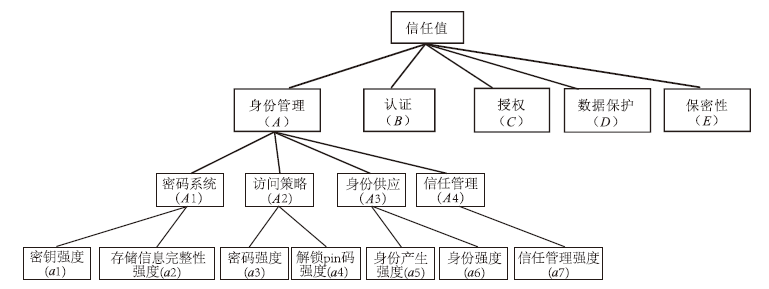
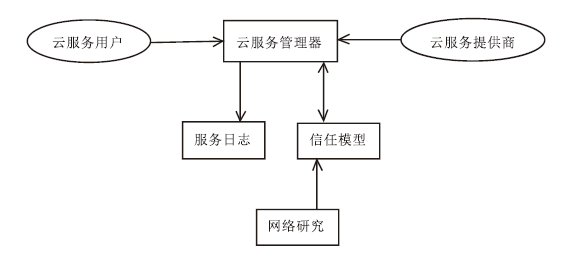
| [1] |
张琳,王汝传,张永平.一种基于模糊集合的可用于网格环境的信任评估模型[J].电子学报,2008,36(5):862-868.
|
| [2] |
田立勤,林闯.基于双滑动窗口的用户行为信任评估机制[J].清华大学学报:自然科学版,2010,50(5):763-767.
|
| [3] |
田俊峰,曹迅.基于多部图的云用户行为认定模型[J].计算机研究与发展,2014,51(10):2308-2317.
|
| [4] |
王汝传,张琳,饶凯莉.云计算环境下基于评价可信度的动态信任评估模型[J].通信学报,2013,2013(S1):31-37.
|
| [5] |
周茜,于炯. 云计算下基于信任的防御系统模型[J]. 计算机应用,2011, 31(6):1531-1535.
|
| [6] |
BROSSO I,NEVE A L,BRESSAN G,et al.A Continuous Authentication Aystem Based on User Behavior Analysis[C]//IEEE.2012 Seventh International Conference on Availability, Reliability and Security (2010),February 15-18,2010. Krakow, Poland.NJ:IEEE,2010:380-385.
|
| [7] |
王守信,张莉,李鹤松.一种基于云模型的主观信任评价方法[J].计算机学报,2010,21(6):1341-1352.
|
| [8] |
SUBASHINI S, KAVITHA V.A Survey on Security Issues in Service Delivery Models of Cloud Computing[J].Journal of Network and Computer Applications, 2011, 34(1):1-11.
|
| [9] |
SALEH A S, HAMED E, HASHEM M.Building Trust Management Model for Cloud Computing[C]//ICSAI.International Conference on Informatics&Systems,November 15,2014. Shanghai, China.NJ:IEEE ,2014:116-125.
|
| [10] |
陈亚睿,田立勤,杨扬.云计算环境下基于动态博弈论的用户行为模型与分析[J].电子学报, 2011, 39(8):1818-1923.
|
| [11] |
MANSHAEI M H, ZHU Q, ALPCAN T, et al.Game Theory Meets Network Security and Privacy[J].ACM Computing Surveys (CSUR), 2013, 45(3):25-43.
|
| [12] |
XIONG Li, LIU Ling.Peertrust:Supporting Reputation-based Trust for Peer-to-Peer Electronic Communities[J].IEEE Transactions on Knowledge, 2004,16(7):843-857.
|
| [13] |
ALMENAREZ F,MARIN A,CAMPO C,et al.PTM:A Pervasive Trust Management Model for Dynamic Open Environments[EB/OL].https://www.researchgate.net/publication/228772564_PTM_A_pervasive_trust_management_model_for_dynamic_open_environments,2016-05-20.
|
| [14] |
章恒,禄凯. 构建云计算环境的安全检查与评估指标体系[J]. 信息网络安全,2014(9):115-119.
|
| [15] |
SHAIKH R,SASIKUMAR M .Trust Model for Measuring Security Strength of Cloud Computing Service[J].Procedia Computer Science,2015(45):380-389.
|
| [16] |
马威,韩臻,成阳. 可信云计算中的多级管理机制研究[J]. 信息网络安全,2015(7):20-25.
|
| [17] |
谢晓兰,刘亮,赵鹏.面向云计算基于双层激励和欺骗检测的信任模型[J].电子与信息学报,2012,34(4):812-817.
|
| [18] |
廖子渊,陈明志,邓辉. 基于评价可信度的云计算信任管理模型研究[J]. 信息网络安全,2016(2):33-39.
|