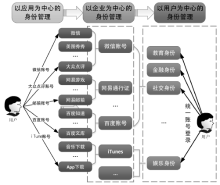
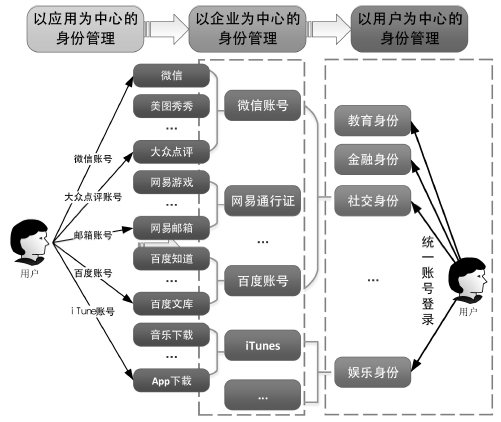
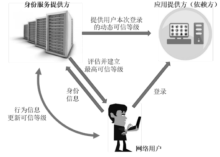
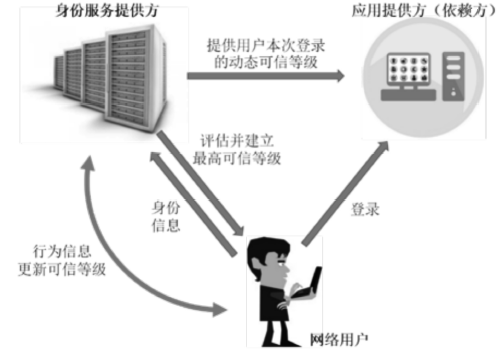
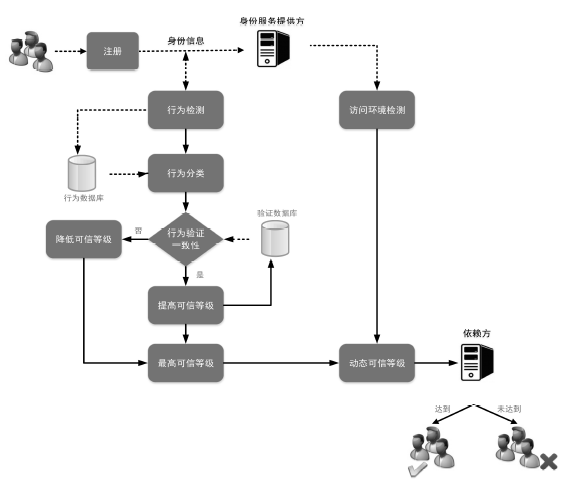
Netinfo Security ›› 2016, Vol. 16 ›› Issue (9): 124-129.doi: 10.3969/j.issn.1671-1122.2016.09.025
• Orginal Article • Previous Articles Next Articles
Research on Identity Trusted Level Evaluation Mechanism Based on User Behavior Analysis
- Data Assurance and Communication Security Research Center, Chinese Academy of Sciences, Beijing 100093, China
-
Received:2016-07-25Online:2016-09-20Published:2020-05-13
CLC Number:
Cite this article
Jia PENG, Neng GAO. Research on Identity Trusted Level Evaluation Mechanism Based on User Behavior Analysis[J]. Netinfo Security, 2016, 16(9): 124-129.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2016.09.025
| [1] | STERNER E.Retaliatory Deterrence in Cyberspace[J]. Strategic Studies Quarterly, 2011,5(1):62. |
| [2] | National Audit Office. Identity Assurance Programme[EB/OL]. ,2014-12-10. |
| [3] | MANTELERO A.The EU Proposal for a General Data Protection Regulation and the Roots of the ‘Right to Be Forgotten’[J]. Computer Law & Security Report, 2013, 29(29):229-235. |
| [4] | 范月,许晋,高宇童. eID移动身份认证系统的研究与实现[J]. 信息网络安全,2015(3):48-53. |
| [5] | ELDON, ERIC. Single Sign-on Service OpenID Getting More Usage [EB/OL]. , 2009-04-25. |
| [6] | WHITSON G. Understanding OAuth: What Happens When You Log Into a Site with Google, Twitter, or Facebook [EB/OL]. ,2016-05-15. |
| [7] | Wikipedia.Security Assertion Markup Language [EB/OL]. , 2016-6-7. |
| [8] | MATT H., 2014-10-4. |
| [9] | 武传坤. 身份证件的安全要求和可使用的密码学技术[J]. 信息网络安全,2015(5):21-27. |
| [10] | MONROSE F, RUBIN A .Authentication via Keystroke Dynamics[C]//ACM.4th ACM Conference on Computer and Communications Security, April 1-4, 1997, Zurich, Switzerland.New York: ACM,1997:48-56. |
| [11] | FEHER C, ELOVICI Y, Moskovitch R, et al.User Identity Verification via Mouse Dynamics[J]. Information Sciences, 2012, 201(19):19-36. |
| [12] | VELTEN M, SCHNEIDER P, WESSEL S, et al.User Identity Verification Based on Touchscreen Interaction Analysis in Web Contexts[M].Berlin Heidelberg:Springer , 2015. |
| [13] | WESOLOWSKI T, KUDLACIK P.User Profiling Based on Multiple Aspects of Activity in a Computer System[J]. Journal of Medical Informatics & Technologies, 2014,11(6):121-130. |
| [14] | 徐剑,赵英南,田永纯,等. 融合二维码与人脸识别的会议身份认证系统研究[J]. 信息网络安全,2015(4):13-18. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||