Netinfo Security ›› 2015, Vol. 15 ›› Issue (9): 249-252.doi: 10.3969/j.issn.1671-1122.2015.09.055
• Orginal Article • Previous Articles Next Articles
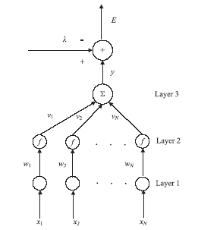
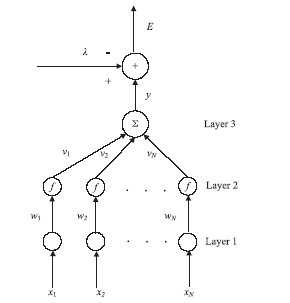
Research and Applications on Detector Generation Algorithm Based on Neural Networks
- Hunan First Normal University, Changsha Hunan 410205, China
-
Received:2015-07-15Online:2015-09-01Published:2015-11-13
CLC Number:
Cite this article
Hai-bo WU. Research and Applications on Detector Generation Algorithm Based on Neural Networks[J]. Netinfo Security, 2015, 15(9): 249-252.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2015.09.055
| [1] | KIM J, BENTLEY P J.The human immune system and network intrusion detection[C]//Proceedings of the 7th European Congress on Intelligent Techniques and Soft Computing. Aachen, Germany: EUFIT, 1999: 1120-1125. |
| [2] | 姚洪磊,张彦. 基于BP神经网络的铁路互联网售票系统信息安全评估方法[J]. 信息网络安全,2014,(7):81-86. |
| [3] | 刘锦伟,唐俊. 一种改进的实值负选择算法[J]. 计算机工程,2011,37(14):201-202. |
| [4] | 张凤斌,王天博. 实值n维混沌映射否定选择算法[J]. 计算机研究与发展,2013,50(7):1387-1398. |
| [5] | 陈文,李涛,刘晓洁,等. 一种基于自体集层次聚类的否定选择算法[J]. 中国科学:信息科学,2013,43(5):611-625. |
| [6] | 刘恩海,宋瑞平,樊世燕. 否定选择算法中高性能检测器的生成[J]. 计算机工程与设计,2014,35(8):2773-2777. |
| [7] | 杨韬,邓红莉. 一种使用最近邻自体耐受的否定选择算法[J]. 数字技术与应用,2014,(12):126-127. |
| [8] | 文天柱,许爱强,邓露. 可拓否定选择算法及其在故障诊断中的应用研究[J]. 智能系统学报,2015,7(3):1-5. |
| [9] | 史乐,柏文阳. 新的否定选择算法及其在疾病诊断中的应用[J]. 计算机科学与探索,2015,9(1):36-42. |
| [10] | FORREST S, PERELSON A S, ALL L, et a1. Self_nonself discrimination in a computer[C]//Process of IEEE Symposium on Research in Security and Privacy. Oakland, CA: IEEE Press, 1994: 202-212. |
| [11] | 何鹏程,方勇. 一种基于Web日志和网站参数的入侵检测和风险评估模型的研究[J]. 信息网络安全,2015,(1):61-65. |
| [12] | 张玲. 基于粗糙集与人工免疫的入侵检测模型研究[D]. 北京:北京邮电大学,2014. |
| [13] | 杨雅辉,黄海珍,沈晴霓,等. 基于增量式GHSOM神经网络模型的入侵检测研究[J]. 计算机学报,2014,37(5):1216-1224. |
| [14] | 王景中,徐友强. 基于RBF神经网络的HTTP异常行为自动识别方法[J]. 信息网络安全,2014,(12):16-20. |
| [15] | GAO X Z, OVASKA S J, WANG X, et al.A Neural Networks-based Negative Selection Algorithm in Fault Diagnosis[J]. Neural Comput & Applic, 2008, (17): 91-98. |
| [16] | 李晨光. 基于神经网络的入侵检测技术研究与应用[D]. 长春:吉林大学,2013. |
| [17] | 段新东,林玉香,张鑫. 基于智能化自学习方式的入侵检测防护系统设计与实现[J]. 信息网络安全,2014,(2):20-26. |
| [18] | Kim J, Bentley P J, Aickelin U, et al.Immune system approaches to intrusion detection—a review[C]//Proceedings of the 3rd International Conference on Articial Immune Systems. Catania, Australia: Kluwer Academic Publishers, 2004: 316-329. |
| [19] | Lincoln Laboratory. Information Systems Technology[EB/OL]. . |
| [20] | 汤健,孙春来,李东. 基于在线集成学习技术的工业控制网络入侵防范技术探讨[J]. 信息网络安全,2014,(9):86-91. |
| [1] | Zhiyan ZHAO, Xiaomo JI. Research on the Intelligent Fusion Model of Network Security Situation Awareness [J]. Netinfo Security, 2020, 20(4): 87-93. |
| [2] | Min LIU, Shuhui CHEN. Research on VoLTE Traffic Based on Association Fusion [J]. Netinfo Security, 2020, 20(4): 81-86. |
| [3] | Lingyu BIAN, Linlin ZHANG, Kai ZHAO, Fei SHI. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [4] | Yifeng DU, Yuanbo GUO. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [5] | Zhizhou FU, Liming WANG, Ding TANG, Shuguang ZHANG. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [6] | Rong WANG, Chunguang MA, Peng WU. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [7] | Xiaoli DONG, Shuai SHANG, Jie CHEN. Impossible Differential Attacks on 9-Round Block Cipher Rijndael-192 [J]. Netinfo Security, 2020, 20(4): 40-46. |
| [8] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | Lu CHEN, Yajie SUN, Liqiang ZHANG, Yun CHEN. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [10] | Jinfang JIANG, Guangjie HAN. Survey of Trust Management Mechanism in Wireless Sensor Network [J]. Netinfo Security, 2020, 20(4): 12-20. |
| [11] | Jianwei LIU, Yiran HAN, Bin LIU, Beiyuan YU. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [12] | Peng LIU, Qian HE, Wangyang LIU, Xu CHENG. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [13] | Yubo SONG, Ming FAN, Junjie YANG, Aiqun HU. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis [J]. Netinfo Security, 2020, 20(3): 9-17. |
| [14] | Tengfei WANG, Manchun CAI, Tianliang LU, Ting YUE. IPv6 Network Attack Source Tracing Method Based on iTrace_v6 [J]. Netinfo Security, 2020, 20(3): 83-89. |
| [15] | Yi ZHANG, Hongyan LIU, Hequn XIAN, Chengliang TIAN. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||