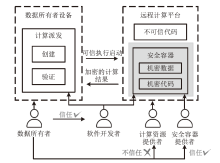
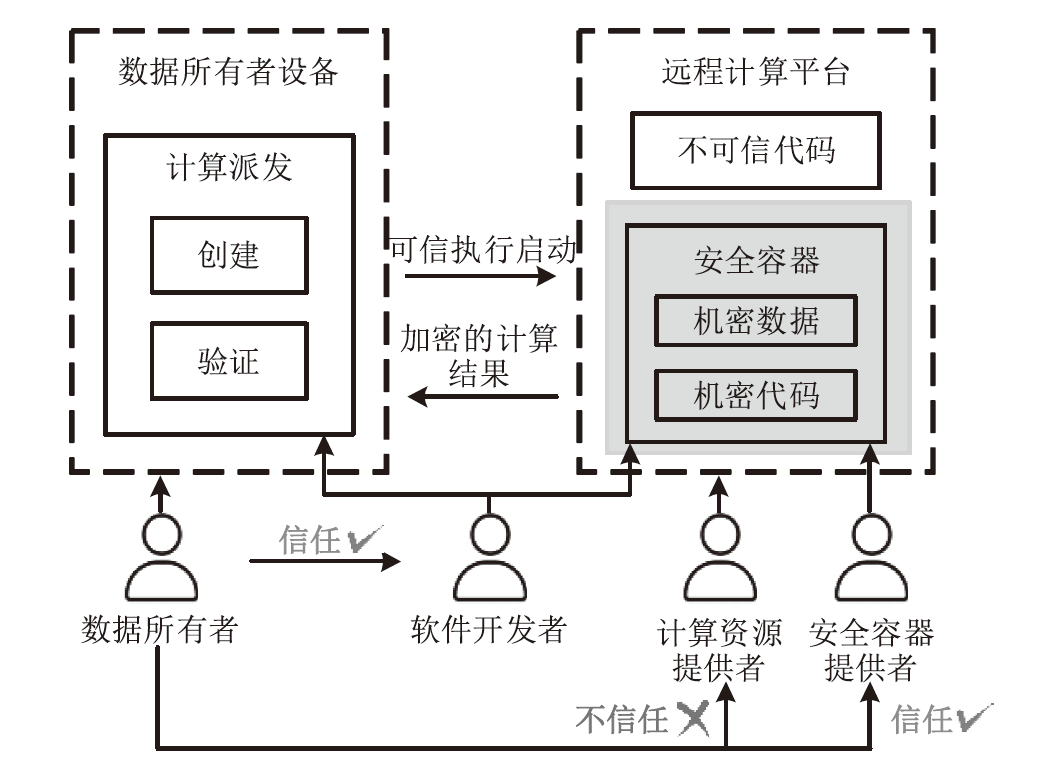
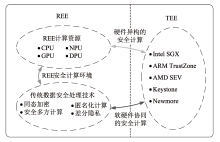
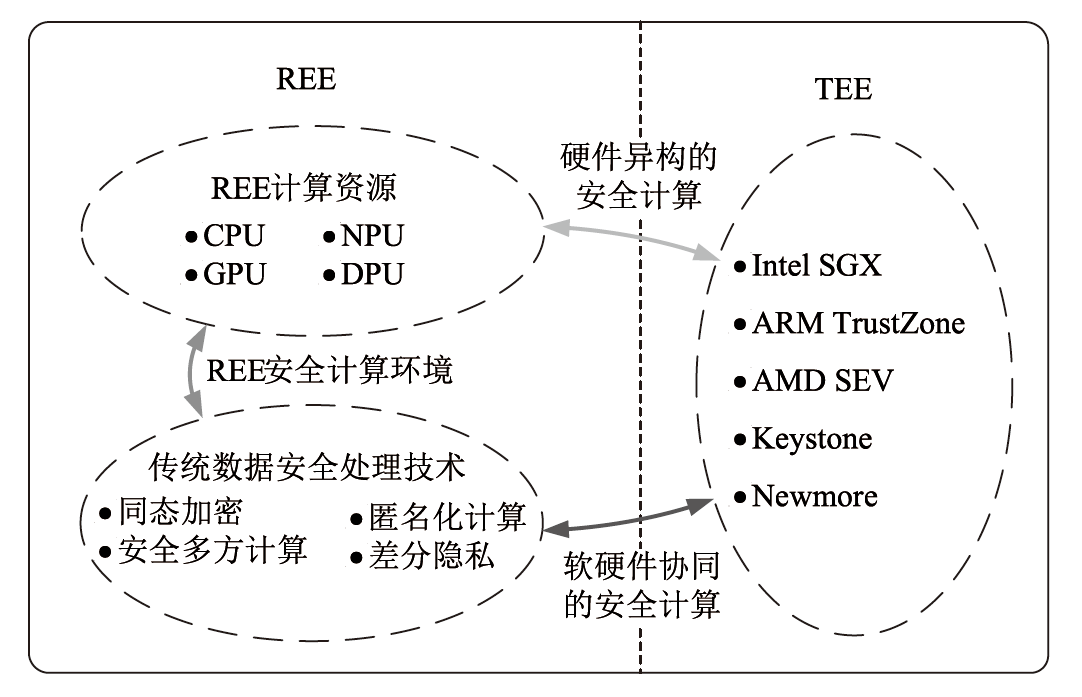
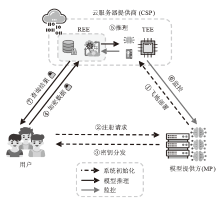
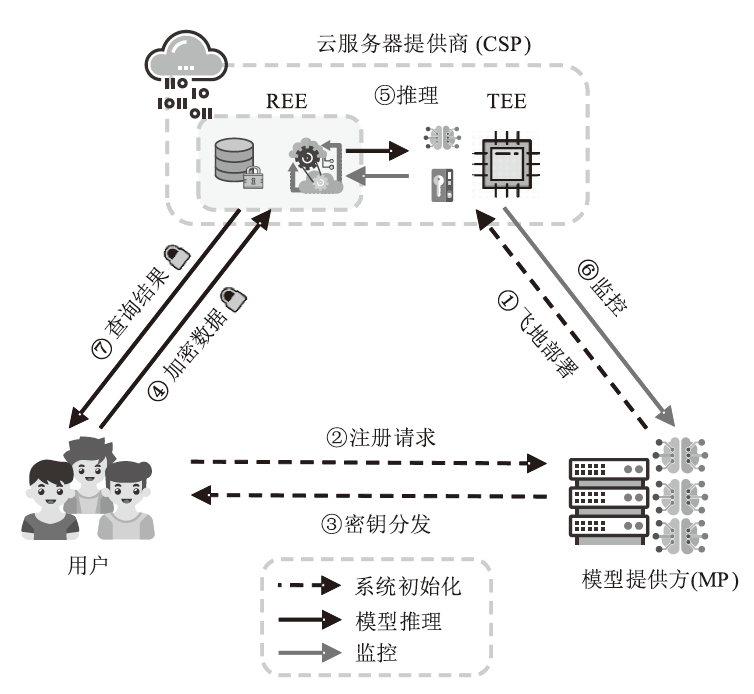
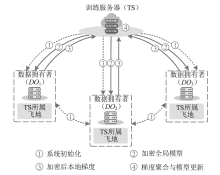
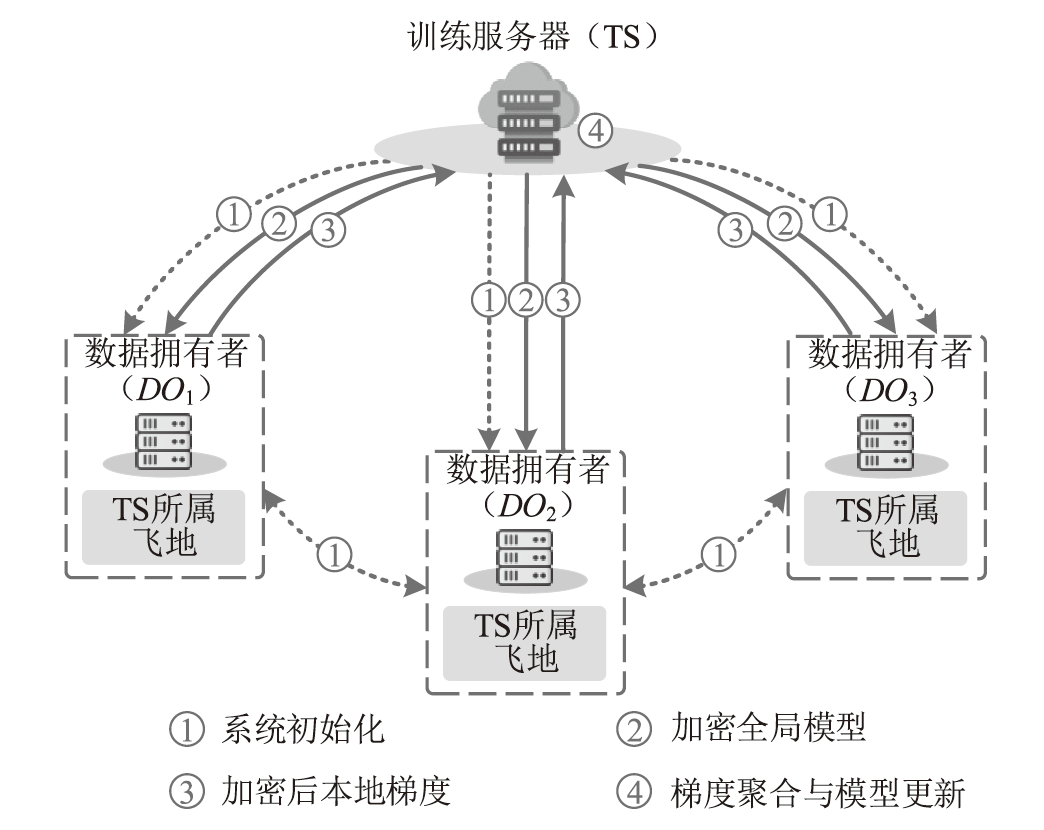
信息网络安全 ›› 2025, Vol. 25 ›› Issue (11): 1643-1657.doi: 10.3969/j.issn.1671-1122.2025.11.001
融合机密计算的数据安全处理研究进展
西安电子科技大学网络与信息安全学院 西安 710126
-
收稿日期:2025-05-25出版日期:2025-11-10发布日期:2025-12-02 -
通讯作者:朱辉zhuhui@xidian.edu.cn -
作者简介:朱辉(1981—),男,河南,教授,博士,主要研究方向为数据安全、隐私保护和应用密码学|方云依(1995—),女,浙江,博士研究生,主要研究方向为机密计算、数据安全与隐私保护|王枫为(1993—),男,河南,副教授,博士,主要研究方向为数据安全与隐私保护|许伟(1999—),男,湖南,博士研究生,主要研究方向为联邦学习、隐私推理 -
基金资助:国家重点研发计划(2022YFB4501500);国家重点研发计划(2022YFB4501501);国家自然科学基金(U22B2030);国家自然科学基金(62302360);国家自然科学基金(62572376);陕西省重点研发计划(2024SF2-GJHX-37)
Research Progress on Data Security Processing Integrating Confidential Computing
ZHU Hui( ), FANG Yunyi, WANG Fengwei, XU Wei
), FANG Yunyi, WANG Fengwei, XU Wei
School of Cyber Engineering ,Xidian University Xi’an 710126, China
-
Received:2025-05-25Online:2025-11-10Published:2025-12-02
摘要:
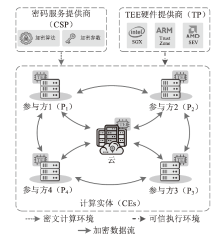
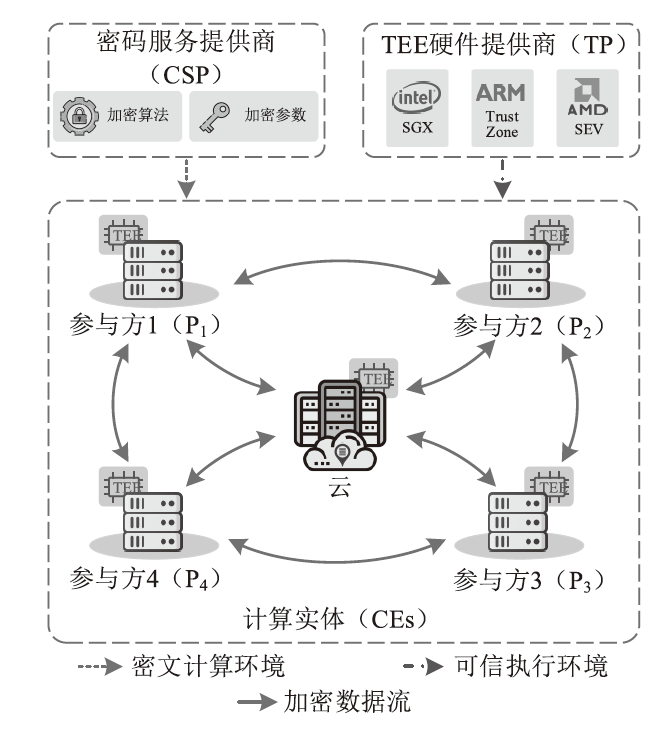
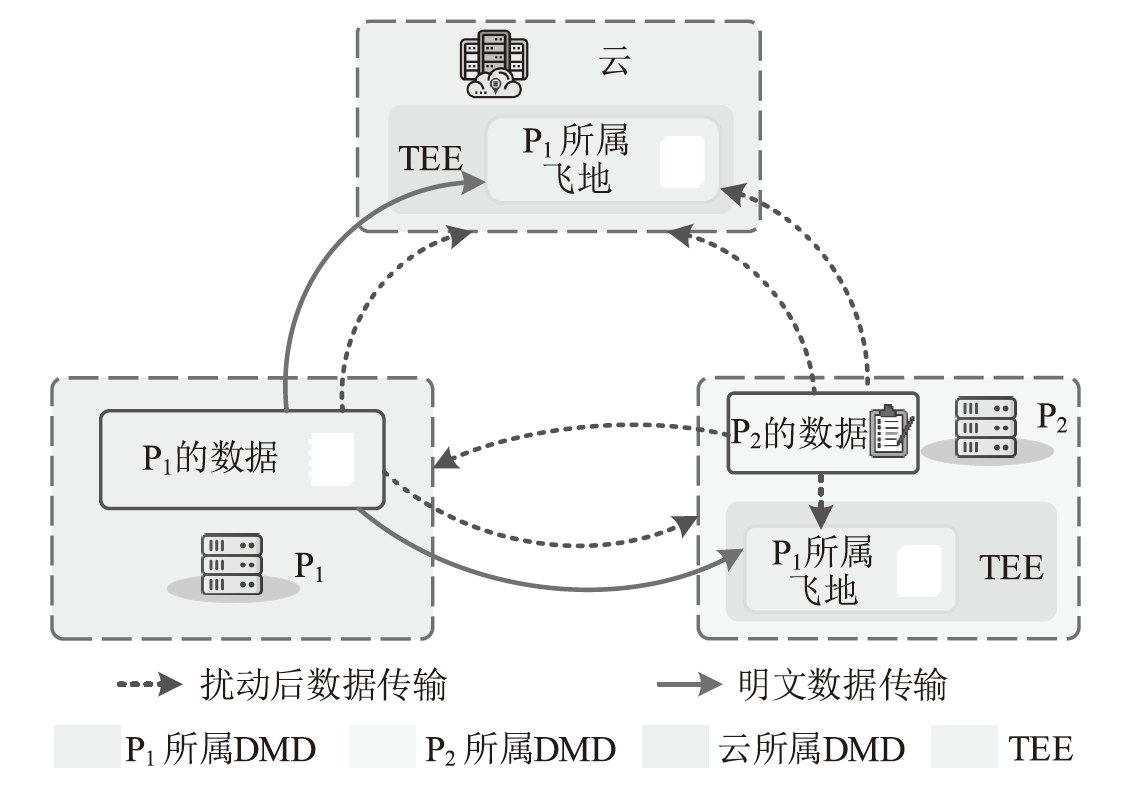
在数据要素、数据安全、法律法规、隐私保护等多种因素的作用下,数据安全处理逐渐成为未来数据的主要利用方式。安全多方计算、密码学、匿名化和差分隐私技术是现有数据安全处理方案构造的基石。然而,安全多方计算协议通常需要各计算参与方之间进行多轮交互以完成固定运算,带来较大的通信开销;密码学技术在性能和功能上存在短板;匿名化和差分隐私技术会对原始数据进行泛化、加扰等处理,使数据的可用性下降。为解决上述问题,将可信执行环境(TEE)与传统数据安全处理技术进行结合,成为了当前学术界和工业界的研究热点。文章从研究背景与发展现状、代表性工作进展等方面对现有TEE与数据安全处理融合的方案进行了分析,在此基础上,提出了TEE与密态计算融合的安全模型,并对未来的发展趋势进行了展望和总结。
中图分类号:
引用本文
朱辉, 方云依, 王枫为, 许伟. 融合机密计算的数据安全处理研究进展[J]. 信息网络安全, 2025, 25(11): 1643-1657.
ZHU Hui, FANG Yunyi, WANG Fengwei, XU Wei. Research Progress on Data Security Processing Integrating Confidential Computing[J]. Netinfo Security, 2025, 25(11): 1643-1657.
| [1] | TU Chunxia. Survey on Homomorphic Encryption Technology[C]// Atlantis Press. The 8th International Conference on Social Network, Communication and Education (SNCE 2018). Atlantis: Atlantis Press, 2018: 764-768. |
| [2] |
ZHAO Chuan, ZHAO Shengnan, ZHAO Minghao, et al. Secure Multi-Party Computation: Theory, Practice and Applications[J]. Information Sciences, 2019, 476: 357-372.
doi: 10.1016/j.ins.2018.10.024 |
| [3] | SAMARATI P, SWEENEY L. Generalizing Data to Provide Anonymity When Disclosing Information[C]// ACM. ACM SIGMOD Symposium on Principles of Database Systems, 1998: 188-201. |
| [4] | DWORK C. Differential Privacy: A Survey of Results[C]// Springer. International Conference on Theory and Applications of Models of Computation. Heidelburg:Springer, 2008: 1-19. |
| [5] | RIVEST R L, ADLEMAN L, DERTOUZOS M L. On Data Banks and Privacy Homomorphisms[J]. Foundations of Secure Computation, 1978, 4(11): 169-180. |
| [6] | YAO A. Protocols for Secure Computations[C]// IEEE. The 23rd Annual Symposium on Foundations of Computer Science (SFCS 1982). New York: IEEE, 1982: 160-164. |
| [7] | VOLOS S, VASWANI K, BRUNO R. Graviton: Trusted Execution Environments on GPUs[C]// USENIX. The 13th USENIX Symposium on Operating Systems Design and Implementation (OSDI 18). Berkeley: USENIX, 2018: 681-696. |
| [8] | JANG I, TANG A, KIM T, et al. Heterogeneous Isolated Execution for Commodity GPUS[C]// ACM. Proceedings of the 24th International Conference on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 2019: 455-468. |
| [9] | ZHU Jianping, HOU Rui, WANG Xiaofeng, et al. Enabling Rack-Scale Confidential Computing Using Heterogeneous Trusted Execution Environment[C]// IEEE. 2020 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2020: 1450-1465. |
| [10] | FISCH B, VINAYAGAMURTHY D, BONEH D, et al. Iron: Functional Encryption Using Intel SGX[C]// ACM.The 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 765-782. |
| [11] | TAKESHITA J, MCKECHNEY C, PAJAK J, et al. GPS: Integration of Graphene, Palisade, and SGX for Large-Scale Aggregations of Distributed Data[J]. Cryptology ePrint Archive, 2021: 1-21. |
| [12] | OUYANG Wenyi, WANG Qiongxiao, WANG Wei, et al. SCB: Flexible and Efficient Asymmetric Computations Utilizing Symmetric Cryptosystems Implemented with Intel SGX, International Performance[C]// IEEE. Computing, and Communications Conference. New York: IEEE, 2021: 1-8. |
| [13] | WANG Wenhao, JIANG Yichen, SHEN Qintao, et al. Toward Scalable Fully Homomorphic Encryption through Light Trusted Computing Assistance[EB/OL]. (2019-05-19)[2025-04-27]. https://arxiv.org/abs/1905.07766. |
| [14] | WANG Qifan, ZHOU Lei, BAI Jianli, et al. HT2ML: An Efficient Hybrid Framework for Privacy-Preserving MacHine Learning Using HE and TEE[J]. Computers & Security, 2023, 135(103509): 1-12. |
| [15] |
COPPOLINO L, D’ANTONIO S, FORMICOLA V, et al. Vise: Combining Intel SGX and Homomorphic Encryption for Cloud Industrial Control Systems[J]. IEEE Transactions on Computers, 2022, 70(5): 711-724.
doi: 10.1109/TC.2020.2995638 URL |
| [16] | WU Pengfei, NING Jiating, SHEN Jiamin, et al. Hybrid Trust Multi-Party Computation with Trusted Execution Environment[C]// Internet Society. Network and Distributed System Security Symposium (NDSS 2022). San Diego: Internet Society, 2022: 1-18. |
| [17] |
FAN Yongkai, LIN Xiaodong, LIANG Wei, et al. A Secure Privacy Preserving Deduplication Scheme for Cloud Computing[J]. Future Generation Computer Systems, 2019, 101: 127-135.
doi: 10.1016/j.future.2019.04.046 |
| [18] | LU Yibiao, ZHANG Bingsheng, ZHOU Hongsheng, et al. Correlated Randomness Teleportation via Semi-Trusted Hardware—Enabling Silent Multi-Party Computation[C]// Springer. European Symposium on Research in Computer Security. Heidelburg: Springer, 2021: 699-720. |
| [19] | CHOI J I, TIAN D, HERNANDEZ G, et al. a Hybrid Approach to Secure Function Evaluation Using SGX[C]// ACM. The 2019 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2019: 100-113. |
| [20] | ZHOU Xing, XU Zhilei, WANG Cong, et al. PPMLAC: High Performance Chipset Architecture for Secure Multi-Party Computation[C]// ACM. The 49th Annual International Symposium on Computer Architecture, New York: ACM, 2022: 87-101. |
| [21] |
WEI Tao, PAN Wuqiong, LI Tingting, et al. Trusted-Environment-Based Privacy Preserving Computing: Breaks the Bottleneck of Ciphertext-Exchange Era[J]. Information and Communications Technology and Policy, 2022, 48(5): 15-24.
doi: 10.12267/j.issn.2096-5931.2022.05.003 |
|
韦韬, 潘无穷, 李婷婷, 等. 可信隐私计算:破解数据密态时代“技术困局”[J]. 信息通信技术与政策, 2022, 48(5): 15-24.
doi: 10.12267/j.issn.2096-5931.2022.05.003 |
|
| [22] | DONG Wentao, WANG Cong. Poster: Towards Lightweight TEE-Assisted MPC[C]// ACM.The 2023 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2023: 3609-3611. |
| [23] | HU Xuanwei, LI Rujia, LIU Yi, et al. Towards Efficient and Practical Multi-Party Computation under Inconsistent Trust in TEEs[C]// IEEE.2025 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2025: 2885-2902. |
| [24] | FUHRY B, BAHMANI R, BRASSER F, et al. HardIDX: Practical and Secure Index with SGX[C]// Springer. IFIP Annual Conference on Data and Applications Security and Privacy. Heidelburg: Springer, 2017: 386-408. |
| [25] | MISHRA P, PODDAR R, CHEN J, et al. Oblix: An Efficient Oblivious Search Index[C]// IEEE. 2018 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2018: 279-296. |
| [26] | SUN Wenhai, ZHANG Ruide, LOU Wenjing, et al. Rearguard: Secure Keyword Search Using Trusted Hardware[C]// IEEE. IEEE Conference on Computer Communications (INFOCOM). New York: IEEE, 2018: 801-809. |
| [27] |
JIANG Qin, CHANG E C, QI Yong, et al. Rphx: Result Pattern Hiding Conjunctive Query over Private Compressed Index Using Intel SGX[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 1053-1068.
doi: 10.1109/TIFS.2022.3144877 URL |
| [28] |
ZHENG Yandong, ZHU Hui, LU Rongxing, et al. Secure Similarity Queries over Vertically Distributed Data via TEE-Enhanced Cloud Computing[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 6237-6251.
doi: 10.1109/TIFS.2024.3413630 URL |
| [29] |
YANG Xinying, YUE Cong, ZHANG Wenhui, et al. SecuDB: An In-Enclave Privacy-Preserving and Tamper-Resistant Relational Database[J]. Proceedings of the VLDB Endowment, 2024, 17(12): 3906-3919.
doi: 10.14778/3685800.3685815 URL |
| [30] |
LU Di, SHI Minqiang, MA Xindi, et al. Smaug: A TEE-Assisted Secured SQLite for Embedded Systems[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(5): 3617-3635.
doi: 10.1109/TDSC.2022.3216020 URL |
| [31] | NATARAJAN D, LOVELESS A, DAI Wei, et al. Chex-Mix: Combining Homomorphic Encryption with Trusted Execution Environments for Two-Party Oblivious Inference in the Cloud[EB/OL]. (2021)[2025-04-27]. https://eprint.iacr.org/2021/1603. |
| [32] |
LI Tong, LI Xuan, ZHONG Xingyi, et al. Communication-Efficient Outsourced Privacy-Preserving Classification Service Using Trusted Processor[J]. Information Sciences, 2019, 505: 473-486.
doi: 10.1016/j.ins.2019.07.047 |
| [33] | CHEN Huili, FU Cheng, ROUHANI B D, et al. Deepattest: An End-to-End Attestation Framework for Deep Neural Networks[C]// IEEE. 2019 ACM/IEEE 46th Annual International Symposium on Computer Architecture (ISCA). New York: IEEE, 2019: 487-498. |
| [34] | LEE T, LIN Zhiqi, PUSHP S, et al. Occlumency: Privacy-Preserving Remote Deep-Learning Inference Using SGX[C]// ACM. The 25th Annual International Conference on Mobile Computing and Networking (MobiCom 2019). New York: ACM, 2019: 1-17. |
| [35] | BIAN Song, JIANG Weiwen, SATO T. Privacy-Preserving Medical Image Segmentation via Hybrid Trusted Execution Environment[C]// IEEE. 2021 58th ACM/IEEE Design Automation Conference (DAC). New York: IEEE, 2021: 1347-1350. |
| [36] | XIAO Huizi, ZHANG Qingyang, PEI Qingqi, et al. Privacy-Preserving Neural Network Inference Framework via Homomorphic Encryption and SGX[C]// IEEE.2021 IEEE 41st International Conference on Distributed Computing Systems (ICDCS). New York: IEEE, 2021: 751-761. |
| [37] | ZHANG Zheng, WANG Na, ZHANG Ziqi, et al. Groupcover:A Secure, Efficient and Scalable Inference Framework for On-Device Model Protection Based on TEEs[C]// International Machine Learning Society (IMLS). The 41st International Conference on Machine Learning. MA: Journal of Machine Learning Research (JMLR), 2024: 1-12. |
| [38] |
XU Hongjian, LIAO Longlong, LIU Xinqi, et al. Fault-Tolerant Deep Learning Inference on CPU-GPU Integrated Edge Devices with TEEs[J]. Future Generation Computer Systems, 2024, 161: 404-414.
doi: 10.1016/j.future.2024.07.027 URL |
| [39] |
JIAN Zhaolong, LIU Xu, DONG Qiankun, et al. SmartZone: Runtime Support for Secure and Efficient On-Device Inference on ARM TrustZone[J]. IEEE Transactions on Computers, 2025, 74(6): 2144-2158.
doi: 10.1109/TC.2025.3557971 URL |
| [40] | ZHANG Chengliang, XIA Junzhe, YANG Baichen, et al. Citadel: Protecting Data Privacy and Model Confidentiality for Collaborative Learning[C]// ACM. The 12th ACM Symposium on Cloud Computing (SoCC 2021). New York: ACM, 2021: 546-561. |
| [41] | TRAMER F, BONEH D. Slalom: Fast, Verifiable and Private Execution of Neural Networks in Trusted Hardware[EB/OL]. (2018-06-08)[2025-04-27]. https://arxiv.org/abs/1806.03287. |
| [42] | HASHEMI H, WANG Yongqin, ANNAVARAM M. DarKnight: An Accelerated Framework for Privacy and Integrity Preserving Deep Learning Using Trusted Hardware[C]// ACM.The 54th Annual IEEE/ACM International Symposium on Microarchitecture. New York: ACM, 2021: 212-224. |
| [43] | ZHANG Xiaoli, LI Fengting, ZHANG Zeyu, et al. Enabling Execution Assurance of Federated Learning at Untrusted Participants[C]// IEEE. IEEE Conference on Computer Communications (INFOCOM). New York: IEEE, 2020: 1877-1886. |
| [44] | MO Fan, HADDADI H, KATEVAS K, et al. PPFL: Privacy-Preserving Federated Learning with Trusted Execution Environments[C]// ACM.The 19th Annual International Conference on Mobile Systems, Applications, and Services. New York: ACM, 2021: 94-108. |
| [45] | LAW A, LEUNG C, PODDAR R, et al. Secure Collaborative Training and Inference for XGBoost[C]// ACM.The 2020 Workshop on Privacy-Preserving Machine Learning in Practice. New York: ACM, 2020: 21-26. |
| [46] | MO Fan, SHAMSABADI A S, KATEVAS K, et al. DarkneTZ: Towards Model Privacy at the Edge Using Trusted Execution Environments[C]// ACM.The 18th International Conference on Mobile Systems, Applications, and Services. New York: ACM, 2020: 161-174. |
| [47] | ASVADISHIREHJINI A, KANTARCIOGLU M, MALIN B. GINN: Fast GPU-TEE Based Integrity for Neural Network Training[C]// ACM.The 12th ACM Conference on Data and Application Security and Privacy. New York: ACM, 2022: 4-15. |
| [48] | YAZDINEJAD A, DEHGHANTANHA A, SRIVASTAVA G. Ap2fl: Auditable Privacy-Preserving Federated Learning Framework for Electronics in Healthcare[J]. IEEE Transactions on Consumer Electronics, 2023: 1-9. |
| [49] |
XU Wei, ZHU Hui, ZHENG Yandong, et al. ToNN: An Oblivious Neural Network Prediction Scheme with Semi-Honest TEE[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 7335-7348.
doi: 10.1109/TIFS.2024.3435493 URL |
| [50] | WANG Fengwei, ZHU Hui, LIU Xingdong, et al. Achieving Federated Logistic Regression Training towards Model Confidentiality with Semi-Honest TEE[J]. Information Sciences, 2024, 679(121115): 1-21. |
| [1] | 郝萌, 李佳勇, 杨洪伟, 张伟哲. 异构CPU-GPU系统机密计算综述[J]. 信息网络安全, 2025, 25(11): 1658-1672. |
| [2] | 任丰原, 张馨月, 雷卓祎, 刘忻. 基于机密计算的键值数据存储与操作优化方法研究[J]. 信息网络安全, 2025, 25(11): 1707-1717. |
| [3] | 卢笛, 刘玉佳, 吕超越, 孙梦娜, 张清文, 杨力. 一种云原生TEE服务共享机制[J]. 信息网络安全, 2025, 25(11): 1774-1791. |
| [4] | 刘忻, 李韵宜, 王淼. 一种基于机密计算的联邦学习节点轻量级身份认证协议[J]. 信息网络安全, 2022, 22(7): 37-45. |
| [5] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [6] | 刘忻, 郭振斌, 宋宇宸. 一种基于SGX的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(6): 1-10. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||