-83. |
| [2] | ZAMORA J, MENDOZA M, ALLENDE H.Hashing-based Clustering in High Dimensional Data[J]. Expert Systems with Applications, 2016, 62(15): 202-211. |
| [3] | KHAN S, GANI A, WAHAB A W A, et al. Network Forensics: Review,Taxonomy,Open Challenges[EB/OL]., 2016-3-20. |
| [4] | 李亚萌,何泾沙. 基于Hash的YAFFS2文件各版本恢复算法研究[J]. 信息网络安全,2016(5):51-57. |
| [5] | CHRISTIAN W, MARKUS S, YORK Y.F2S2: Fast Forensic Similarity Search through Indexing Piecewise Hash Signatures[J]. Digital Investigation, 2013, 10(4): 361-371. |
| [6] | 王建峰. 基于哈希的最近邻查找[D]. 合肥:中国科学技术大学,2015. |
| [7] | INDYK P, MOTWANI R.Approximate Nearest Neighbors: Towards Removing the Curse of Dimensionality[C]//ACM. 30th Annual ACM Symposium on Theory of Computing, May 24-26, 1998, Dallas, Texas, USA. New York: ACM, 1998: 604-613. |
| [8] | BREITINGER F, BAIER H.Performance Issues about Context-triggered Piecewise Hashing[C]//EAI. Third International ICST Conference, October 26-28, 2011, Dublin, Ireland. Heidelberg: Springer, 2011: 141-155. |
| [9] | CHARIKAR M S.Similarity Estimation Techniques from Rounding Algorithms[C]//ACM. 34th Annual ACM Symposium on Theory of Computing, May 19-21, 2002, Montreal, Quebec, Canada. New York: ACM, 2002: 380-388. |
| [10] | 刘禹. 中文新闻分类语料库[EB/OL]. , 2016-6-20. |
| [11] | 尚海,罗森林,韩磊,等. 基于句义成分的短文本表示方法研究[J]. 信息网络安全,2016(5):64-70. |
| [12] | 李荣陆. 文本分类语料库(复旦)[EB/OL]. , 2016-6-21. |
| [13] | BREITINGER F, STIVAKTAKIS G, BAIER H.FRASH: A Framework to Test Algorithms of Similarity Hashing[J]. Digital Investigation, 2013, 10(10): 1066-1069. |
| [14] | National Institute of Standards and Technology. National Software Reference Library[EB/OL]. , 2016-6-21. |
| [15] | PAULEVE L, JEGOU H, AMSALEG L.Locality Sensitive Hashing: A Comparison of Hash Function Types and Querying Mechanisms[J]. Pattern Recognition Letters, 2010, 31(11): 1348-1358. |
| [16] | KORNBLUM J.Identifying Almost Identical Files Using Context Triggered Piecewise Hashing[J]. Digital Investigation the International Journal of Digital Forensics & Incident Response, 2006, 3(3): 91-97. |
| [17] | 史记,曾昭龙,杨从保,等. Fuzzing测试技术综述[J]. 信息网络安全,2014(3):87-91. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||