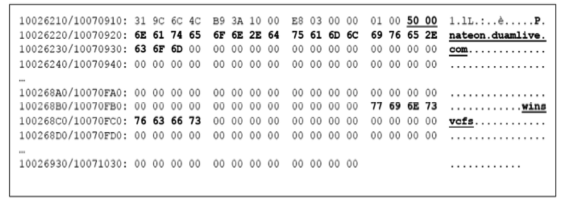
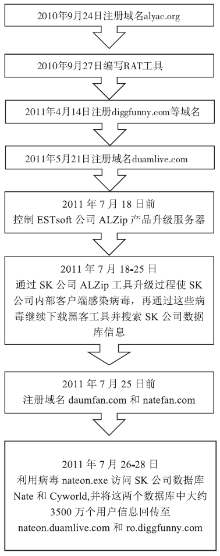
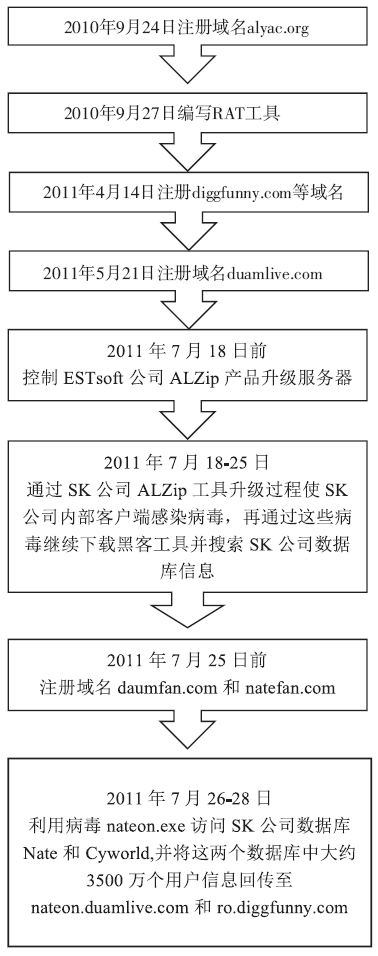
Netinfo Security ›› 2016, Vol. 16 ›› Issue (9): 118-123.doi: 10.3969/j.issn.1671-1122.2016.09.024
• Orginal Article • Previous Articles Next Articles
Analysis of APT Attack Principle and Protection Technology
- People's Procuratorate of Henan Province, Zhengzhou Henan 450004, China