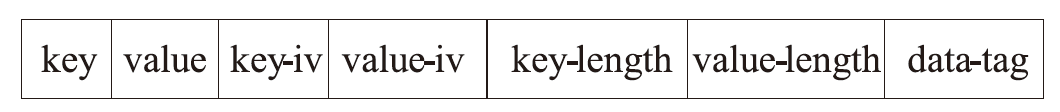信息网络安全 ›› 2025, Vol. 25 ›› Issue (11): 1707-1717.doi: 10.3969/j.issn.1671-1122.2025.11.005
基于机密计算的键值数据存储与操作优化方法研究
1.兰州大学信息科学与工程学院 兰州 730099 2.清华大学信息科学技术学院 北京 100084
-
收稿日期:2025-07-27出版日期:2025-11-10发布日期:2025-12-02 -
通讯作者:刘忻xinl@lzu.edu.cn -
作者简介:任丰原(1970—),男,甘肃,教授,博士,CCF会员,主要研究方向为系统结构、工业互联网|张馨月(2006—),女,甘肃,本科,主要研究方向为机密计算|雷卓祎(2002—),男,山西,硕士研究生,主要研究方向为机密计算|刘忻(1988—),男,甘肃,副教授,博士,CCF会员,主要研究方向为机密计算、人工智能 -
基金资助:国家自然科学基金(62132007);甘肃省重点研发计划(23YFGA0010)
Research on Key-Value Data Storage and Operation Optimization Method Based on Confidential Computing
REN Fengyuan1,2, ZHANG Xinyue1, LEI Zhuoyi1, LIU Xin1( )
)
1. School of Information Science & Engineering ,Lanzhou University Lanzhou 730099, China 2. School of Information Science and Technology ,Tsinghua University Beijing 100084, China
-
Received:2025-07-27Online:2025-11-10Published:2025-12-02
摘要:
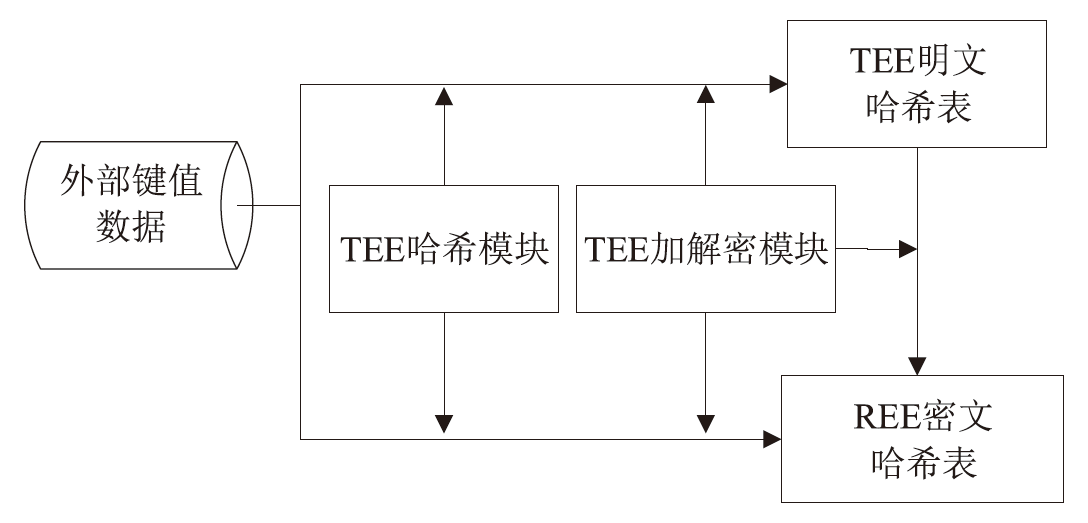
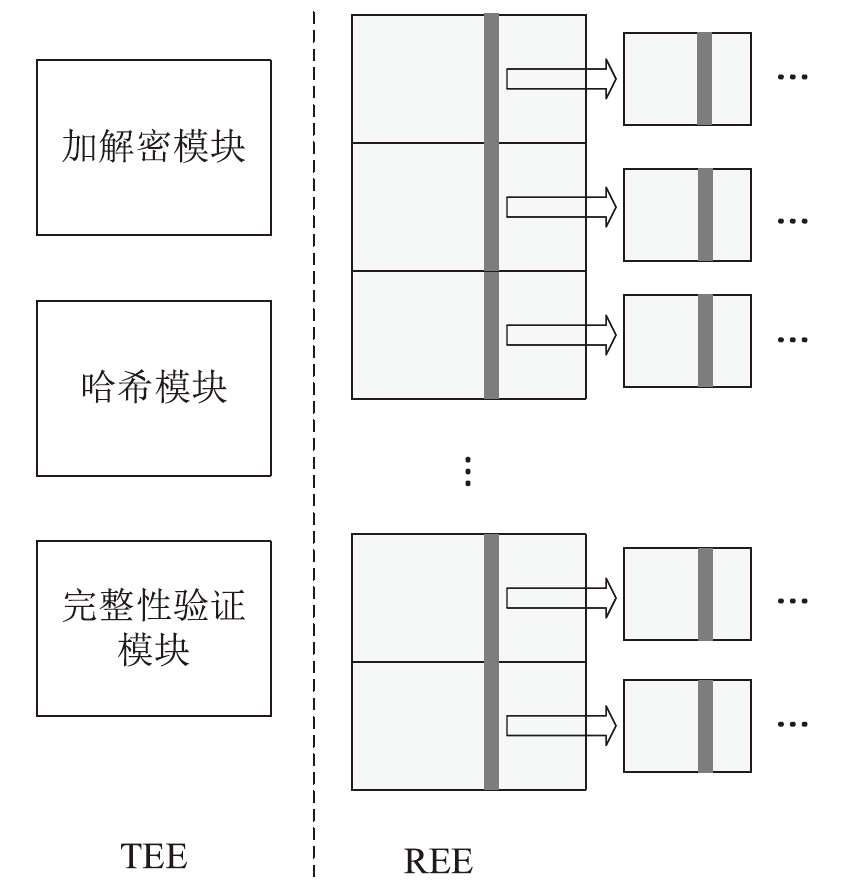
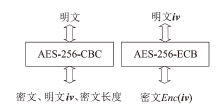
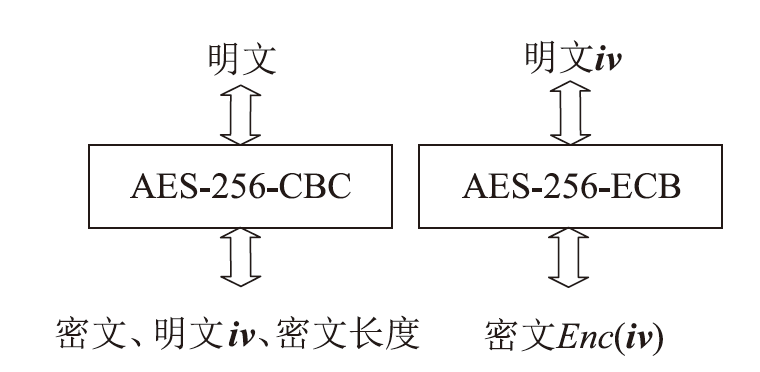
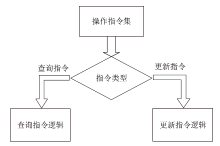
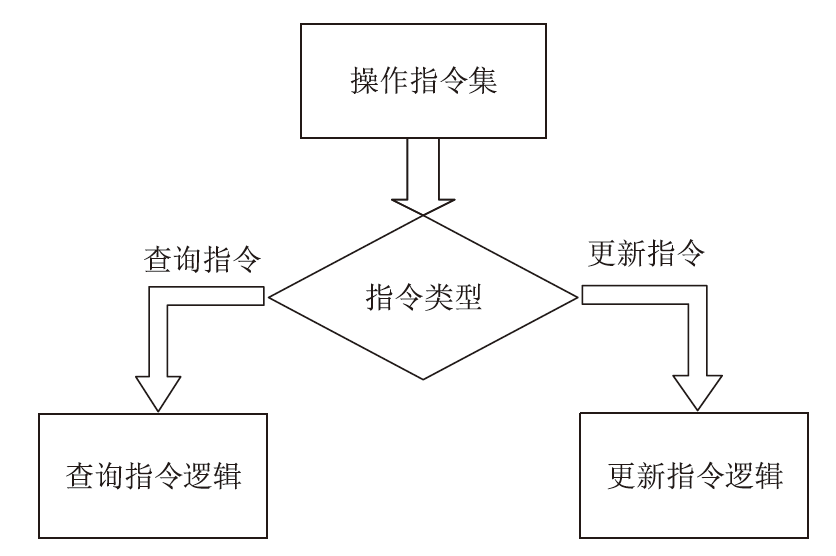
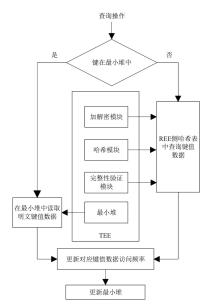
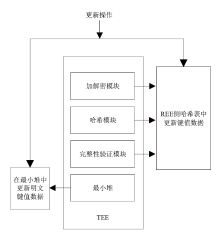
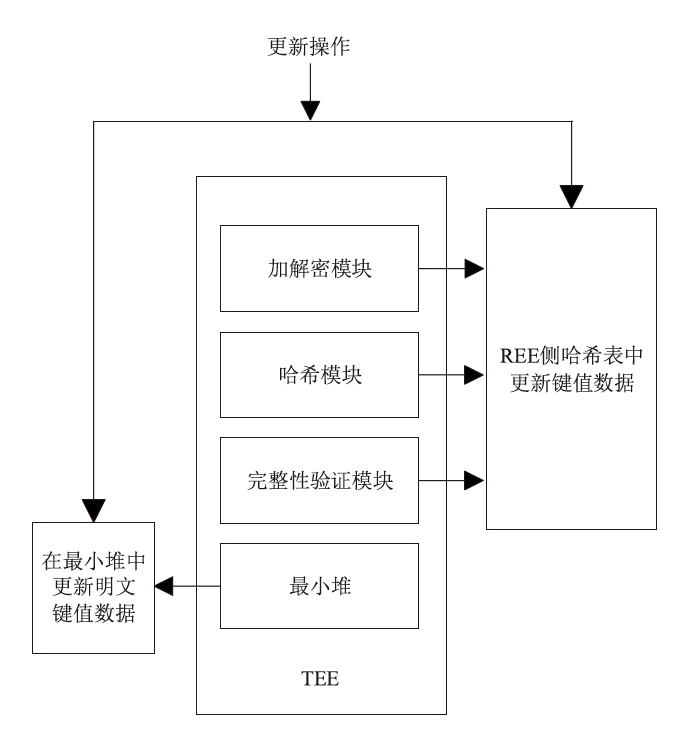
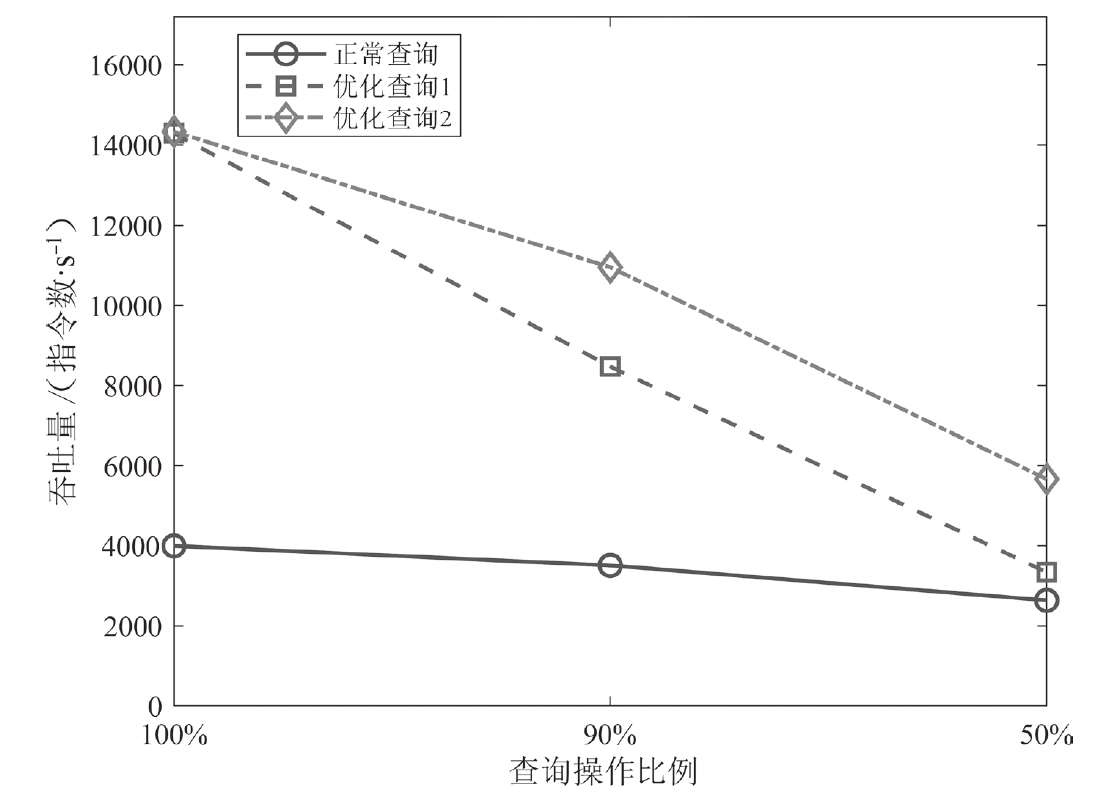
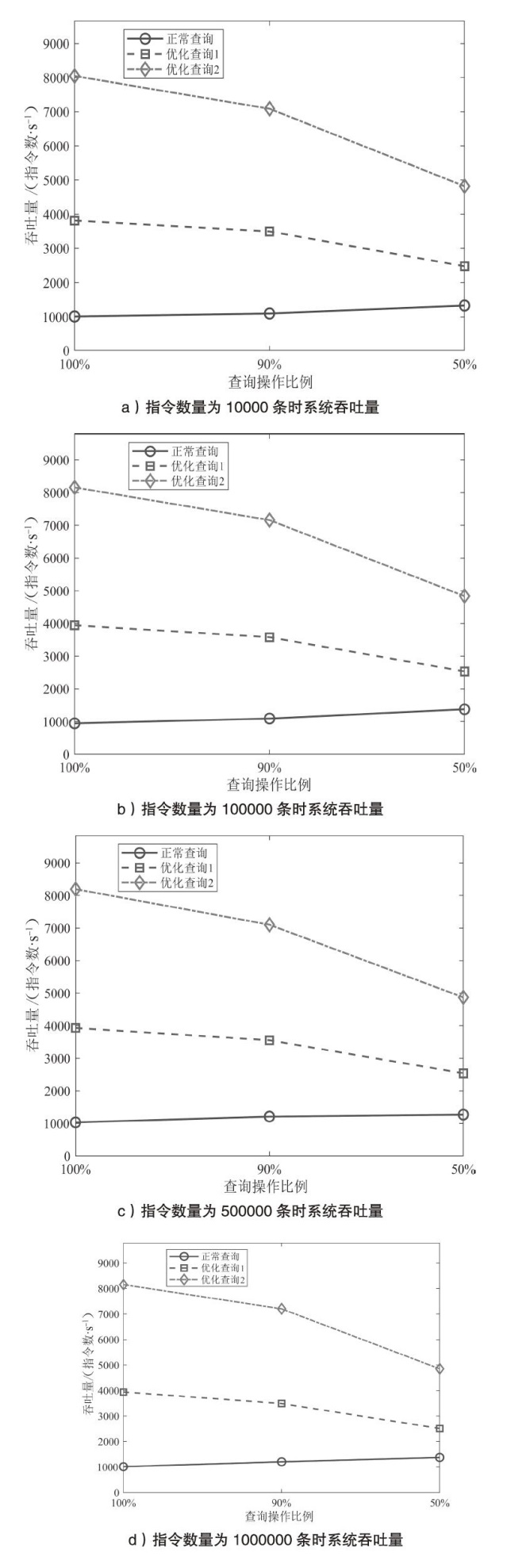
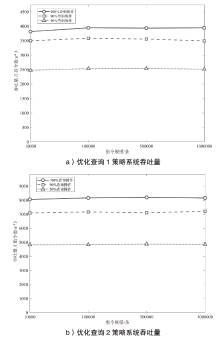
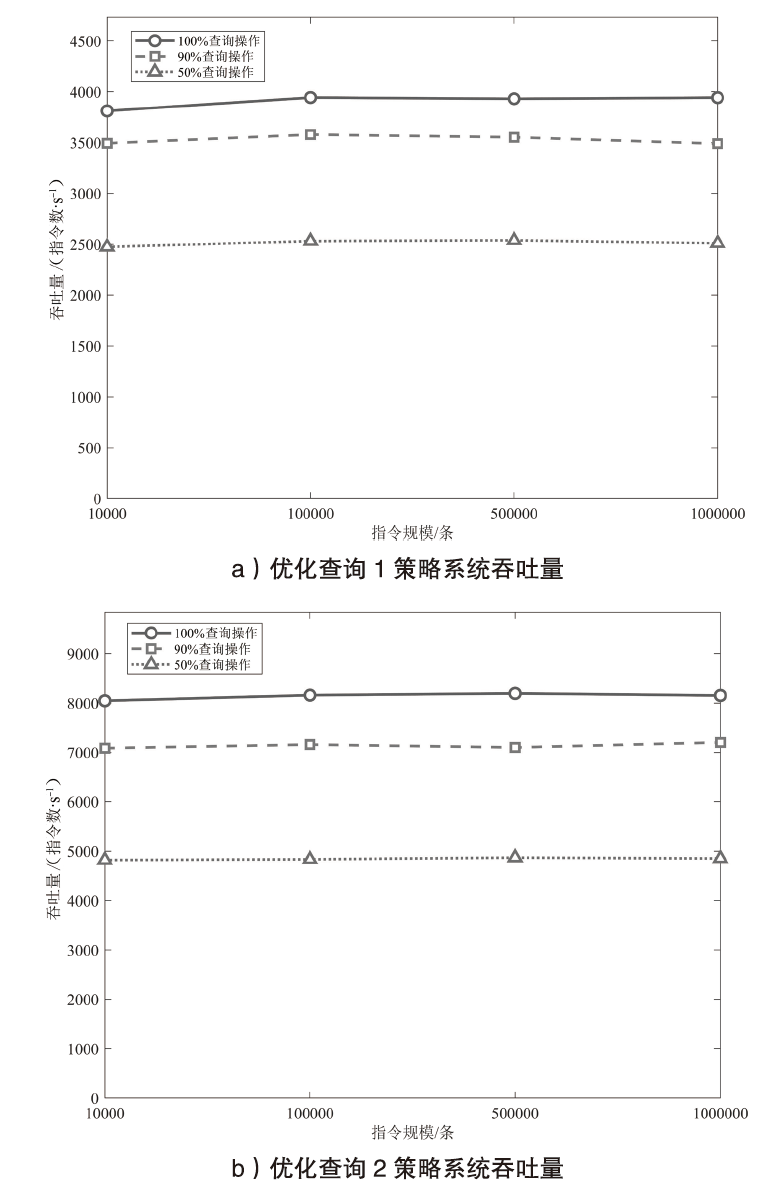
机密计算旨在保护正在使用中的数据,基于硬件的TEE可使受保护的数据无法被主内存中的应用程序访问。为优化机密计算技术在使用过程中的换页开销和系统I/O性能,针对键值数据的查询与更新操作,文章基于SGX1技术实现基于机密计算的键值数据存储与操作优化方法。该方法将高频查询的键值数据以明文形式存储在TEE的最小堆中,主要数据结构以密文哈希表形式存储在不受保护的主内存中,在利用TEE优化热数据查询操作时,利用数据标签优化主内存中冷数据的查询与更新操作。实验结果表明,与直接对键值数据进行加解密以实现查询与更新的方法相比,该方法效率更高,能够有效避免换页开销并提升系统的I/O性能。
中图分类号:
引用本文
任丰原, 张馨月, 雷卓祎, 刘忻. 基于机密计算的键值数据存储与操作优化方法研究[J]. 信息网络安全, 2025, 25(11): 1707-1717.
REN Fengyuan, ZHANG Xinyue, LEI Zhuoyi, LIU Xin. Research on Key-Value Data Storage and Operation Optimization Method Based on Confidential Computing[J]. Netinfo Security, 2025, 25(11): 1707-1717.
| [1] | ZHANG Fengwei, ZHOU Lei, ZHANG Yiming, et al. Trusted Execution Environment: Status and Prospects[J]. Journal of Computer Research and Development, 2024, 61(1): 243-260. |
| 张锋巍, 周雷, 张一鸣, 等. 可信执行环境:现状与展望[J]. 计算机研究与发展, 2024, 61(1):243-260. | |
| [2] | SHANG Ketong, LU Fang, HUANG Ke, et al. Cluster Nodes Integrity Attestation and Monitoring Scheme for Confidential Computing Platform[C]// IEEE. The 22nd International Conference on Trust, Security and Privacy in Computing and Communications(TrustCom). New York: IEEE, 2023: 740-749. |
| [3] | XU Tao, KONG Shuaidi, LIU Caihua, et al. Overview of Heterogeneous Confidential Computing[J]. Journal of Jilin University(Engineering and Technology Edition), 2025, 55(3):755-770. |
| 徐涛, 孔帅迪, 刘才华, 等. 异构机密计算综述[J]. 吉林大学学报(工学版), 2025, 55(3):755-770. | |
| [4] | LI Zhiang, MASHIMA D, ONG W S, et al. On Practicality of Using ARM TrustZone Trusted Execution Environment for Securing Programmable Logic Controllers[C]// ACM. The 19th ACM Asia Conference on Computer and Communications Security. New York: ACM, 2024: 947-961. |
| [5] | SCHUNTER M. Intel Software Guard Extensions: Introduction and Open Research Challenges[EB/OL]. (2016-10-28)[2025-07-10]. https://doi.org/10.1145/2995306.299530. |
| [6] | COSTAN V, DEVADAS S. Intel SGX Explained[D]. Cambridge: Massachusetts Institute of Technology, 2016. |
| [7] | LI Wei, FENG Wei, QIN Yu, et al. Scheme of Runtime Monitoring in Confidential Computing with Dynamic Integrity Measurement[J]. Journal of Computer Research and Development, 2024, 61(10): 2482-2500. |
| 李为, 冯伟, 秦宇, 等. 基于动态完整性度量的机密计算运行时监控方案[J]. 计算机研究与发展, 2024, 61(10):2482-2500. | |
| [8] | FENG Erhu, LU Xu, DU Dong, et al. Scalable Memory Protection in the PENGLAI Enclave[C]// USENIX. The 15th USENIX Symposium on Operating Systems Design and Implementation(OSDI 21). Berkely: USENIX, 2021: 275-294. |
| [9] | YANG Zuoru, LI Jingwei, LEE P P. Secure and Lightweight Deduplicated Storage via Shielded Deduplication-Before-Encryption[C]// USENIX. 2022 USENIX Annual Technical Conference(USENIX ATC 22). Berkeley: USENIX, 2022: 37-52. |
| [10] |
HA Guanxiong, GE Xiaowei, JIA Chunfu, et al. Revisiting SGX-Based Encrypted Deduplication via PoW-Before-Encryption and Eliminating Redundant Computations[J]. IEEE Transactions on Dependable and Secure Computing, 2025, 22(3): 2037-2053.
doi: 10.1109/TDSC.2024.3476288 URL |
| [11] | LUTSCH A, EL-HINDI M, HEINRICH M, et al. Benchmarking Analytical Query Processing in Intel SGXv2[C]// OpenProceedings. The 28th International Conference on Extending Database Technology(EDBT 2025). Barcelona: OpenProceedings, 2025: 516-528. |
| [12] |
PANDITH O S. SGXFault: An Efficient Page Fault Handling Mechanism for SGX Enclaves[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 21(3): 1173-1178.
doi: 10.1109/TDSC.2023.3268169 URL |
| [13] | PARK J, KANG S, LEE S, et al. Hardware-Hardened Sandbox Enclaves for Trusted Serverless Computing[J]. ACM Transactions on Architecture and Code Optimization, 2024, 21(1): 1-25. |
| [14] | ASLANTAS B, PEKTAS E, BAYDERE S. Distributed Key Value Store for IoT Edge Devices[C]// IEEE. The 9th International Conference on Computer Science and Engineering(UBMK). New York: IEEE, 2024: 1-6. |
| [15] | CHEN Shanshan, MA Zhenyu, GAO Jun, et al. HSKV: A Key-Value Storage Scheme Using Hash to Reduce Write Pause[C]// IEEE. 3rd International Conference on Frontiers Technology of Information and Computer(ICFTIC). New York: IEEE, 2021: 453-456. |
| [16] | RAHMAN M H, AL ABID F B, ZAMAN M N, et al. Optimizing and Enhancing Performance of Database Engine Using Data Clustering Technique[C]// IEEE. 2015 International Conference on Advances in Electrical Engineering(ICAEE). New York: IEEE, 2015: 198-201. |
| [17] | LI Dewen, HUANG Wenjun, LI Long. Design of Real-Time Database for Industrial Control System[C]// IEEE. The 10th IEEE International Conference on Control and Automation(ICCA). New York: IEEE, 2013: 12-14. |
| [18] | MESSAOUD A A, MOKHTAR S B, SIMONET-BOULOGNE A. TruShare: Confidential Key-Value Store for Untrusted Environments[C]// IEEE. The 20th IEEE European Dependable Computing Conference(EDCC). New York: IEEE, 2025: 1-9. |
| [19] | SHEN Chenkai, FAN Lei. PLDB: Protecting LSM-Based Key-Value Store Using Trusted Execution Environment[C]// IEEE. The 22nd International Conference on Trust, Security and Privacy in Computing and Communications(TrustCom). New York: IEEE, 2023: 762-771. |
| [20] | LU Jinkang, XIE Pping. HotKey-Cache: A HotKey-Separate Cache to Improve Performance for Key-Value Store[C]// IEEE. The 2nd IEEE International Conference on Cloud Computing, Big Data Applications and Software Engineering(CBASE). New York: IEEE, 2023: 286-290. |
| [21] | NAM H, PARK J, LEE S, et al. Hints for Memory Optimization of Asylo-Based SGX Enclave Applications[C]// IEEE. 2020 International Conference on Information and Communication Technology Convergence(ICTC). New York: IEEE, 2020: 1685-1690. |
| [22] | LEE J, SON S, BAE J, et al. SkipLSM: Fast Retrieval of Hot Key-Value Pairs on LSM Tree[C]// ACM. The 40th ACM/SIGAPP Symposium on Applied Computing. New York: ACM, 2025: 396-405. |
| [23] | KOO J, BAE J, YUK M, et al. All-Flash Array Key-Value Cache for Large Objects[C]// ACM. The 18th European Conference on Computer Systems. New York: ACM, 2023: 784-799. |
| [24] | JOHNSON S, MAKARAM R, SANTONI A, et al. Supporting Intel® SGX on Multi-Socket Platforms[R]. Santa Clara: Intel Corporation, 843058, 2021. |
| [25] | HUANG Jianming, YU Hua. Root Crash Consistency of SGX-Style Integrity Trees in Secure Non-Volatile Memory Systems[C]// IEEE. 2023 IEEE International Symposium on High-Performance Computer Architecture(HPCA). New York: IEEE, 2023: 152-164. |
| [26] |
LI Mingyu, XIA Yubin, CHEN Haibo. Memory Optimization System for SGXv2 Trusted Execution Environment[J]. International Journal of Software and Informatics, 2022, 12(3): 285-307.
doi: 10.21655/ijsi.1673-7288.00287 URL |
| [27] | TRAMÈR F, BONEH D. Slalom: Fast, Verifiable and Private Execution of Neural Networks in Trusted Hardware[EB/OL]. (2019-02-27)[2025-07-10]. https://doi.org/10.48550/arXiv.1806.03287. |
| [28] | KIM T, PARK J, WOO J, et al. ShieldStore: Shielded In-Memory Key-Value Storage with SGX[C]// ACM. The 14th EuroSys Conference 2019. New York: ACM, 2019: 1-15. |
| [1] | 朱辉, 方云依, 王枫为, 许伟. 融合机密计算的数据安全处理研究进展[J]. 信息网络安全, 2025, 25(11): 1643-1657. |
| [2] | 郝萌, 李佳勇, 杨洪伟, 张伟哲. 异构CPU-GPU系统机密计算综述[J]. 信息网络安全, 2025, 25(11): 1658-1672. |
| [3] | 卢笛, 刘玉佳, 吕超越, 孙梦娜, 张清文, 杨力. 一种云原生TEE服务共享机制[J]. 信息网络安全, 2025, 25(11): 1774-1791. |
| [4] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [5] | 刘忻, 李韵宜, 王淼. 一种基于机密计算的联邦学习节点轻量级身份认证协议[J]. 信息网络安全, 2022, 22(7): 37-45. |
| [6] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [7] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [8] | 刘忻, 郭振斌, 宋宇宸. 一种基于SGX的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(6): 1-10. |
| [9] | 冯达, 王强, 赵译文, 徐剑. 基于SGX的证书可信性验证与软件安全签发系统[J]. 信息网络安全, 2018, 18(3): 63-69. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||