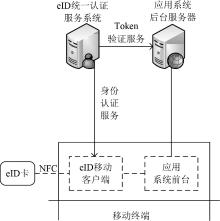
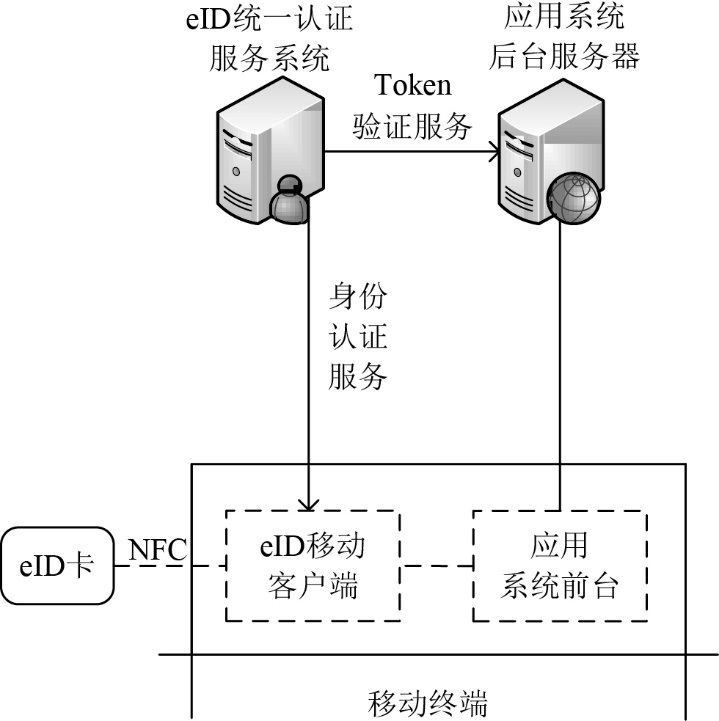
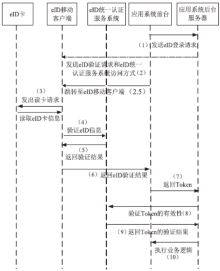
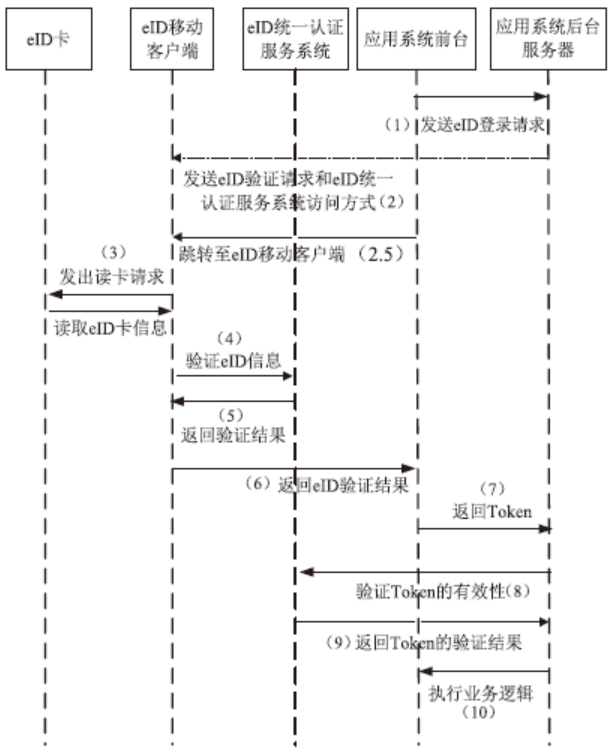
| [1] |
郭晓彪,曾志,顾力平. 电子身份认证技术应用研究[J]. 信息网络安全,2011,(3):21-22.
|
| [2] |
De Cock D, Wolf C, Preneel B.The Belgian Electronic Identity Card (Overview)[C]//Sicherheit. 2006, 77: 298-301.
|
| [3] |
POLLER A, WALDMANN U, Vowé S, et al.Electronic identity cards for user authentication-promise and practice[J]. IEEE Security & Privacy, 2012, 10(1): 46-54.
|
| [4] |
ESSBACH J.An approach to a decentral mobile payment system using nfc and the german eid-card[C]//Wireless Systems (IDAACS-SWS), 2012 IEEE 1st International Symposium on, IEEE, 2012: 67-71.
|
| [5] |
HORSCH M, STOPCZYNSKI M. The German eCard-Strategy[EB/OL]. .
|
| [6] |
ZWATTENDORFER B, TAUBER A.Secure cloud authentication using eIDs[C]//Cloud Computing and Intelligent Systems (CCIS), 2012 IEEE 2nd International Conference on, 2012, 397, 401.
|
| [7] |
BRUEGGER B P, Hühnlein D, KREUTZER M.Towards global eID-interoperability[C]//BIOSIG, 2007: 127-140.
|
| [8] |
KOSTAKOS V, O'Neill E. NFC on Mobile Phones: Issues, Lessons and Future Research[C]//PerCom Workshops, 2007, 8.
|
| [9] |
MICHAHELLES F, THIESSE F, SCHMIDT A, et al.Pervasive RFID and near field communication technology[J]. Pervasive Computing, IEEE, 2007, 6(3): 94-96, c3.
|
| [10] |
CCURRAN K, MILLAR A, MC G C.Near field communication[J]. International Journal of Electrical and Computer Engineering (IJECE), 2012, 2(3): 371-382.
|
| [11] |
ÖZDENIZCI B, AYDIN M, COSKUN V, et al.NFC research framework: a literature review and future research directions[C]//Published in 14th IBIMA Conference, 2010: 23-24.
|
| [12] |
MATINMIKKO T, Ylisaukko-Oja A, STROMMER E, et al. Physical browsing with NFC technology[EB/OL]. .
|
| [13] |
王景中,凌晨. 基于节点认证的物联网感知层信息安全传输机制的研究[J]. 信息网络安全,2014,(2):53-57.
|
| [14] |
刘劲彤,吴勇. 欧盟eID项目与面向未来的身份服务战略[J]. 信息安全与通信保密,2012,(11):124-127.
|
| [15] |
夏戈明,史立哲,周文,等. 轻量级RFID双向通信认证协议优化方案[J]. 信息网络安全,2014,(2):58-62.
|
| [16] |
袁艳祥,游林. 基于身份加密的可认证密钥协商协议[J]. 信息网络安全,2014,(3):1-6.
|
| [17] |
张越今. 我国互联网电子身份证体系机制研究[J]. 中国人民公安大学学报:自然科学版,2013,(1):84-86.
|
| [18] |
李珊珊,周爽,蒋天发. 一种分块压缩感知观测值的图像篡改认证算法[J]. 信息网络安全,2014,(4):35-39.
|
| [19] |
王毓娜,吕秋云. 基于生物识别的网络身份认证新方案[J]. 信息网络安全,2014,(8):1-5.
|
| [20] |
郑志蓉,刘毅. 虚拟计算平台远程可信认证技术研究[J]. 信息网络安全,2014,(10):77-80.
|
| [21] |
黄丰凡,崔海利. eID与RFID技术对比分析[J]. 电信技术,2013,(5):20-21.
|
| [22] |
张平,陈长松,胡红钢. 基于分组密码的认证加密工作模式[J]. 信息网络安全,2014,(11):8-17.
|
 ), XU Jin1,2, GAO Yu-tong3
), XU Jin1,2, GAO Yu-tong3